Woodlake Unified District in California includes Castle Rock Elementary, Francis J. White Learning Center, Woodlake Educational Options Program, Woodlake Union High School, and Woodlake Valley Middle School. On April 11, the district took to Facebook to alert the community to a ransomware incident that occurred on April 9.
 |
 |
| Image: DataBreaches.net |
For months, the breach did not show up anywhere, but on September 13, Pysa threat actors added it to their leak site, noting the incident as April 8.
As they tend to do, Pysa dumped a lot of data. In this case, the data dump seemingly should have contained 77 parts that included more than 16 GB of files, compressed. Some parts seem to have been omitted from the dump, however, raising questions and concerns as to what might be in the parts that were not dumped.
The files that were dumped contained a lot of personal and sensitive information of students and employees. The following sections describe just some of what DataBreaches.net found in plain text files available to anyone and everyone.
All redactions in the images in this report were performed by DataBreaches.net.
Student-Related Files
We found files containing the names and surnames of the students with their date of birth and social security numbers. Some spreadsheets contained students’ email addresses and passwords.
In one folder, we found dozens of special education student files. These files contained the name of the teacher, the class, the date and the name of the student with other special education-related information for the students.
In other files, we found scholarship applications containing photos of the students with their personal, family and educational information.
Not all data was for current students. We found older files as well, including disciplinary files such as expulsion records. We also found files with a student transcript, course rosters, and we saw expulsion notes from several years ago, we saw student grades and other education records, including Behavior Intervention Plans (BIPs) for students with disruptive behaviors, and IFSPs (Individualized Family Service Plans) for pre-school children. As with Individualized Education Programs (IEPs), IFSPs often contain personal and family background information and social and medical history.

There were hundreds of files on individual students of various kinds, but all should have been protected under FERPA, the federal law protecting the privacy of, and disclosure of, education records.

One of the exposed files had a complete history of a child in foster care. For such children, their medical records and education records are updated by current foster parents and providers so that the next foster placement will have current and accurate records of medical issues and educational needs and services. The document is referred to as a “passport” because it travels with the student.
Personnel-Related Files
In some folders we found tax-related or payroll-related information. Some files had employees’ names with social security numbers as well as other personally identifiable information. We also found some personnel issues such as complaints about individuals or investigations.
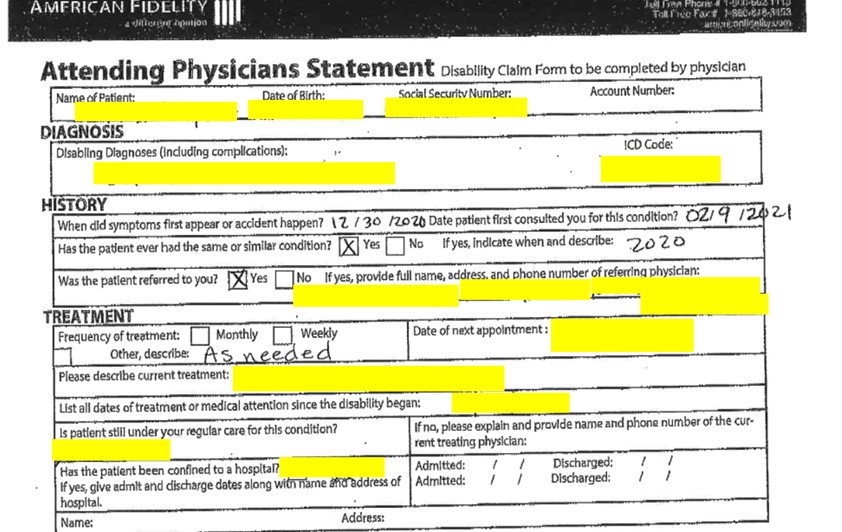
Information on employees from the 2018-2019 and 2019-2020 included injury status reports with fields like: Employee Name, Social Security Name, Date of Birth, Address, Phone, Gender, Job Title, Date of Injury, Time, Specific Injury, Supervisors Comments. In other files, there were medical reports related to claims such as physician statements and disability forms.
Other files had school personnel’s usernames and passwords.
What Wasn’t in the Data Dump
While there was a lot of data in the dump and this report only gives some examples without the full scope of the breach, what we didn’t find was master payroll systems or systems with direct deposit or other financial information on employees. Nor did we find master education records systems including enrollment. Did Pysa acquire those files and decide not to dump them but to sell them or misuse them — or did they not acquire them at all? DataBreaches.net does not know.
Woodlake’s Response
Because DataBreaches.net could find no updated notification on Woodlake’s site, we reached out to the district’s Superintendent, Laura Gonzalez, to ask if the district had sent individual notifications to employees and parents of students, and if so, how many people had been notified.
The superintendent did not respond to our first email, but did respond to our second request with:
“No comment.”
We have found no update on their web site, and we have found no report to the California Attorney General’s Office. Has the district notified anyone? We do not know, but will update this post if more information becomes available. But it has been six months now since the district was attacked and data exfiltrated. Should there have been some public disclosure? Does “no comment” really serve the public well?
Pysa Continues Attacks on Schools
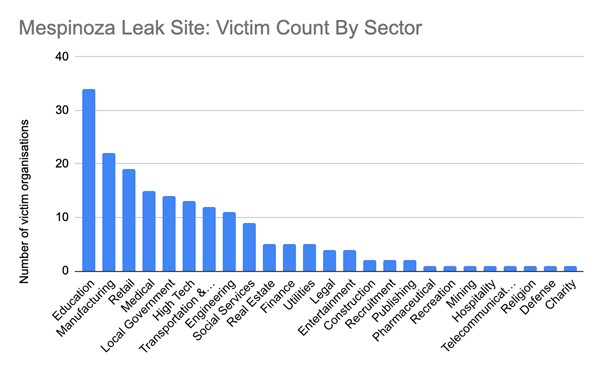
DataBreaches.net has reported on a number of other education sector attacks by Pysa threat actors. This is now the 12th k-12 report this site has published.
Unit 42’s cybersecurity consultants have observed that the education sector is the most affected by the Pysa criminal gang.
If you have been affected by this breach or have received a notification from the district, please email chum1ngo[at]databreaches[dot]net
Research and reporting by chum1ng0, with additional material and editing by Dissent.