This is not be the first time the Texas Department of Transportation (TxDOT) has apparently had a data security incident, and it certainly not the largest breach the state has ever experienced, but it appears that TxDOT’s portal for the certified payroll system for contractors has been hacked.
Two posts by one individual appeared over the weekend on a hacking-related forum.
The first post included a screencap of an employee’s setup with the employee’s personal information, including SSN. The forum post also included login credentials and the url for the state’s contractor’s payment system. For ethical and legal reasons, DataBreaches did not test the login credentials.

The second post included a screencap showing listings of a contractor’s projects. A second screencap in the post contained another employee’s setup screen with their personal information.
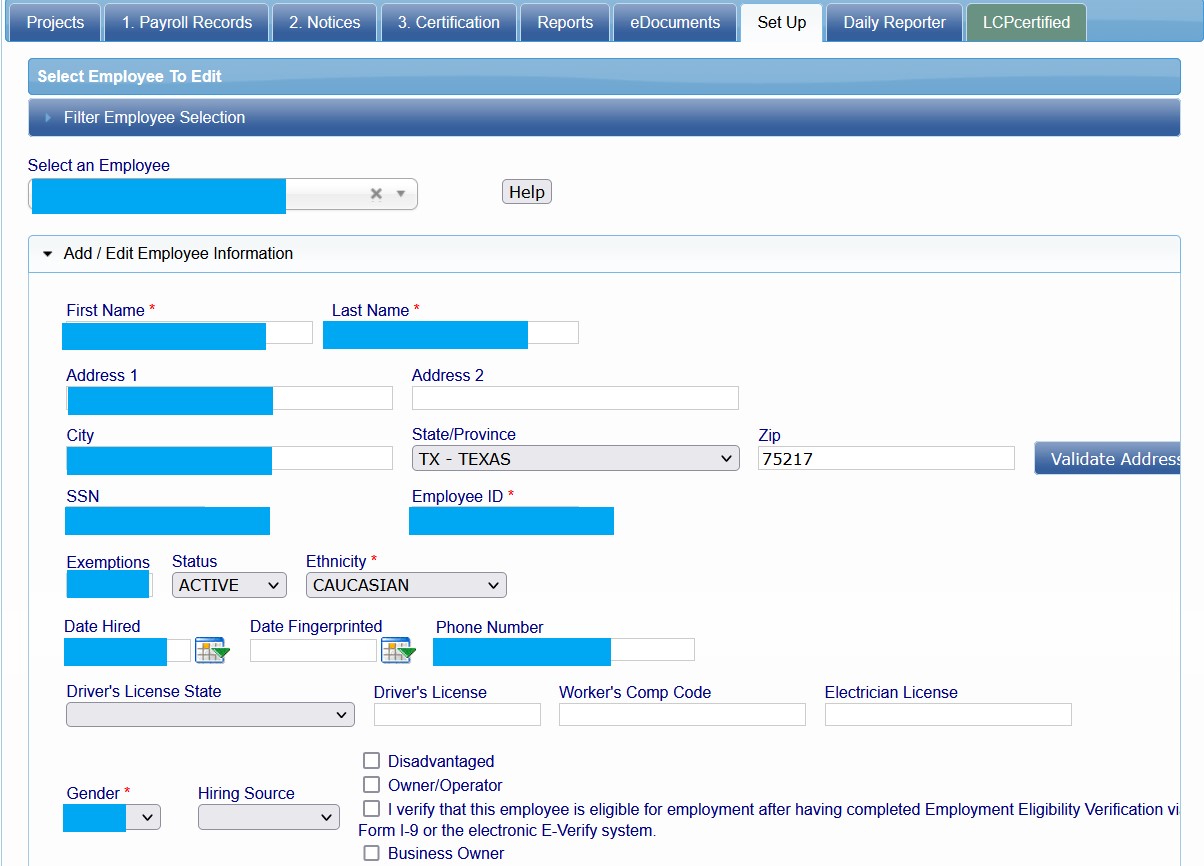
An example of an employee’s set up shows the types of personal information in these files.
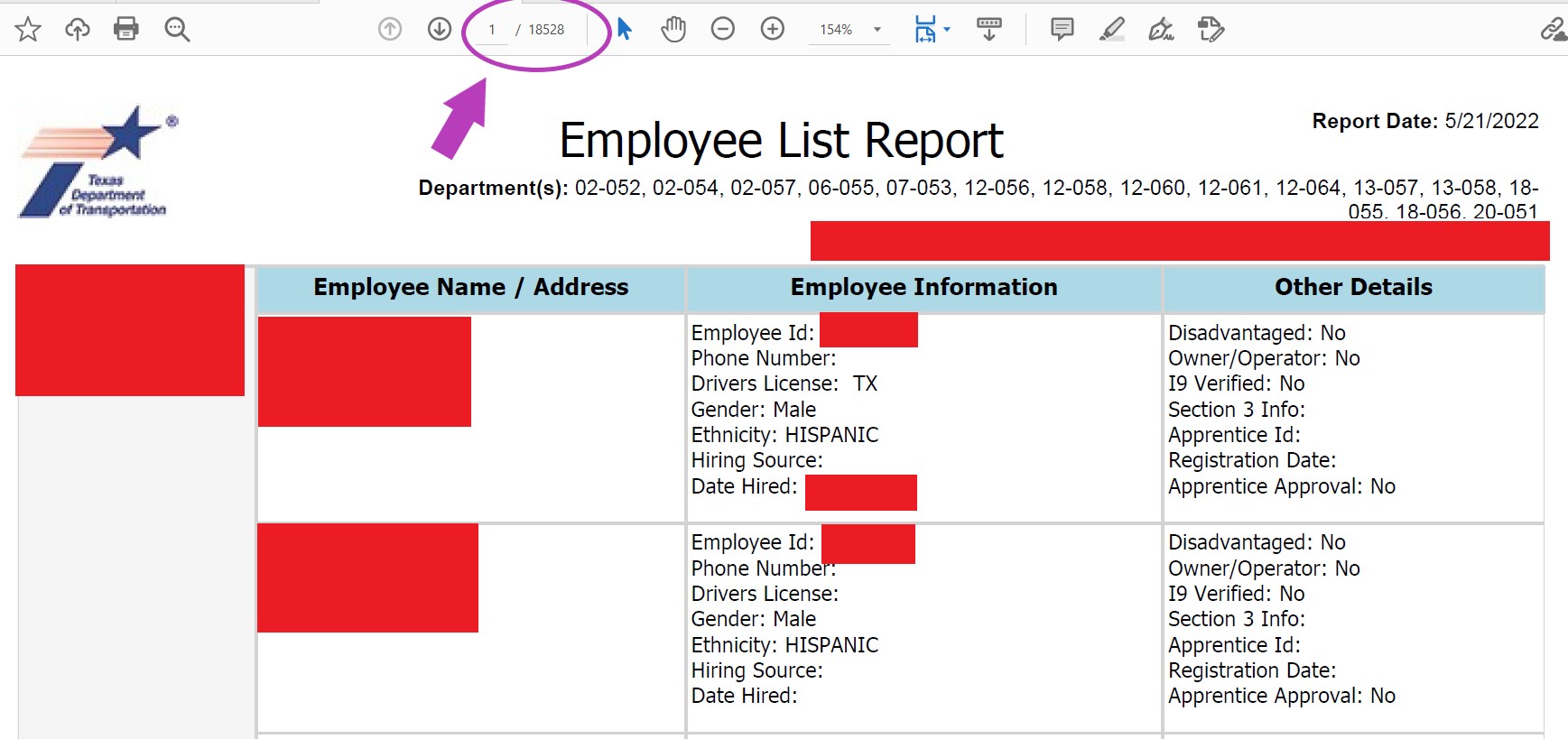
DataBreaches.net was contacted about the posts by someone who informed this site that the person or persons responsible for the hack had acquired more than 7,000 individuals’ records. They provided DataBreaches with two pdf files in addition to the screencaps in the posts. While the two “Employee List Report” pdf files did not contain SSN’s, one of the files — an employee list report for a named contractor — consisted of more than 18,000 pages with multiple employees listed on each page.
According to the individual, data will be up for sale soon. They did not indicate how soon, but when asked, stated that the individual or individuals involved had not contacted TxDOT to try to extort any payment to not leak or sell the data.
The person(s) who did this is/are “not animals,” they told DataBreaches, and do not do anything for money or extortion. “Just for publicity and show that they have bad security,” they said. “We are all human and still have morals. I would not want to be extorted for money. Would you?” they asked DataBreaches.
Well, no. But so how do they justify selling the data?. They responded to that question:
Extortion is just wrong.
Like blackmail.But sold as not much you can do with ssn anyway.
To do anything real harmful you need photo of ssn and photo of ID
At another point in the chat, when DataBreaches asked how they had gained access, they replied that it was a brute force attack.
DataBreaches sent an email Sunday evening to the Texas Department of Transportation media relations to ask them about the claimed incident and to provide them with the urls where they could find the listings and screencaps. DataBreaches also sent a direct message to the TxDOT Twitter team to alert them to the breach and to the email sent to their media relations department. Early Monday morning, DataBreaches called TxDOT and left a message for their cybersecurity department saying that they appear to have been hacked. The message included this site’s phone number.
DataBreaches also reached out to Ragle, Inc., a highway and bridge construction firm with offices in Indiana and Texas. Ragle had reportedly been recently attacked by the Black Basta ransomware team, and Ragle’s corporate and personnel data had been dumped on Black Basta’s dark web leak site on or about April 28. Now it appeared that some of Ragle’s data, including its employees’ payroll-related data, may have been compromised in the attack on TxDOT. Whether the Ragle data was some of the same data leaked by Black Basta is unknown to DataBreaches.
As of the time of this publication, TxDOT has not responded to this site’s inquiries or notification attempts. Nor has Ragle Inc. responded. Because DataBreaches cannot test the login credentials, this site does not know if they still work or if the state has already changed those credentials.
This post will be updated if a reply is received or if there are more developments.