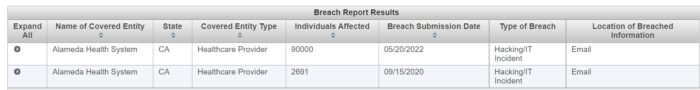
On June 24, Alameda Health System in California submitted a notification to the California Attorney General’s Office. The notification concerned a breach of an employee’s email account breach that began on April 30, 2020. The breach wasn’t discovered until February 23, 2022, and the account was locked down after that in March.
According to Alameda’s notification, the types of information involved varied by individual but included: name, date of birth, patient ID, clinical or treatment information, health insurance or claims information, Social Security number, and driver’s license number.
But it is not clear to DataBreaches whether Alameda had just forgotten to notify California or if something else happened, because in May, Alameda had already notified HHS of that incident, and had reported that 90,000 patients had been affected.
Earlier Incident
The June 2022 notification appears to be unrelated to a September 2020 notification by Alameda in which they also reported compromise of an employee’s email account. In that earlier case, Alameda reported that on June 17, 2020, they learned that, “for a brief period of time on April 8, 2020, an unauthorized person from outside AHS was able to remotely access the email account of an AHS employee.” They then “launched an investigation and engaged a leading forensic security firm to assist in our investigation.”
So a leading forensic firm and investigation never detected that another employee email account had been compromised on April 30 or May 1 — just weeks after the known April 8 compromise — and was still compromised at all times during their investigation?
The April 8, 2020 incident reportedly impacted 2,691 patients.
NOTE: DataBreaches.net has seen some sites claiming that the 90,000 breach occurred on April 8 and was discovered June 17 of 2020. No. There were two different breach incidents reported by Alameda Health System.