Two medical entities appear to have recently fallen prey to attacks using BlackByte’s ransomware, and both entities have now had some of their data leaked on BlackByte’s dedicated leak site.
Lamoille Health Partners
Lamoille Health Partners in Vermont serves the Lamoille County community’s healthcare needs. As such, they provide a range of comprehensive services that include dentistry, family medicine, pediatrics, addiction treatment, mail-order pharmacy services, and mental health and substance use treatment.
In its data leak, BlackByte included two folders, each with a different employee’s name as the folder name. One folder contained mostly accounting-related or billing-relating files but there was still some protected health information there where patient names were listed in tracking billings. There were also a number of files with employee data, especially related to payroll/wages.
The other folder contained a lot more sensitive information on patients. As one example, DataBreaches saw letters that provided the patients’ names, dates of birth, SSN, and their medical issues/disability and need for specified accommodations or services.

There is no notice on Lamoille’s website, nor on the Vermont Attorney General’s website for breach reports. DataBreaches emailed Lamoille yesterday to ask whether they had made any notifications and whether patient care had been impacted by the breach. No reply has been received.
Gateway Rehab
Gateway Rehab provides services in western Pennsylvania and Ohio. BlackByte leaked more than 4 GB of their data already. The leaked data contain numerous internal business documents, including accounts receivable and payable. There are also spread sheets with information on named patients, and hundreds of older files that include personal and sensitive information on people enrolled in community treatment programs.
Some forms that DataBreaches found in the leak are state of Pennsylvania “Extraordinary Occurrence” report forms that identify people who have absconded from a community treatment program run by Gateway Rehab. These reports appear to be from 2001-2005 and include sensitive and personal information on people such as their arrest records and history including behavioral issues and substance-related issues. Other old reports included re-classification recommendations.
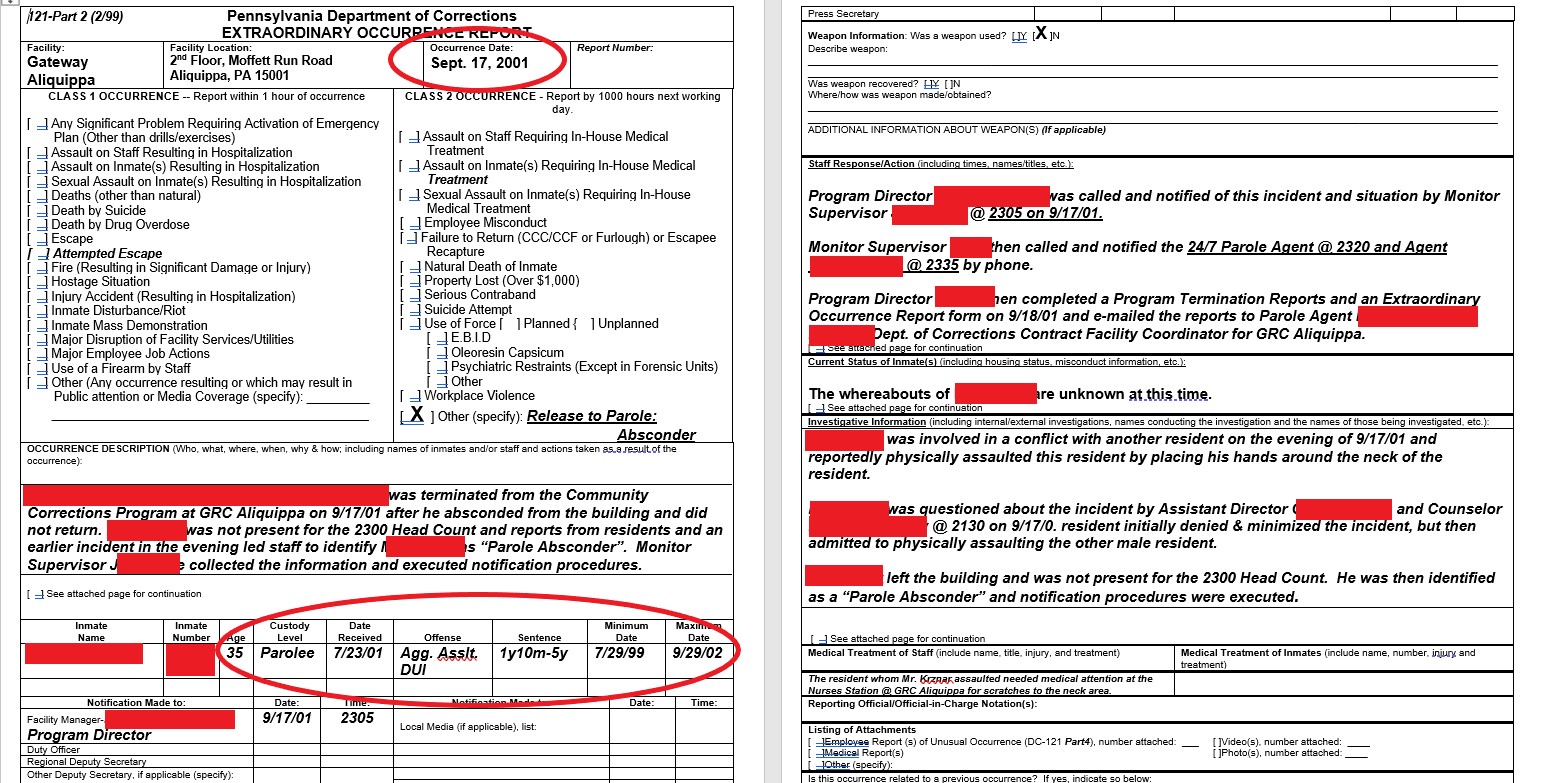
DataBreaches noted that there were hundreds of old files on named individuals with “extraordinary occurrence” reports or program termination reports.

Gateway Rehab’s website has links for privacy, HIPAA, and data security that link externally to Treatspace.
Treatspace’s data security policy page does not appear to have been updated since March, 2015. Their policy states, in part:
All users of the system have a login / password that limits access to only their specific user data or organizational-level data. All data submitted on the website is sent / received using Secure Socket Layer (SSL) technology to connect to the Treatspace servers. Specifically, upon submission of the form data, Transmit Layer Security (TLS) using an Advanced Encryption Standard (AES) connection is used to transmit the data to Treatspace servers. When the data arrives, the user sending the data is authenticated to ensure they are authorized to submit the data based on their login credentials which are granted by Treatspace when the account is established. All data at rest is encrypted. All access to data is logged. All data is backed-up and encrypted on a regular basis.
To protect any data you store on our servers, we also regularly monitor our system for possible vulnerabilities and attacks.
DataBreaches sent an inquiry to Treatspace yesterday asking if they were responsible for the security of all these files or if Gateway Rehab was. No reply has been received as yet.
What Next?
BlackByte reportedly follows the double extortion model. They have been around since mid-2021, and Palo Alto Networks, Cisco Talos, and Juniper Networks are among the firms who have recently published reports and analyses.
Based on their past behavior, it is likely that when the countdown clocks run out on Lamoille Health Partners and Gateway Rehab in about 18 days, more data will be leaked. DataBreaches reached out to BlackByte to ask them to confirm that that is still their current model, and they replied:
As you already understand, every company must protect its own data from outside parties, especially companies like these 2 that you indicated. A company that does nothing to protect the data, and even more, the data of its customers, cannot be called non-profit. What for are they getting money for then? Our company conducted this audit and offered a favorable price for correcting their mistakes. As it turned out, they would prefer to receive a fine from the state for not being able to protect confidential data.
and ofc when the timer will end another pack of their data will be posted.
DataBreaches will not speculate about whether either state would actually fine these entities, but HHS automatically investigates all reports, so if and when these incidents are reported to HHS, HHS should investigate. Hopefully, HHS investigators will take a close look at Gateway Rehab’s security to determine if it complies with the Security Rule.
Update of July 11: WCAX got a statement from Lamoille. As part of their coverage, they report:
As of right now, it’s still unclear whether or not Lamoille Health’s servers were purposely attacked or if the suspicious activity was the result of something like malware or a virus.
May admits they haven’t told patients about the breach and he doesn’t know when they will.
“Once we reach that point where we feel like we have more information to share, we will of course do that at that time along with any state or federal requirements of reporting these types of breaches,” May said.
Lamoille Health Partners is notifying all involved individuals for whom it has a valid mailing address and has arranged for complimentary identity protection and credit monitoring services for those individuals whose Social Security numbers were potentially involved.