It’s been more than a decade since DataBreaches covered any significant data breach involving the Aloha POS system, and back then it was owned by Radiant Systems. In 2011, NCR Corporation bought Aloha POS. Things were fairly quiet since then, if you don’t count NCR’s response to a zero day RCE vulnerability that NCR somewhat punted to its clients.
But now Aloha POS was back in RSS feeds this week as people tried to understand an outage that NCR really wasn’t explaining.
 As with all things, however, there was an explanation. And it involves the BlackCat ransomware group.
As with all things, however, there was an explanation. And it involves the BlackCat ransomware group.
Both eCrime.ch‘s tracker and Dominic Alvieri detected a short-lived post on BlackCat’s leak site. eCrime.ch alerted DataBreaches that their tracker had detected the post at 2023-04-15 07:20:44 UTC and that it was last seen at 2023-04-15 08:20:25 UTC. The timestamp on BlackCat’s leak site showed it first appeared at Sat 15 April 2023 07:17:05.910 UTC.
According to eCrime.ch, BlackCat’s post read:

During four days of silence and removal of any mention of ransomware on reddit, NCR representatives went into a chat room to find out what data had been stolen. After receiving information that NCR data had not been stolen, but accessed their customers’ networks, they decided to make a press release. We are forced to take action regarding NCR customers. If you become our victim you know who to thank.
Alvieri also posted what appears to be a chat log snippet between BlackCat and NCR:
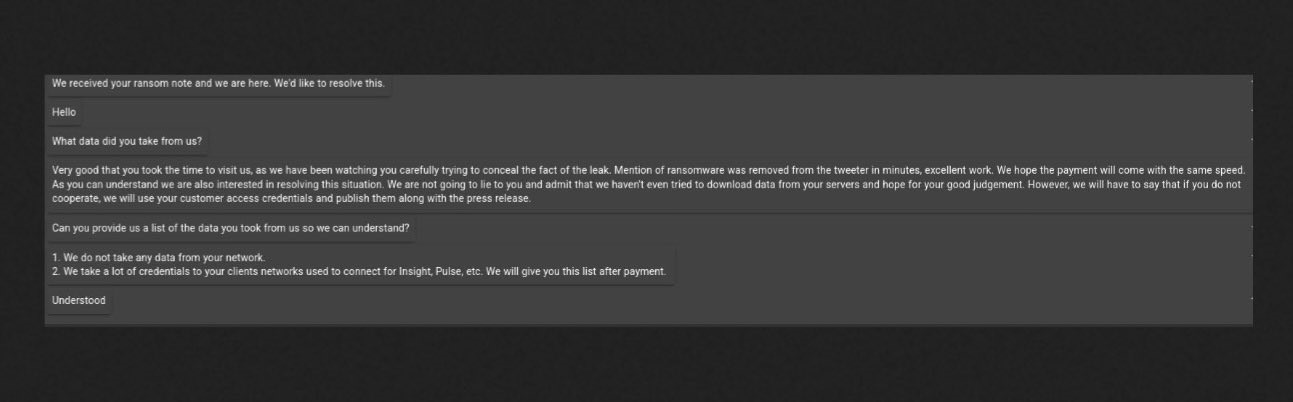
In the chat, NCR learned that it wasn’t their data that had been stolen, but their customers’ networks had allegedly been accessed.
Shortly thereafter, NCR posted an update on their outage status page about the DFW05 datacenter outage:
Update
As a valued customer of NCR Corporation, we are reaching out with additional information about a single data center outage that is impacting a limited number of ancillary Aloha applications for a subset of our hospitality customers. On April 13, we confirmed that the outage was the result of a ransomware incident. Immediately upon discovering this development we began contacting customers, engaged third-party cybersecurity experts and launched an investigation. Law enforcement has also been notified.Please rest assured that we have a clear path to recovery and we are executing against it. We are working around the clock to restore full service for our customers. In addition, we are providing our customers with dedicated assistance and workarounds to support their operations as we work toward full restoration. Restaurants impacted are still able to serve their customers. Only specific functionality is impaired. There is no impact to payment applications or on-premises systems.
The security and integrity of our systems is a top priority for NCR. We will continue to keep you updated with pertinent information and will let you know as soon as impacted services have been fully restored. In the meantime, please contact NCR Support or your Account Representative if you have any questions or need additional support.
We regret any concern this incident may cause. We appreciate your patience and support as we work toward full restoration.
This incident affects: North America (Aloha Insight-US, Aloha Keyless Licensing-US, Aloha Loyalty-US, Aloha Stored Value-US, Aloha Update-US, Command Center-US, Command Center WebOrder-US, Configuration Center-US, Configuration Center API-US, Customer Voice-US, Mobile Pay API-US, NCR Back Office (NBO)-US, Pulse Realtime-US, Pulse Realtime API-US, Radiant POS Management-US, Restaurant Guard Audit-US), Asia Pacific (Online Ordering Classic-APAC, Online Ordering API-APAC), and Europe (Online Ordering Classic-EU, Online Ordering API-EU).
BlackCat’s listing was removed one hour after it first appeared. Did NCR return to resume any negotiations? Will we see the listing again, or will there be no further word from BlackCat about this one?