In an update on Babuk’s site today, the threat actors write:
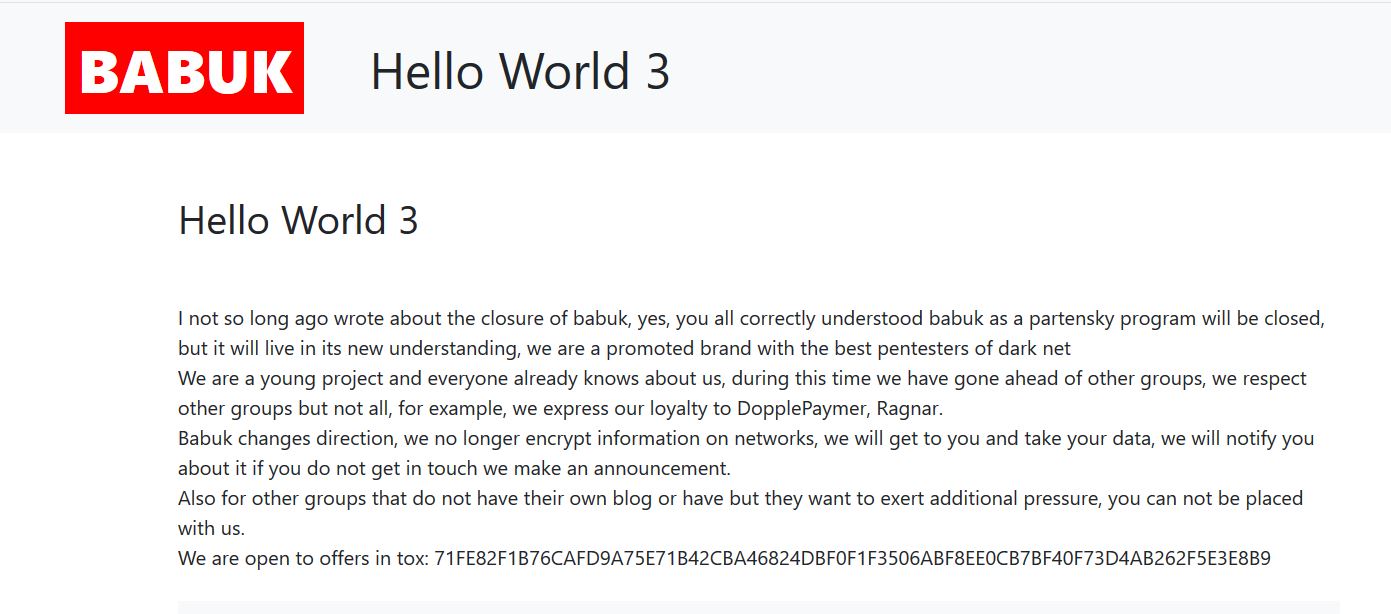
I not so long ago wrote about the closure of babuk, yes, you all correctly understood babuk as a partensky program will be closed, but it will live in its new understanding, we are a promoted brand with the best pentesters of dark net
We are a young project and everyone already knows about us, during this time we have gone ahead of other groups, we respect other groups but not all, for example, we express our loyalty to DopplePaymer, Ragnar.
Babuk changes direction, we no longer encrypt information on networks, we will get to you and take your data, we will notify you about it if you do not get in touch we make an announcement.
Also for other groups that do not have their own blog or have but they want to exert additional pressure, you can not be placed with us.
We are open to offers in tox:[deleted by DataBreaches.net]
In a previous chat with a Polish blogger, a Babuk spokesperson had indicated that after the Metropolitan Police Department of D.C., they would no longer attack state or government entities.
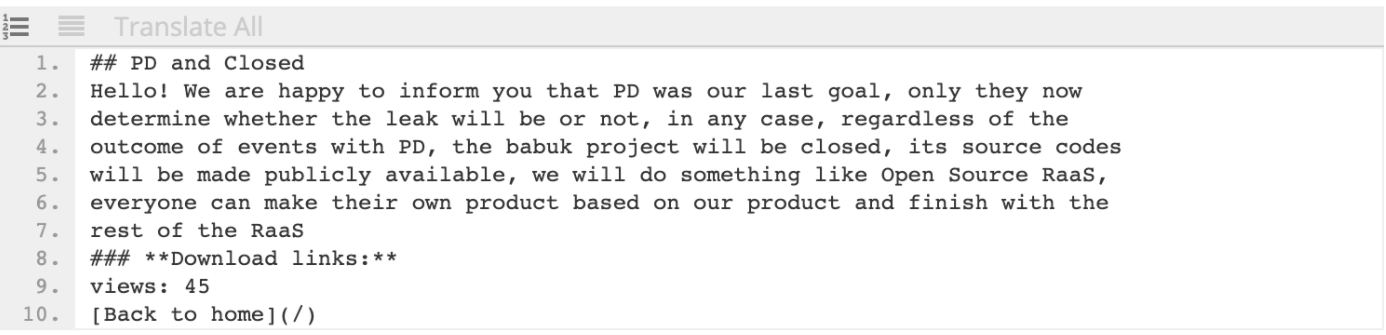
A screencap posted on a Russian-language forum yesterday from an unspecified source* seems to reiterate that they will no longer attack government entities, but also notes that their source code will be made publicly available, a development that they have been discussing in that forum since early March.
The outcome of the Metropolitan Police attack remains to be seen, Babuk had stated that they were in negotiations with the police department, but there has been no word from either party for the past two days. The police department’s listing is still removed from Babuk’s dedicated leak site, but the confidential files are still available online if one knows where to look.
In terms of their future, whether Babuk’s software will be popular remains to be seen. Emisoft had recently reported serious concerns about the quality of Babuk’s ransomware. On April 14, they wrote:
Unfortunately, the velocity at which they evolved their platform came at the cost of quality. As a result, there are multiple fundamental design flaws within both the encrypting and decrypting parts of Babuk on ESXi, which can result in permanent data loss.
One of the bugs within the actual Babuk ransomware on ESXi is that files can be encrypted multiple times. Multiple encryption layers are a nuisance, but ultimately just mean that with some manual effort a victim can still decrypt their data by simply decrypting the ransomed data again and again until all encryption layers have been removed.
That feedback and bad press seems to have concerned Babuk. In their recent interview with a Polish blogger, Babuk asked the blogger to get a message to Emisoft:
We want to convey a message to emisoft that we have fixed all the errors in our decoders, and would like to confirm this.
… you can see from a live example that the decryptor now works well (image linked from Babuk).
In the meantime, there are likely many police informants and police officers who may be anxious as to whether their personal information is about to be dumped on the dark web. DataBreaches.net will provide an update on that matter when more information is released.
*Update: Catalin Cimpanu had previously reported a Hello World 2 message from Babuk that was subsequently removed from Babuk’s site.