CO: SECOP II platform affected by “presumed hacking”
The SECOP II platform is a transactional platform with accounts for state entities and contractors used for submitting, evaluating, and awarding contracts. On May 3, La Agencia Nacional de Contratación Pública – Colombia Compra Eficiente reported a cyberattack on its SECOP II platform. The attack was announced on its Twitter account:
#Comunicado | Informamos a los usuarios del SECOP II que la plataforma ya se encuentra disponible, la interrupción de la infraestructura de la plataforma se presentó por presunto hackeo y se tomarán las medidas pertinentes.https://t.co/RbkLKZ2gyw pic.twitter.com/CIVXRusuoW
— Colombia Compra Eficiente (@colombiacompra) May 3, 2023
Machine Translation:
We inform SECOP II users that the platform is now available; the interruption of the platform’s infrastructure was caused by a presumed hacking and the pertinent measures will be taken.
In a May 5 update on Twitter, they tweeted:
We have worked constantly for the normalization of SECOP II operation. However, despite the activities carried out, there have been delays in some actions.
After the inconveniences presented in SECOP II, we have worked in coordination with the entities in charge of digital security and we are pleased to announce that the platform is now operating normally.
In an interview reported on Infobae, the deputy director of information and technology of Colombia Compra Eficiente said (machine translation):
The issue of information risks and cyber attacks are in the light of day and that is an issue that the National Government is contemplating in the National Development Plan, because in terms of cyber security there is no limit, any mitigation must be implemented by companies. Unfortunately risks cannot be eliminated: what we can do is to create opportunities for improvement to provide a better service and minimize the impacts that may affect Colombians.”
DataBreaches.net emailed SECOP on May 8 to request an update and to ask if users’ information had been compromised. On May 11, we received an acknowledgment of receipt of our email but have not received any substantive reply. The same day, however, they announced:
We inform that this Thursday, May 11, SECOP II presented intermittency.
At this moment the platform is now available and functioning normally.
Users complained, however, that the platform was not functioning normally that day.
On May 18, DataBreaches received a response to our email from William Renan Rodriguez, Secretary General. He wrote that the incident was under investigation, but he noted that information on the SECOP II platform is obfuscated with a specific hash.
There have been no further updates since then.
AR: INTA hit by ransomware attack
Instituto Nacional de Tecnologia Agropecuaria (INTA) is an Argentinean decentralized public agency under the Ministry of Agriculture and Fisheries of the Nation. It describes itself as contributing to the sustainable development of the agricultural, agri-food and agro-industrial sector through research and extension.
On May 2, INTA tweeted that it had suffered a computer attack:
Informamos que durante el fin de semana hemos detectado un ataque a nuestros servicios informáticos institucionales.
Desde ese momento, hemos activado los protocolos de seguridad.
— INTA (@intaargentina) May 2, 2023
In a series of tweets, it reported (machine translation):
We inform you that over the weekend we have detected an attack on our institutional IT services.
Since then, we have activated security protocols.
We are working together with specialists from information security companies and in close communication with the National Cybersecurity Directorate (@cert_Argentina) in accordance with the provisions of the current regulatory framework to solve the problem.
This attack is affecting our network of more than 400 points nationwide, which is why we have decided to suspend all institutional computer services until it is safe to move forward with their restoration.
We are focused on continuing with the recovery tasks to normalize the situation. We hope to be able to re-establish our services in a controlled manner as soon as possible.
Clarin reported that a letter the agency sent its employees called it a ransomware attack. “Now, to release the systems, the hackers would be demanding no more and no less than a sum of 2.5 million dollars,” the agency wrote.
This was not the first time that INTA had a ransomware attack. On March 15, 2022, Twitter user Mauro Eldritch reported an attack by the Everest group.
INTA has not disclosed what ransomware group or bad actor is responsible for the current attack and DataBreaches has not seen it listed on any leak site. INTA did not reply to a message from DataBreaches.net sent via Facebook on May 6 and their website contact page has not been operational.
BR: Logística Integrada Sulamericana Leaked by BlackCat
Brazilian logistics firm Logística Integrada Sulamericana (LISA) was added to BlackCat’s leak site on April 21. BlackCat provided 45 screenshots of various logistics company documents, including identity cards, as proof of their access to LISA.
BlackCat publicly threatened the firm:
“The company LISA LOGICTICA and its management were fully aware of the attack and the theft of sensitive data from their system. They had every opportunity to contact us to protect the personal and critical data of their customers and partners, but failed to do so, believing that their customers’ and partners’ data was nothing and could be sold to be used for criminal purposes.”

DataBreaches found no notice of any incident on the Logistic’s website or their social networks. Nor did they respond to DataBreaches’s email inquiries of April 21 and April 24.
CL: Updating: Medusa Leaks SONDA
DataBreaches recently reported a ransomware attack on Chile’s SONDA. On May 6, Medusa’s Telegram channel leaked SONDA’s data in 327 parts, each part being 3.8 GB.
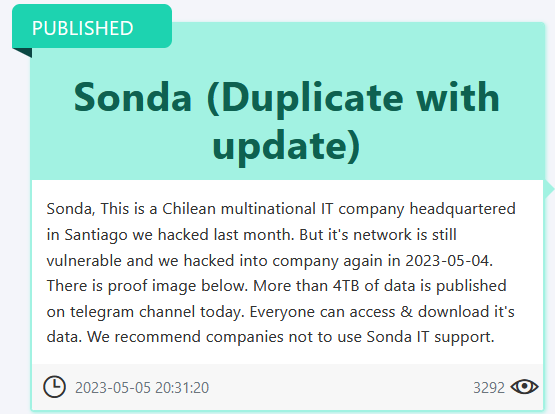
Inspection of some parts revealed the personal data of employees and suppliers. Databreaches.net confirmed that these data were valid by checking the names of current employees against other files with IDs, resumes, data sheets, and contracts.
DataBreaches does not know if SONDA has notified its employees that their data has been dumped on a free Telegram channel.
CL: Cooperativa de Ahorro y Crédito Ahorrocoop Ltda hit by Medusa
Cooperativa de Ahorro y Crédito Ahorrocoop Ltda (AhorroCoop) is a Chilean savings and credit cooperative with 7 branches in the country. The cooperative has more than 65,000 members nationwide. It was added to the Medusa Blog leak site on May 10. What appear to be internal documents from the cooperative were provided as proof.

Because there was no notice on their website, Databreaches.net emailed an executive of the company on May 10th and then again on May 15th, requesting more details. Neither email received a reply, so it is not clear whether the members of this cooperative have been notified that their personal data has been exposed.
Reporting by Chum1ng0, editing by Dissent