Updated May 13: It appears that Bluefield U. has not warned students that the university’s system is still compromised and that the threat actor can see and acquire files. Yesterday, a student that DataBreaches will not name submitted a Virginia Tuition Assistance Grant application with his full Social Security number, date of birth, and other personal information. Both he and his mother e-signed the application and dated it May 12, 2023.
DataBreaches just emailed the student to tell him that this site is looking at his application because the hacker got it and showed it to this site.

Students (and staff and faculty): Anything you submit to the university in the way of personal information is currently being seen and acquired by Avos Locker. If the school didn’t warn you about that, well, that’s between you and them, but think twice before you submit any personal or sensitive information to the school until the university manages to lock the hacker out of their systems. And so far, that hasn’t happened.
———————— original post follows:
On April 30, Bluefield University in Virginia discovered that they had been the victim of a cyberattack. They announced the attack to the community and that they had engaged cybersecurity experts to assist in their remediation efforts. At the time, they did not call it a ransomware attack and understandably, did not yet know the scope and extent of the attack.
Their attempts to reassure the community that they had no evidence of misuse of any information failed to reassure everyone, though — especially after the individual(s) responsible for the attack took control of the university’s RAMAlert system to blast out a message to students. On May 2, DataBreaches was contacted by a concerned employee who provided this site with a screencap of the May 1 alert message.
In response to the RAMAlert incident, the university posted an update on their update site that simply said, “Further, we discovered earlier today that the incident impacted our mass alert system, RAMAlert. As such if you are contacted by anyone claiming to be involved in the incident, please don’t click on any links provided by the individual or respond.” The update didn’t directly address the fact that the attacker(s) clearly had taken control of the system and what progress had been made by the university in kicking the attacker(s) out and locking them out.
By May 7, Avos Locker started leaking data and providing additional details to DataBreaches.
Now, 12 days after the discovery of the attack, it appears the attackers, who call themselves @Bluefield_Pentest[at]infosec.exchange, are still in Bluefield’s system.
As proof, and as first reported on infosec.exchange yesterday, they provided DataBreaches with an internal email sent by the Executive Assistant to the President that had been sent yesterday morning. The email invited other staff and faculty members to join the sender in prayer for the university’s leadership, IST team, and campus. Bluefield describes itself as a Christ-centered learning community.
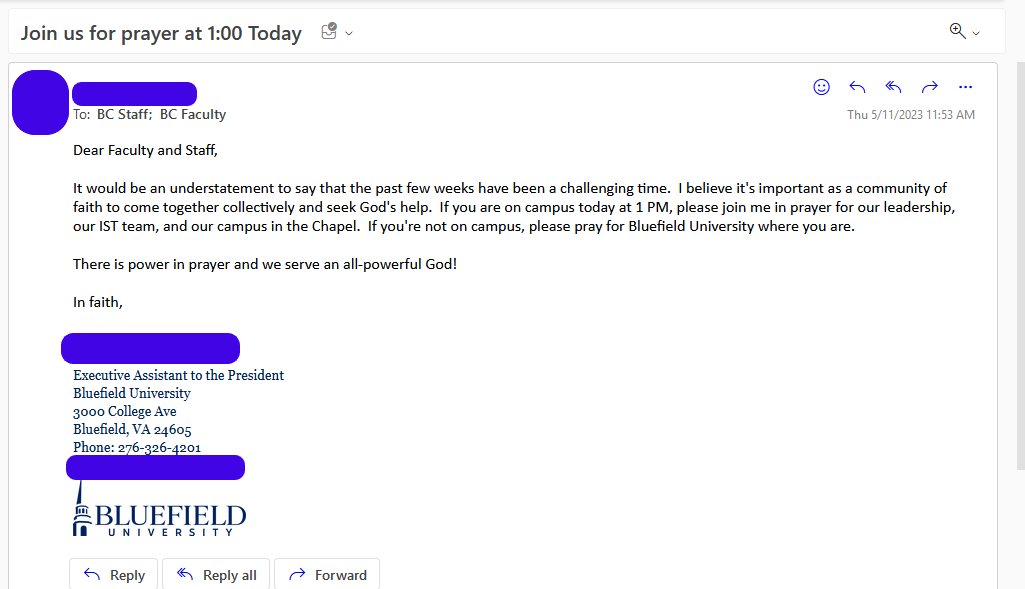
So @Bluefield_Pentest is allegedly still in their system and is monitoring their incident response, telling DataBreaches that the university paid $6000.00 for “threat actor communication,” which the threat actor noted was “basically sending us one message over 10 days.” After that May 5 message, the university did not attempt further communications. However, as of last night, after the attacker had taken control of the school’s Twitter account to post links to the leak samples, the school allegedly opened the chat window again and left it open. Whether they have said anything in the chat since then is unknown to DataBreaches, but the affiliate showed DataBreaches some of the communications between Bluefield and its lawyer(s) about the breach. DataBreaches is not reproducing those communications here.
In response to specific questions from DataBreaches, this site was provided with samples of data acquired by Bluefield_Pentest beyond the student transcripts and employee W-2 data that have already been leaked publicly. One file DataBreaches was given consists of 2222 pages of student transcripts from 2021.
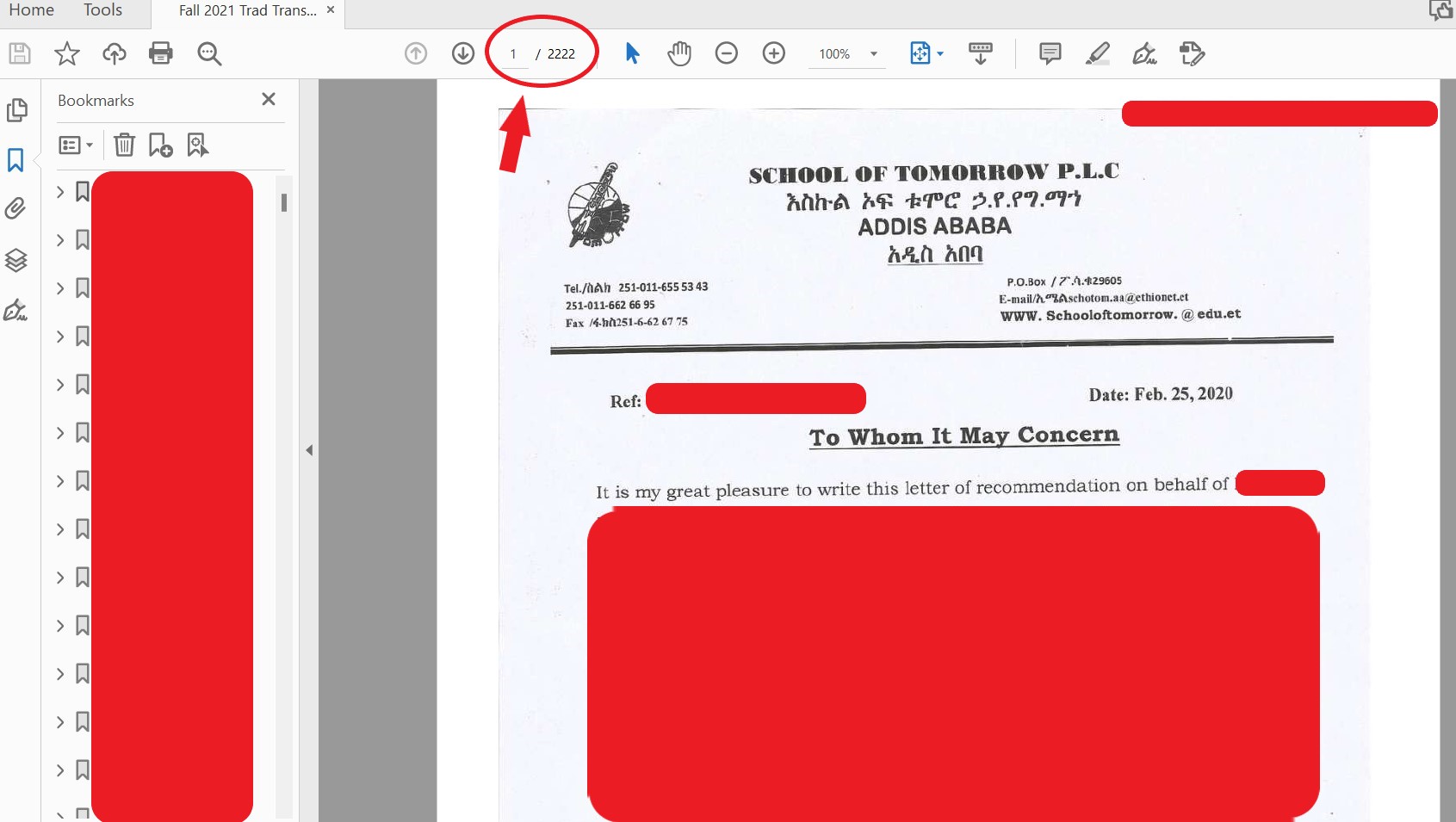
Student transcripts contain much personal information that can be used for identity theft, leaving a person more vulnerable to phishing attacks or fraud. The federal law protecting student education records (FERPA) does not require universities to notify each student individually if their data was in a breach of this kind. Still, it does require the school to make a note in the student’s record about any disclosure. Virginia state law, however, may require actual individual notification letters to those students whose full Social Security numbers with their names and other details were accessed and acquired. DataBreaches is not an expert on Virginia data breach law, but perhaps some lawyer will jump in and comment.
Of more concern in terms of sensitivity, the attacker(s) also acquired some student financial information related to federal student grant applications and state tuition assistance grants.
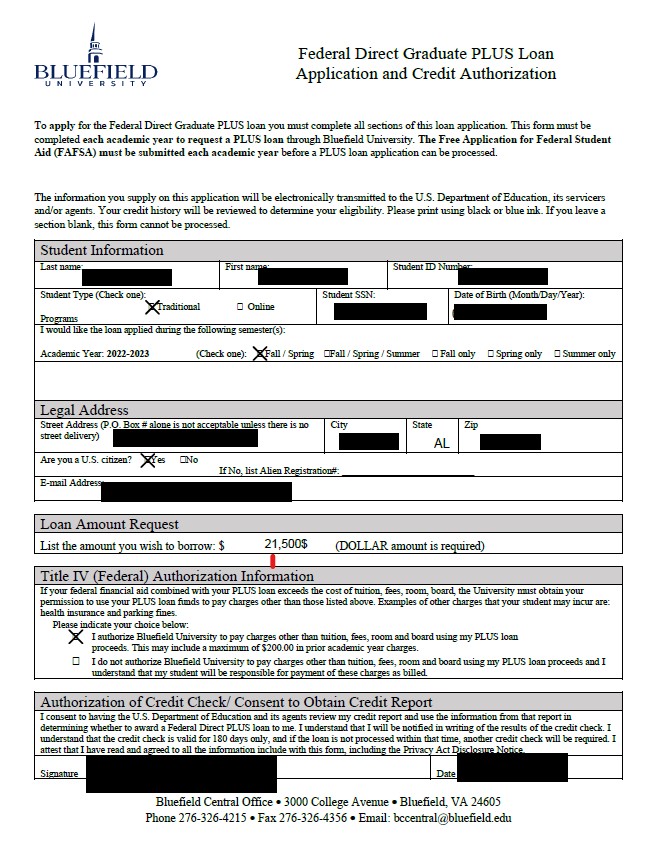

Some students applied for tuition assistance from the state, and DataBreaches saw some completed VTAG applications with student information including identity information and other details. The screencap below is just one section of a 4-page VTAG application shown to DataBreaches that was allegedly taken from Bluefield UniverUniversity’sr.

Both the federal financial aid-related (FASFA or Title IV) forms and the VTAG forms likely trigger notification requirements under either state laws or federal law like the Gramm-Leach Bliley Act (GLBA). DataBreaches does not know how many students had financial aid-related information accessed or acquired without authorization, but parents may also need to be notified because their name, address, phone number, employment, Social Security number, email address, and other information may have been compromised as well as their child’s.
DataBreaches emailed Bluefield University today to ask whether they had notified students and parents whose financial aid-related forms were exfiltrated, and whether they notified the faculty and staff whose W-2 records were both exfiltrated and leaked on the dark web already. No reply was immediately available, and DataBreaches suspects that the University does not have enough information compiled to notify individuals. But perhaps they should be updating their site to indicate that they know that the personal information of faculty and students has been acquired by Avos Locker, even if they don’t don’t know how much or all of the kinds of information. DataBreaches does not know what else Bluefield_Pentest acquired in the way of sensitive info. Were there files with disciplinary records on staff or students? Any health or health insurance-related records for named employees or students? So far, nothing like that has been leaked.
@Bluefield_Pentest informed DataBreaches they were demanding $1 million because that was the amount of the university’si cyberinsurance, but they would have been willing to negotiate.
These are challenging times for the university. Will students and faculty feel betrayed if the school doesn’t pay ransom to protect their personal and, in some cases, sensitive information when it has cyberinsurance that could cover the cost of the ransom? Maybe. Or maybe the students and faculty will want the university not to give in to extortion demands.
But there is one question that the university needs to address: should any employee or student give the university any personal information now if the university is still allegedly compromised? Will posting new grades at the end of the semester add to all the data the threat actors can exfiltrate? What about new loan applications? Should they be taken at this time?
This is not just a matter of cleaning up a breach that is over and done. As long as Avos Locker is in their system, this breach and its potential to do harm are not over.
Update:
After this was posted, Bluefield_Pentest posted something on infosec.exchange:
@jjdavis @brett @douglevin @PogoWasRight paying is cheaper for long-term and short-term costs in this attack. we’ve explained the payment for deleting data also provides the explanation of initial access and persistence. pretending this problem doesn’t exist won’t remove our presence in the network. Lying to students their data wasn’t exfiltrated when data was compromised is unjust, misleading false claim which we can provide proof. Security is an afterthought for this college – if they don’t receive an explanation from us directly how they’re hacked the shit “cyber expert forensics team” hired will never find us. 2 weeks after ransom note they’ve been unsuccessful. Perhaps firing the IST staff would help