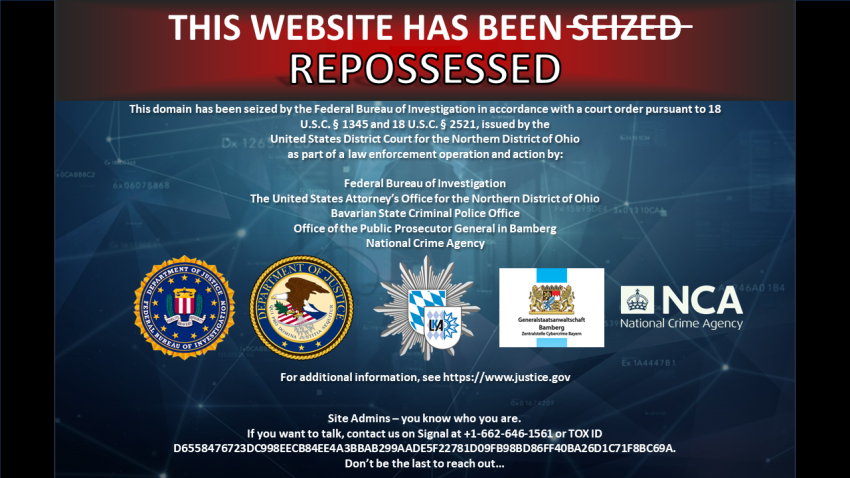
The following takedown and operation relate, in small part, to a leak DataBreaches reported to the FBI and a hosting company. DataBreaches did not name the victim entities or RADAR-DISPOSSESSOR in that blog post to prevent others from finding or misusing the victims’ data. The dispossessor.com website now displays a seizure notice, where the word…
Category: Malware
Surgery Center of Mid Florida notifies patients of February ransomware attack
On or about February 21, Surgery Center of Mid Florida (“SCOMF”) experienced a ransomware attack. No group has publicly claimed responsibility for the attack, but it originated with an attack on their now-former IT vendor. The attack on the unnamed vendor gave the attackers access to SCOMF. In August, SCOMF notified regulators, explaining, in part:…
Betances Health Center hit by ransomware attack; sensitive patient data leaked
On July 12, threat actors known as Hunters International added Betances Health Center in New York to their leak site. On July 25, they leaked what they claim is almost 125 GB of information consisting of 361,564 files. Betances Health Center describes itself as offering a full range of primary care and preventive services, as…
Security bugs in ransomware leak sites helped save six companies from paying hefty ransoms
Zack Whittaker reports: A security researcher says six companies were saved from having to pay potentially hefty ransom demands, in part thanks to rookie security flaws found in the web infrastructure used by the ransomware gangs themselves. Two companies received the decryption keys to unscramble their data without having to pay the cybercriminals a ransom,…
FBI Issues Warning As ‘Men In Black’ Hackers Demand $60 Million Ransom
Davey Winder reports: An updated advisory from the FBI and the Cybersecurity and Infrastructure Security Agency has warned of the danger from a ransomware group that has demanded as much as $60 million from its victims, and a staggering total of $500 million so far. The criminal hackers concerned have rebranded from calling themselves Royal…
UK: Provisional decision to impose £6m fine on software provider Advanced following 2022 ransomware attack
The following statement by the Information Commissioner’s Office concerns a devastating 2022 ransomware attack by LockBit3.0 on Advanced Computer Software Group (“Advanced”), an IT vendor for the UK’s National Health Service (NHS). Here is the ICO’s statement about Advanced: We have provisionally decided to fine Advanced Computer Software Group Ltd (Advanced) £6.09m, following an initial…