We’ve seen it before – in fact, we seem to be seeing it a lot recently – data from an old hack first being publicly leaked. This time it’s Bin Weevils, a British online children’s game, owned by 55 Pixels. 
In September 2014, Bin Weevils posted a note on their site that they had discovered a “vulnerability” affecting usernames and passwords. In response, they forced a password reset and added some unspecified security features. Their note does not seem to inform users that the data were actually hacked and acquired. And based on data provided to DataBreaches.net yesterday and today, they did not fully disclose the types of information that were hacked.
Yesterday, DataBreaches.net was contacted by “ShohidzIslam,” who wrote that he had learned of a database that was now being released to the public by hackers going by the names of “Pure”, “LukeBaxter”, “Akshay”, “Tyrone” and “Philip.” A link to the data had reportedly been posted in an IRC chat.
The file, which DataBreaches.net obtained and inspected, consisted of 1,022,883 records. Each record included the user’s username, encrypted password (salt+hash), and in-game data like their pet’s ID number, pet’s name, and date of registration. A line at the top of the dump credits “jkb, legit, lukebaxter, tyrone, philip, pure, akshay.”
ShohidzIslam informed DataBreaches.net that he asked the hackers if they also had IP addresses and email addresses. In response, they provided a redacted screenshot showing all of the fields, which did include both registration and login IP addresses, as well as email addresses.
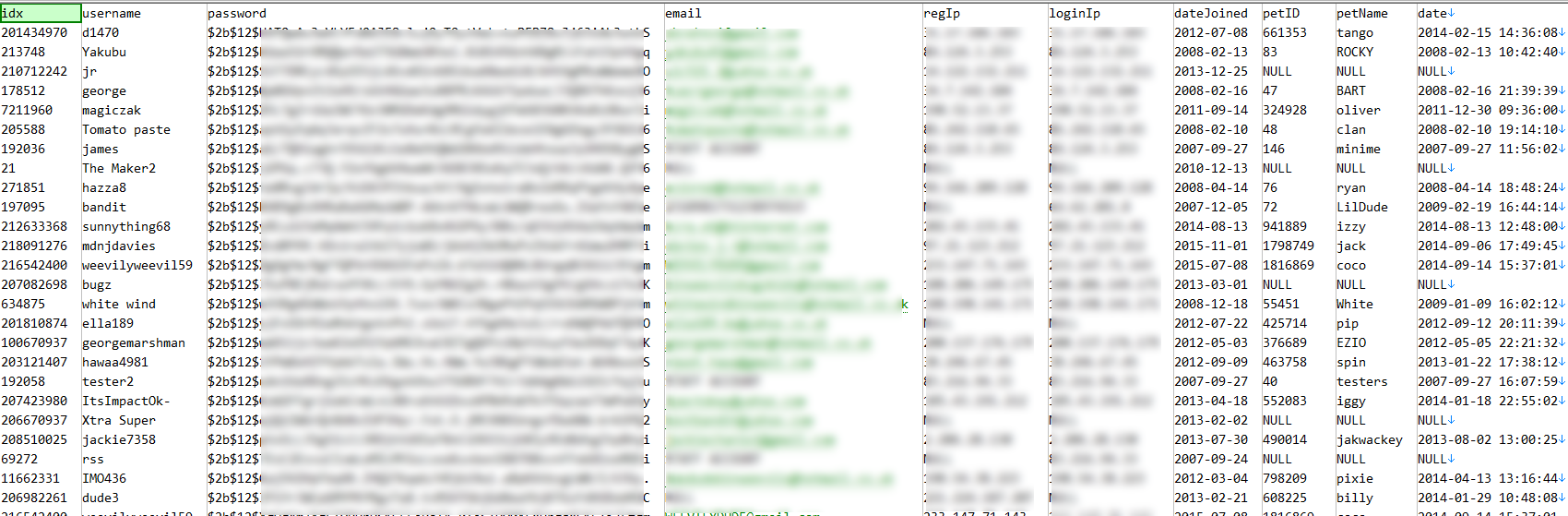
“Luke Baxter” allegedly informed him that they were reserving the full data set with the email addresses and IP addresses as they might sell all of the data privately at some future time. The 1-million record sample was to alert the public that the data were out there, but he claimed that the full data set has approximately 20 million records.
Data in the dump were dated from 2014, which would be consistent with the incident reported in September, 2014 by Bin Weevils. Attempts to verify the data by trying to create new accounts using usernames in the dump resulted in messages that the tested usernames were already taken. Data in the redacted screenshot corresponded to data found in the data sample, although it appeared to be from a different database as the order of the rows did not match.
Evidence that the hackers have email addresses obviously raises questions about Bin Weevils’ report that the breach affected (only) usernames and passwords. Based on Bin Weevil’s About page and Privacy Policy, the email addresses are likely the parents’ email addresses. Parents might understandably want to have been informed if their email addresses with some of their children’s information had been acquired by hackers.
DataBreaches.net sent Bin Weevils an inquiry yesterday asking them to confirm whether email addresses and IP addresses were also in the hacked database, and to confirm or deny the claim of approximately 20 million records, but has received no reply other than an auto-responder.
DataBreaches.net will update this post if additional information is obtained.
Update of August 20, 2017: DataBreaches.net received an email from a sender identifying themselves as “Akshay,” that claimed, in part:
… The information on that link I have given has the name ‘akshay’ in, who did not have anything to do with the games database being released, the name was used to blame another individual.
I have copy and pasted the lines on your website containing the name ‘akshay’ below. You was given this article by someone who was actually involved in what happened and now is trying to cover himself up and blaming others which is really sad.
“Pure”, “LukeBaxter”, “Akshay”, “Tyrone” and “Philip.”
Haha… It was one guy who got into the database and then credited his whole circle jerk squad. The majority of people credited were pre-teens were the type of kids who spent their time talking about cmd and batch files on chat room websites, they couldn’t hack for their lives.
The hacker and his wanna-be hacker friends haven’t been able to do anything like this data breach since, so they just milk this database breach as much as possible, hence why ShohidzIslam aka Legit is still trying to get articles written about it almost 3 years later by posing as outsiders who have contact with the hackers. Haha.
Bin Weevils had extremely low security at the time and so do many websites like it. None of the Bin Weevils accounts listed on the database have any use whatsoever considering 99.9% of them are made by children and Bin Weevils forced every active player to change their passwords. What do they get out of it? Their online alias’ publicized to a few hundred people whilst risking jail time? Worth it.
I wouldn’t be surprised at all. However: if the data were hacked, Bin Weevils should have disclosed more fully. Of course, this may all backfire on the hacker(s), too – including the ones who weren’t involved but have now been associated with it.
Thanks for adding background on this one!
The 20 million database is from 2015 – 2016, and yes it was a group of hackers from a chat who got into the database, it wasn’t only 1 person.. Plus binweevils.com gets hacked everyday because the staff members don’t care about the game and focus on mobile applications..
How about uploading me some proof that you have a database with 2015 and 2016 users’ data? Please upload unredacted users’ data so I can verify it. I’ll redact before any use or publication of it.
The 1 million database is from the database dump which got uploaded… the 20 million database is from the 2015, 2016 which I believe no one has got, yet.
Yeah read the post, they only gave the 1 million out to let people know of the breach and that they might sell 20 million in the future..
Akshay was not involved in the hacking of the game.