Have you ever wished you could just pick up a phone and get an emergency room physician on the phone to advise you in an emergency? Well, it seems that you can. According to their website, North Carolina-based Medcall Advisors is a “Workers Compensation and Healthcare Solutions” provider offering a comprehensive
tele-emergent care medical service utilizing technology to immediately connect anyone experiencing a medical event with a physician Board Certified in Emergency Medicine. Plan participants are able to access physicians through multiple mediums. Landline calls, smart phones and computers provide both audio and video consultations.
The firm offers individual plans, family plans, and plans for firms that want to provide the service for their employees who may get hurt on the job. They even offer specialized plans for truck drivers.
But as great as the triage and advisory service may sound at first blush, on August 24th, 2018 a member of the UpGuard cyber risk team discovered an unsecured Amazon S3 storage bucket that they were able to trace back to MedCall. And to their dismay, the bucket contained sensitive personal and protected health information for what appeared to be thousands of patients. The UpGuard team has written up their report on the incident here, but because this incident appears to implicate HIPAA and HITECH, I thought it should also be covered on this site.
For starters, not only was the bucket publicly viewable without any login required, but it was publicly writable, too, as the access control list (ACL) permissions were set to give “Everyone – Full Control.”
On August 30, UpGuard notified the firm’s CEO Randy Baker via email that the bucket appeared to be theirs and was not properly secured.
By 9:30 am the very next morning, the bucket had been secured, but Baker never even acknowledged UpGuard’s notification. As of today’s date, neither Baker nor anyone else at Medcall has responded to UpGuard’s notification. Nor has Baker nor anyone else at Medcall responded to two inquiries e-mailed to the firm by DataBreaches.net asking for more details about the exposure. Because of their lack of transparency, this report is based primarily on evidence provided to this site by Greg Pollock of UpGuard, who was part of the team that uncovered and investigated this incident.
Types of Data Exposed
UpGuard kindly provided DataBreaches.net with evidence of some of what they found exposed. Keep in mind that anyone could have clicked on the approximately 700 audio files and heard the conversations between patients and doctors who were advising them:

In addition to audio files, there were also some video files as well as traditional reports and files.
It was clear from available data as well as materials on MedcallAdvisors.com, that names, date of birth, relevant medical history, allergies, history of symptoms or incident, Social Security number, and other details were collected and stored by the firm for both its tele-emergent care service and its workers’ compensation services. The following is a partial record from an interaction, redacted by DataBreaches.net:
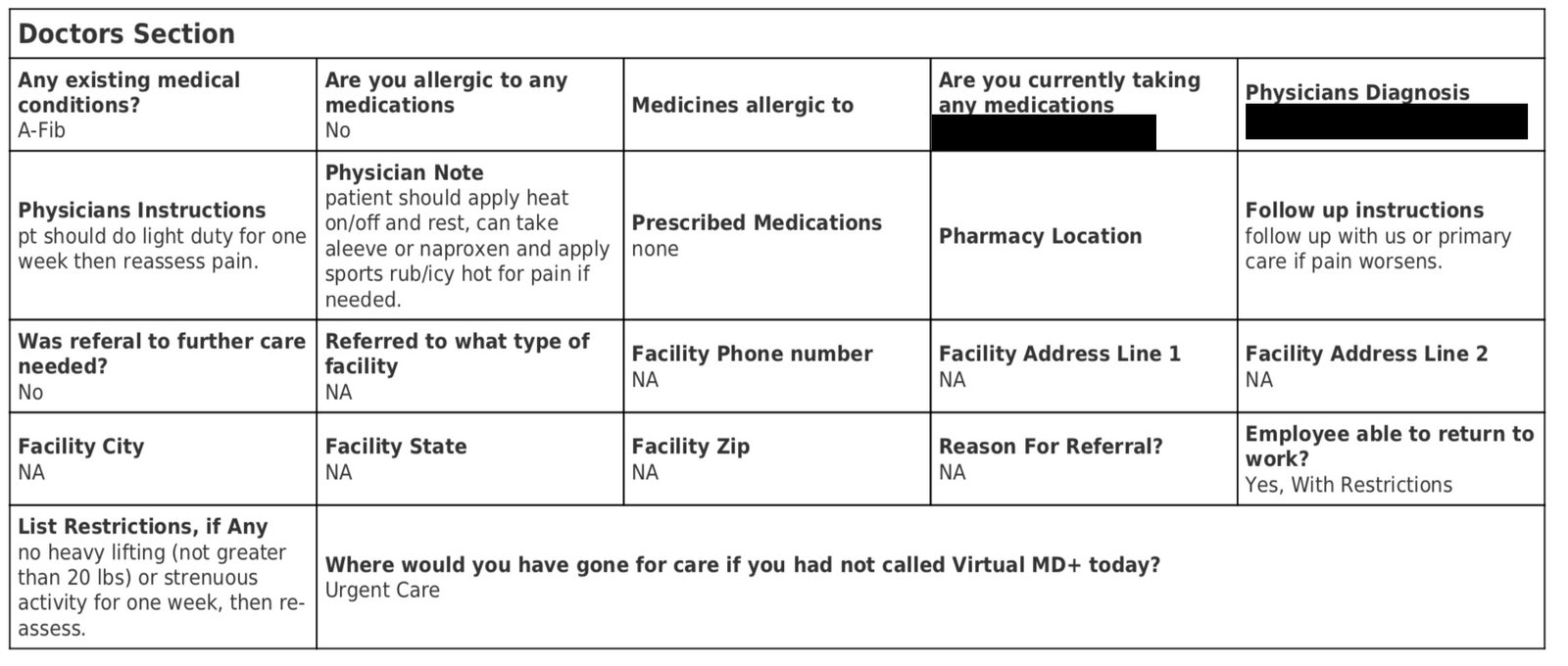
The following section of another patient’s report was also redacted by DataBreaches.net:
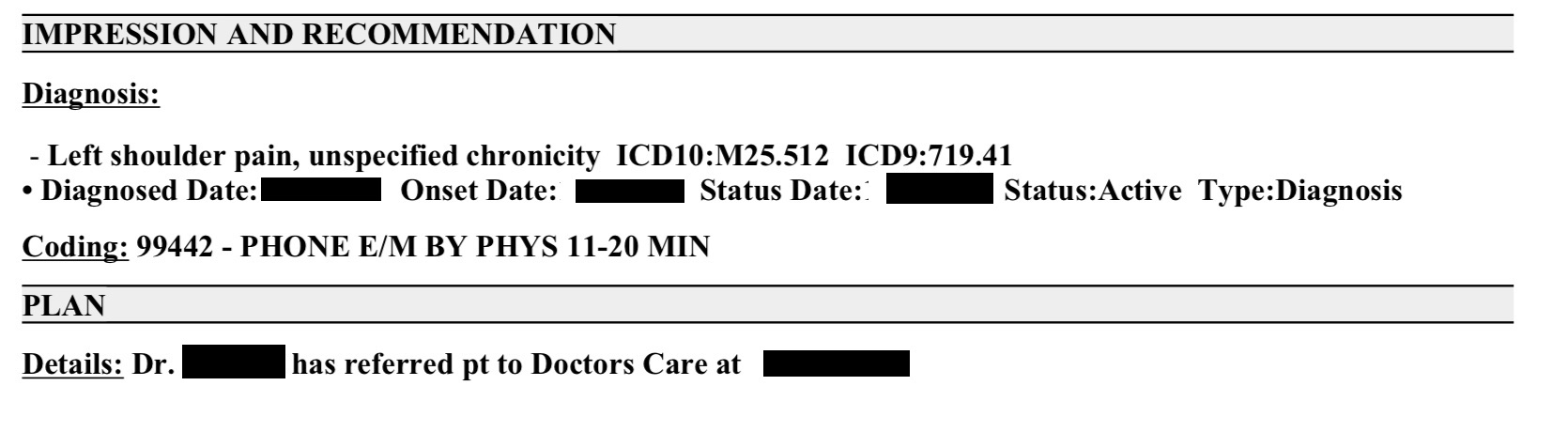
UpGuard provides numerous screenshots showing the types of reports and data collected and stored in plain text in this S3 bucket.
Asked to comment on what they had found, Pollock told DataBreaches.net:
“The digitization of medical information coupled with the move to internet-facing storage technologies has created an unprecedented problem for healthcare industry– the aggregation of large amounts of extremely sensitive information, centrally stored, and made accessible anywhere in the world. We’ve seen rampant privacy violations damage the relationship between healthcare companies and the people who rely on them. In order to establish trust in the industry, companies must ensure that the integrity of this sensitive data is protected by secure systems and controlled processes that prevent data exposures.”
And Then There’s the HIPAA Aspect
At several points in their material, including job listings found externally, Medcall refers to HIPAA or HIPAA-compliant portal.
This job posting provides some more insight into how they work:
https://nomadhealth.com/job/telehealth/louisiana/work-from-home-with-medcall-advisors-emm485
While the whole tele-emergent care aspect is fascinating in terms of considering how a doctor who is taking the call while at their regular day job will adequately secure the patient’s data and privacy, for now, let’s just consider whether anyone other than UpGuard researchers accessed this bucket that UpGuard estimates held data on 2,900 patients.
Will Medcall notify HHS/OCR of this incident? Will they notify any state attorneys general? Will they notify any corporate clients? Will they notify any patients?
To date, I have not seen HHS publicly take any enforcement action against a covered entity for exposing data this way (I am aware of at least one non-public inquiry at this time), but given how many examples we’ve seen of leaks like this, perhaps HHS/OCR should devote some of its limited resources to make an example of one case. Whether this should be the case or not, I don’t know, but the fact that the firm never had the courtesy to thank UpGuard does not earn them any transparency points in my scoring system. Then, too, the firm’s failure to make contact with UpGuard also means that they never asked UpGuard how much PHI UpGuard may have directly accessed and downloaded. Shouldn’t Medcall be inquiring about that and/or asking UpGuard about whether they are willing to securely destroy any PHI they may have in their possession?
And shouldn’t Medcall be at least a bit curious as to whether this site is in possession of any of their patients’ PHI – or whether any other media or news sites have been provided such data?
Sticking your head in the sand like an ostrich if you receive a notification from researchers is simply not a smart move. Why don’t entities know that by now?