In June 2022, Christopher Cook reached out to IPFS:
Hi @IPFS if someone sends a phishing email with an link to IPSF.io (sic) is that something that needs to be reported to your abuse team? If so, this is their link which is phishing for cpanel logins https://ipfs.io/ipfs/QmatpCGs1h4jCwAWcbUEFMMLrLjYi1Po3o29JWcCVxfszx
— Christopher Cook (@webprofusion) June 7, 2022
That link is now gone, but at the time, @[email protected] replied to Cook:
Thanks for reporting this 🙏🏼 I’ve passed it along. Yes, you can email [email protected] with anything like this.
— @[email protected] (@dietrich) June 14, 2022
Months later, @CEOemail commented:
ipfs abuse is becoming a big problem.
Why aren’t you doing proper due diligence on potential customers *before* allowing them to use your platform?
— CEOemail ✉ – Marcus Williamson (@CEOemail) October 14, 2022
There was no reply to that.
Today, DataBreaches received an email addressed to the administrator account. The content was typical of phishing attempts in that it threatened a cutoff date for email services and provided a link to click to verify my identity in case they had made a mistake.
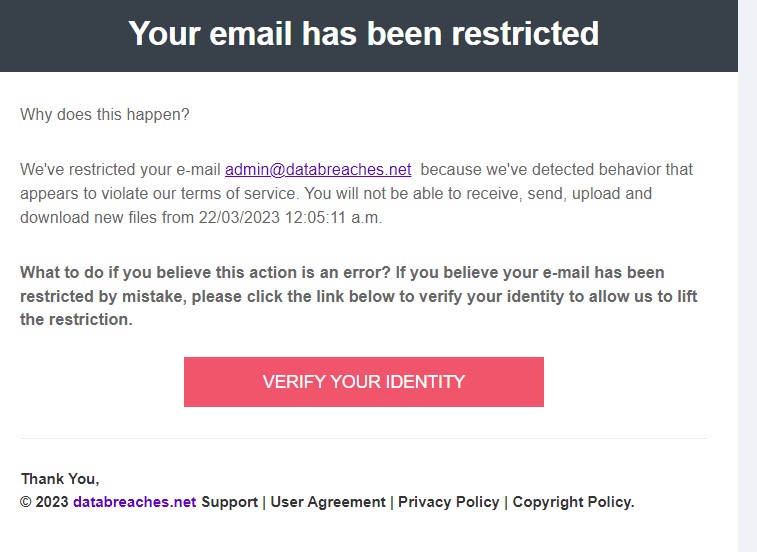
Somewhat amusingly, the “From” line in the email showed the sender as “Admin”<[email protected]>.
But if clicked, the validation link would have taken me to a url on IPFS.io. The url did not point to the exact same url that Cook reported last June, but the url pointed to the same directory as Cook had reported: https://ipfs.io/ipfs/
DataBreaches has sent an email to [email protected]:
Hi. I know IPFS was made aware of this security issue last June (a
thread on Twitter confirms that), but your domain appears to still be
used for phishing attacks. See forward below and attached for
screencap of email body.The phishing link points to:
https://ipfs.io/ipfs/[redacted]And please explain to me why the threat actors are still able to
misuse your domain.Thank you.
DataBreaches awaits their reply.
Update March 22. IPFS.io has not replied, and two more phishing attempts have been received. These appear to be from DocuSign:
