Bill Toulas of Bleeping Computer reported on a recent Arctic Wolf Labs investigation that caught my eye.
Arctic Wolf investigated two cases where victims of the Royal and Akira ransomware gangs who had paid ransoms were subsequently approached by threat actors offering to help them by hacking into the server of the ransomware gangs to delete their data. The threat actors claimed to be ethical researchers or ethical professionals. While the personalities involved in these secondary extortion attempts were presented as separate entities, Arctic Wolf assessed with moderate confidence that the two cases were likely perpetrated by the same threat actor.
Based on DataBreaches’ experience with a threat actor using the same moniker, “xanonymoux,” as their second case, DataBreaches believes they are correct in thinking their two cases are the same threat actor.
The rest of this post provides some details on “xanonymoux” based on DataBreaches’ interactions with the individual(s).
In late October, DataBreaches was approached by xanonymoux. They presented themselves as ethical and independent security researchers who could help victims recover data that had been hacked and exfiltrated by Akira and Karakurt. In their first contacts, they talked about OneDiversified as a victim, described how files related to government facilities and the Department of State had been compromised, and how they could help except OneDiversified had not responded to them at all despite them having sent dozens of emails to them. When DataBreaches reached out to OneDiversified to inquire about their claims, no reply was received.
In subsequent communications with DataBreaches, xanonymoux claimed that they had already been in negotiations with another victim but the victim stopped negotiating with them. That victim was the Michael Garron Hospital (MGH) in Canada, which had been hit by Akira and was originally listed on Akira’s site. When xanonymoux first mentioned the hospital to DataBreaches, MGH had not been claimed by Akira as yet, and DataBreaches noticed that xanonymoux said they were not sure whether Akira or Karakurt was responsible for the breach. DataBreaches reached out to MGH after xanonymoux claimed, “to be honest, I have already spoken with a negotiator who was allowed to handle all the conversation on their behalf with me. I offered them to pass the server’s information in exchange of a payment, so they would be ready to do everything quickly with LE.” At some point, however, MGH’s negotiator stopped responding to xanonymoux.
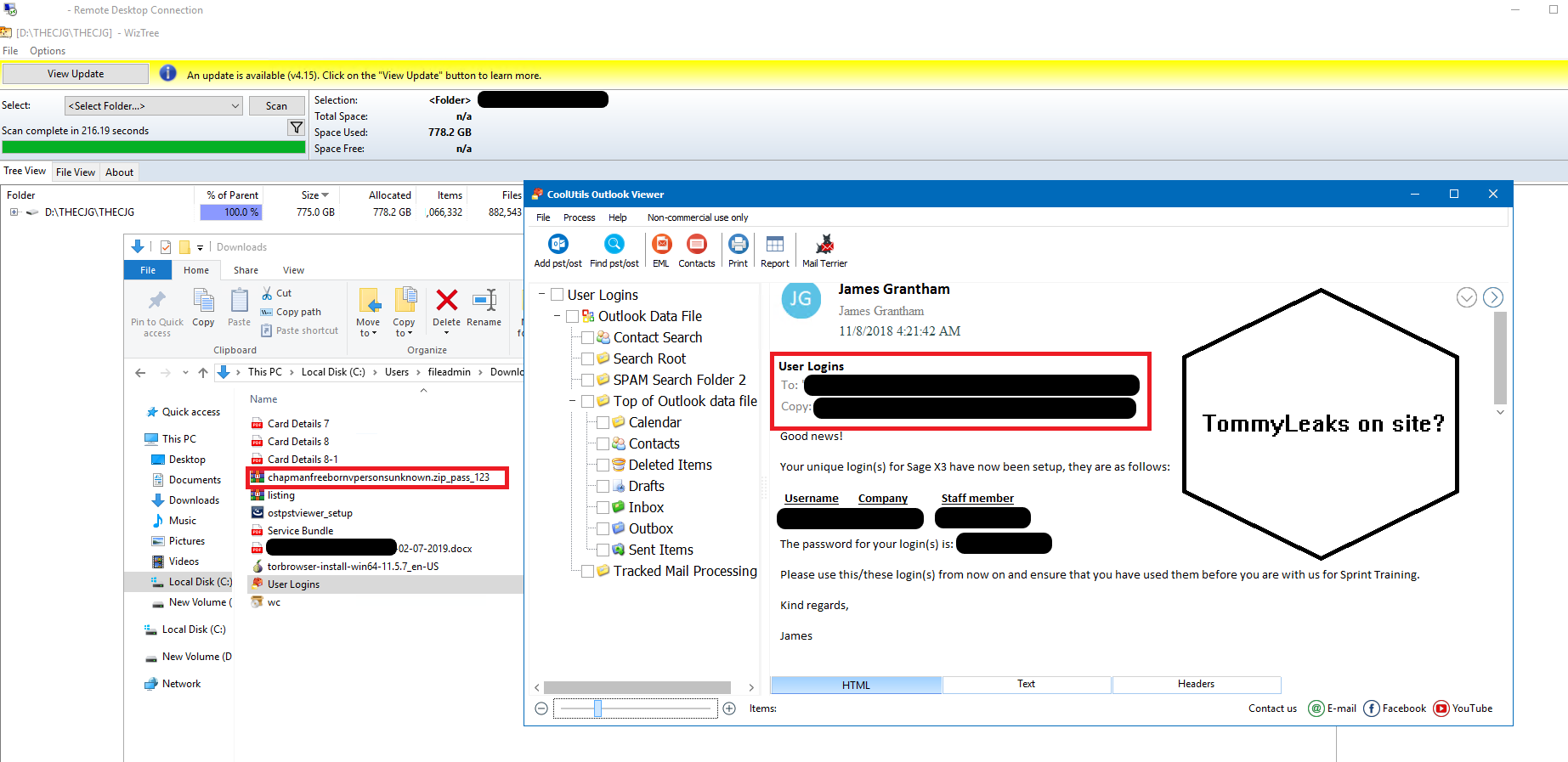
xanonymoux gave DataBreaches three files with Covid-related information that did appear to be patient data from MGH. DataBreaches was also given a file directory for Drive D and some other files that also appeared to be from MGH. In communications with MGH, their spokesperson confirmed that although data had been exfiltrated, it had not been encrypted. At some point, MGH was deleted from Akira’s leak site without any explanation. A screencap provided by xanonymoux to DataBreaches.net related to data from Michael Garron Hospital on Akira’s server. Akira’s listing had claimed to have acquired 775.0 GB of files and 882,000 files. The screencap allegedly taken from their server showed a modification date of October 24 and showed a folder size of 775.0 GB, and more than 882,000 files. Whether the data was subsequently removed by Akira is unknown to DataBreaches.
Of note, Arctic Wolf reported that their first case involved a threat actor calling themself “Ethical Side Group” who mentioned TommyLeaks. They do not report that their second case, “xanonymoux,” mentioned TommyLeaks, but at one point, xanonymoux mentioned TommyLeaks to DataBreaches. At another point, xanonymoux claimed that Akira and Karakurt were sharing the same server because “📯THEY ARE THE SAME GUYS 📯”
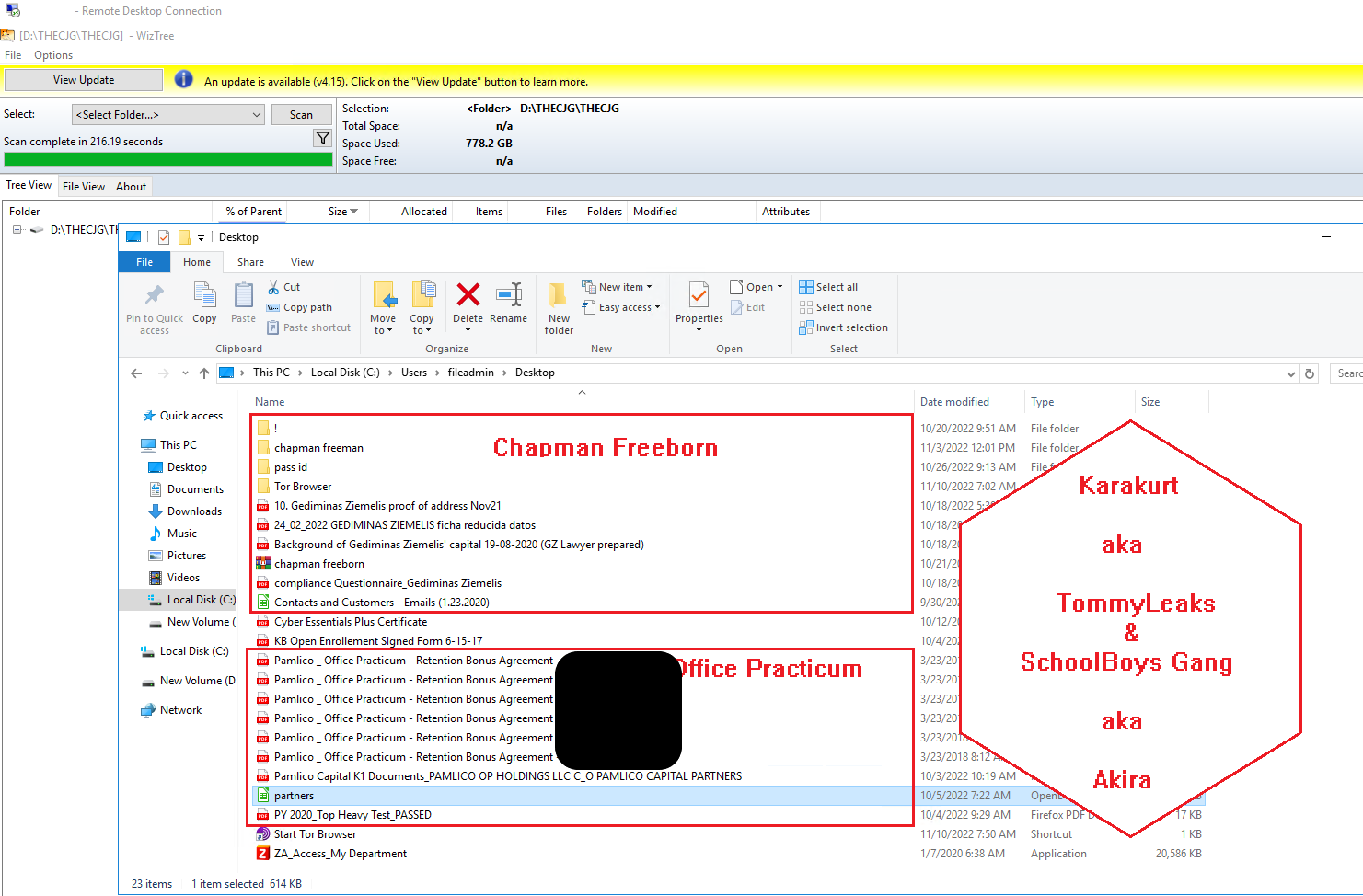
Other screencaps xanonymoux provided to DataBreaches revealed the names of other victims of Akira or Karakurt. The names of the victims have been redacted by DataBreaches.net in the screencaps below. The screencaps are included to show how xanonymoux was alleging that Karakurt was TommyLeaks and SchoolBoys Gang, and Akira.
Despite their proclamations of being independent private security researchers “on the white side,” it all sounded like extortion to DataBreaches, who questioned xanonymoux several times about how they could call themselves ethical researchers or ethical hackers when they were demanding payment before they would either delete the data they claimed they had access to or would give the victims the server information. They responded at one point, “It may sound like trading with their info or so, but in fact it is not. Never been interested in someone`s data. It is like services for payment — something like we normaly day-to-day. If you want a new phone – you get it as long as you can afford it.” At another point, they responded, “Help is here, but we do also pay our staff for outstanding work. And what we did, I think is pretty inspiring. At least one gang can be eliminated. But everyone wants everything free of charge. It does not work this way.”
When none of their targets responded to them nor inquiries from this site, xanonymoux told DataBreaches that they had applied for a reward under Rewards for Justice, but wanted to speak to the FBI to see if they could work something out so that they would give them the server information that would allegedly enable law enforcement to delete stolen data and disrupt the ransomware groups’ infrastructure.
DataBreaches suggested to them that they just give the FBI the server information and give the FBI their contact info in case a reward was to be had, but they declined until they could speak to the FBI. So DataBreaches asked them for some proof of claims and forwarded it to the FBI with xanonymoux’s request to speak with them. The forward included an email address for xanonymoux and some screencaps, two of which are shown above.
To DataBreaches’ knowledge, xanonymoux never got any reward. Whether they ever gave the FBI the IP address of any server allegedly used by Akira and Karakurt is also unknown to DataBreaches. After Bleeping Computer’s reporting made DataBreaches aware of the Arctic Wolf report, DataBreaches emailed xanonymoux, asking if they had any comment or response to Arctic Wolf’s report. There has been no reply by publication, but xanonymoux’s claims to DataBreaches were clearly consistent with Arctic Wolf’s reports on their two cases. The only difference, perhaps was that their cases mentioned Akira and Royal, while xanonymoux claimed to help with Akira and Karakurt. In all other major respects, however, the claims were comparable.
Arctic Wolf raises the question of whether these threat actors are working with the original ransomware gangs or with their knowledge, approval, or neither. DataBreaches has formed no firm opinion on that at all, but given that in discussing a particular victim, they weren’t sure whether a particular victim was Karakurt’s or Akira’s, they may have no direct involvement with the groups. As Arctic Wolf suggested, however, their activities do highlight the risk that victims face of being re-extorted by third parties who may know where others store their stolen data.