- Medico, Inc.’s IT vendor’s error left at least two Amazon buckets unsecured
- More than 300,000 files contained protected health information related to patient billing, complete with insurance information and treatment codes
- Leaks were independently discovered by at least three researchers using different search methods
It’s been a rough few months in terms of business associates or third parties disclosing breaches of protected health information. In May, we had reports of more than 20 million patients impacted by breaches involving OS, Inc. and the American Medical Collection Agency. Both of those incidents involved attacks by external threat actors, but the AMCA breach affected more than 20 million patients, and resulted in the firm losing clients and filing for bankruptcy protection while state attorneys general launched investigations.
But while external attacks continue to dominate the threat landscape in the healthcare sector, human error incidents may also have a devastating impact.
This post is the first of at least five posts I hope to write that involve recent and previously undisclosed leaks of health information. A few of the five incidents involve entities in India, two of the incidents involve HIPAA-regulated entities, and frustratingly, two of the exposed databases are still exposed because the entities have not responded to notifications.
But one data protection nightmare at a time, right? So let’s start with an incident that involves a firm that is a business associate for HIPAA-covered entities.
The Medico, Inc. Leak
I am starting this series of posts with the Medico incident because no less than three different parties independently discovered that Medico, Inc. was exposing protected health information, and we had all found it using different search methods and strings:
This site had found it on June 15, while running an exploratory search on grayhatwarfare.com using the name of a large health insurance company.
Less than 48 hours later, a researcher contacted me to alert me to the very same bucket, but he had found it while searching Shodan.io using another search approach.
Weeks later, I would learn that UpGuard had also discovered an exposed Medico Amazon bucket.
But to keep this in some chronological order: the bucket I had found did not have a name that would give any clue as to ownership, requiring me to do some digging through the files to determine whom to notify. Days after first finding the bucket, DataBreaches.net reached out to Medico, Inc. to alert them.
Within hours of notification, Madhu Babu, the COO of Medico, Inc.responded by email to say that he would be calling me first thing in the morning. And he did. And one of the things he told me in our first phone conversation was that he had also received a courtesy notification about the exposure from UpGuard hours before he received this site’s notification. UpGuard’s team would subsequently tell me that they had found the bucket using yet a third search strategy. In any event, it seemed that both UpGuard and DataBreaches.net had notified Medico within hours of each other. But as we would later realize, UpGuard and DataBreaches.net had found different buckets. Both were Medico’s, but the bucket UpGuard found, described and illustrated in their detailed report, was a smaller bucket with fewer files.
At least three whitehats found Medico buckets exposing PHI. How many non-whitehats may have found the PHI, too, and downloaded it for less than honorable purposes? We do not have the answer to that question yet.
About Medico, Inc.
Medico, Inc. is a business associate that provides services such as medical billing, medical transcription, medical coding and compliance audits to HIPAA-covered entities. Their medical billing service is advertised as processing 100,000 claims processed monthly for 400+ active healthcare providers and 100+ practices.
Unsurprisingly, then, they say that they take privacy and data security very seriously. Babu informed this site that they have business associate contracts in place with their clients, and they have the necessary contracts in place with their vendors and third-party providers – including those who provide IT services. According to Medico’s statement to this site, the unsecured Amazon bucket this site found had been handled for them by an IT vendor that they have declined to name at this time.
Findings
Unfortunately for Medico, the vendor’s error resulted in 91.6 GB of patient data in an Amazon s3 bucket being left exposed for the taking, without any login required (this is apart from the bucket that UpGuard found and reported on elsewhere).
This bucket contained 307,139 files. The files were in folders — one folder per date — beginning in January, 2019, and going through March 1, 2019.
Each day’s folder contained a number of folders. Some of these had folder names with the name of the patient as the folder name. Some of the folders had names that indicated the name of the provider, while yet other folders had the names of the insurers. And then there were other assorted folders that did not fall into any of the preceding categories.
The files contained what you might expect to see for a firm that handles billing services: patient’s name, date of birth, address, Social Security number (in some cases), insurance policy number, date of service, service code (CPT), and any related billing information such as date submitted, date paid, date claim was denied and/or appealed, and photocopies of any checks or credit card transaction if the patients paid the provider directly. For some patients, there might be only two .pdf files in a folder: a discharge report from a hospital showing their personal and detailed medical history of admission, and a second .pdf file relating to submitted claims for payment of the doctor’s charges. DataBreaches.net is not posting screencaps of these types of files. UpGuard has provided screenscaps in their report that you can see on their site.
Most of the files in this bucket appeared to be in plaintext, although some folders were password-protected. Having password-protection on files is better than not having it, of course (although strong encryption would be even better), but anything gained by password protection is lost if:
1. You include the password or login credential in the files exposed online;
2. You use ridiculously weak passwords; and/or
3. Your file names contain protected health information as part of the plaintext filename.
Unfortunately, all three were the case in this incident.
DataBreaches.net observed that numerous folders and files contained patients’ first and last names (and in some cases, middle initials) as part of the filenames or folder names. Other filenames contained other PHI such as details concerning billing or payment.
There were also entries of logins to insurance company portals for billing. Sadly, all the logins were in plaintext, and the passwords were ridiculously embarrassing (like “Medico1” or “Medico2014”). In some places, I could see attempts to note security questions and weak answers.
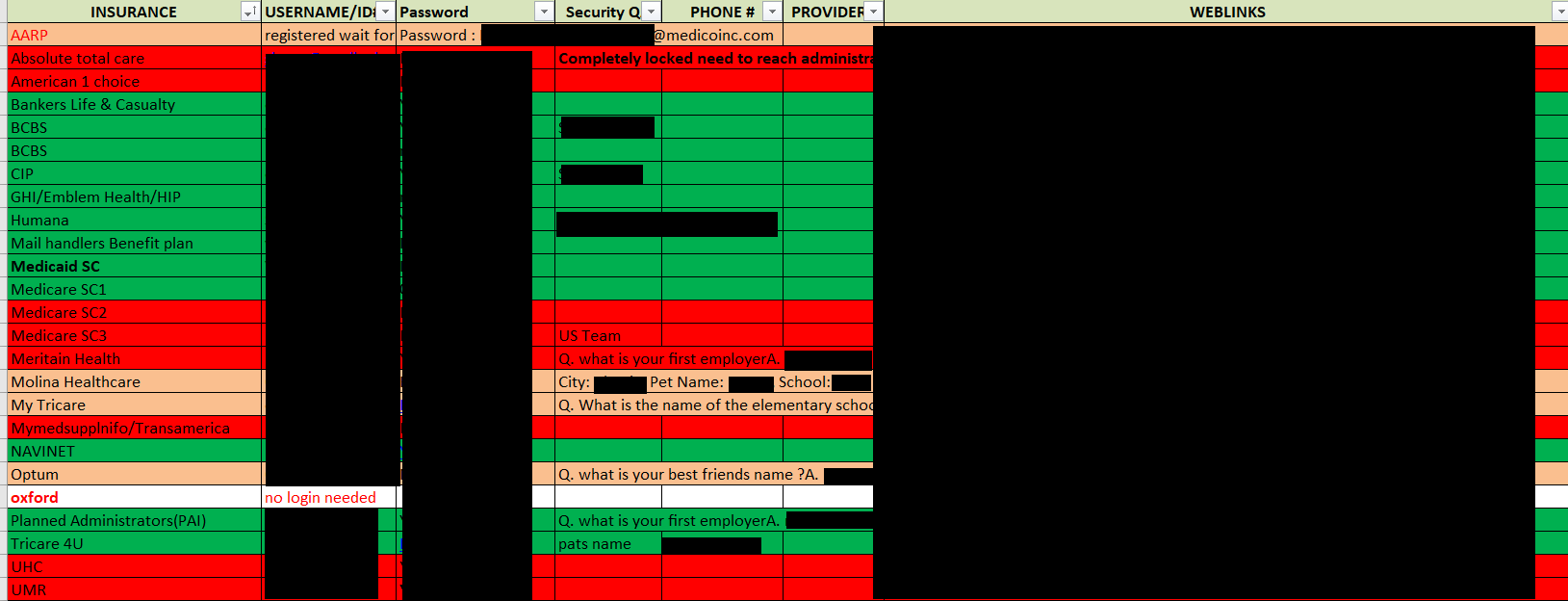
But some of the most concerning contents were the patient reports such as hospital admission histories with discharge notes, or even bills that did not spell out diagnosis or treatments, but where such information could be quickly obtained by merely looking up the ICD-10, DSM-5, or CPT codes via a Google search.
Medico’s Incident Response
Within hours of being notified, Medico had the exposed buckets locked down and then removed. And within 48 hours after being alerted to the leak, Medico’s COO informed DataBreaches.net that they had already notified all of their clients and were pursuing their investigation and determination as to what agencies and/or patients they might need to notify. Their COO was also in communication with UpGuard during the same period.
Now What Will HHS/OCR Do, If Anything?
A business associate’s vendor allegedly made an error. As a business sssociate under HIPAA, could Medico be held liable by HHS/OCR for a security failure by the unnamed vendor? My reading of HHS’s fact sheet on the liability of business associates leads me to think that Medico, Inc. might not have direct liability in this case — but that determination might depend, in part, on whether Medico can demonstrate that they had complied with HIPAA’s requirement for a risk assessment, etc.They certainly cured the problem promptly once they were aware of it.
Some readers may also be surprised to learn that the covered entities — the providers and practices that contract with Medico — generally have no direct liability either, as covered entities are not required by HIPAA to monitor their business associates for compliance (although there are some requirements that they must comply with).
So for those thinking about who gets sued, take a breath and think some more. And let’s wait to see what Medico finds out in their investigation as to whether any non-whitehats might have accessed or downloaded the data. And let’s see what HHS/OCR finds in its investigation — or whether any state attorneys general decide to open their own investigation.
There’s a lot we don’t know, but trust me on this: this leak is just one of waaay too many leaks that are due to misconfigurations that should be relatively easily avoided by now.
Post edited post-publication to correct link to UpGuard’s report.