As Robert Lord of Protenus explains in the May issue of Compliance Today, pediatric patient data continues to remain not only vulnerable to criminals, but also quite valuable to them, in part
because the medical records of these young patients provide criminals a blank slate upon which they can build a false identity. This—combined with the fact that medical identity theft of pediatric patients is incredibly hard to detect—means that criminals have a much longer time period with which to profit from the stolen information, costing the victim hundreds of hours and thousands of dollars.
Certainly, listings offering medical records on dark web marketplaces are concerning, as I noted previously when I found detailed mental health records up for sale. And although medical records are generally not selling for as much as many reports have claimed, here’s a listing by a vendor calling himself “Skyscraper” that had me both curious and concerned:
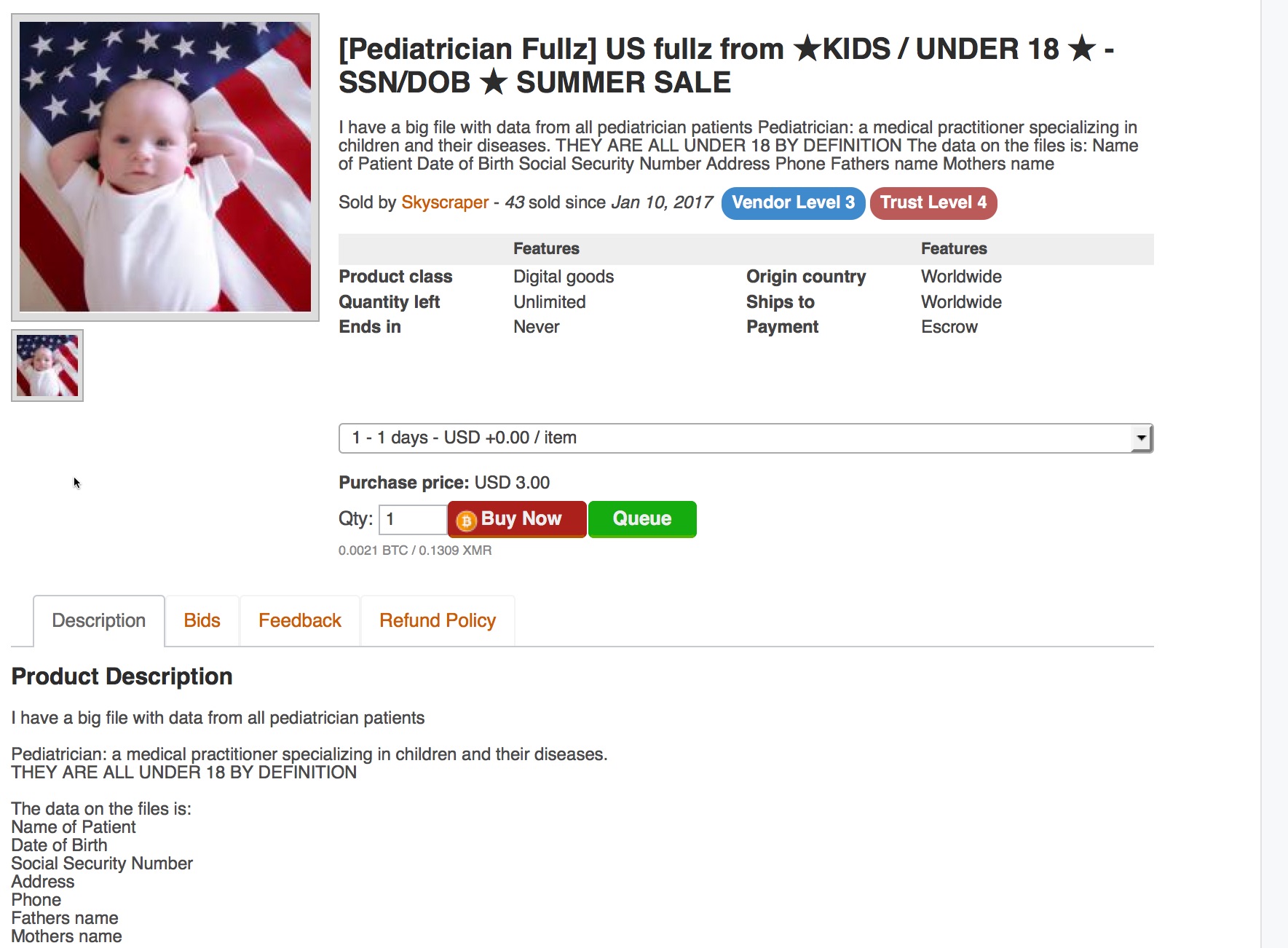
In a private chat, Skyscraper informed this site that the records he was selling came from a number of sources – and all were acquired within recent months. By his estimate, he has about 500,000 children’s records from pediatricians’ offices and an additional 200,000 records acquired from children’s schools (k-12).
I’ll just pause here to let that sink in, because if you’re a regular reader of this site, you’ll know that I haven’t reported any pediatricians’ breaches that would add up to 500,000 over recent months. Nor have I reported enough k-12 breaches to add up to 200,000. So how many pediatrician offices and schools do not know they’ve been hacked – or do they know and just haven’t disclosed publicly? Even if the vendor overestimated the number of records he has for sale, there’s a significant discrepancy between what we know about and what he’s likely amassed.
Skyscraper provided this site with a small sample of records containing child’s name, date of birth, postal address and zip, telephone number, Social Security number, father’s name, and mother’s name. DataBreaches.net contacted the families by phone, and the parents confirmed the accuracy of their children’s identity details. The families’ names, phone numbers, and postal addresses were also verified by consultation of voter registration rolls and public sources.
DataBreaches.net was unable to determine which pediatrician’s offices may have been the source of the sample data, however, as each child’s family reported having seen more than one pediatrician over the years.
When asked about his methods, Skyscraper stated that he finds the targets via searches for “Patients:”
I just ‘search’ for anything called Patients and for some stupid reason entire databases show up…. What I mean is I throw wide and the bad thing is the most that comes back in fishing net is medical data.. they’re the worst.
Skyscraper’s searches do not include Shodan or FTP, he tells this site.
I asked Skyscraper what ONE thing pediatricians’ offices might do or should do to prevent him from successfully attacking them. Expecting him to say something relating to RDP or phishing, I was somewhat surprised at his response:
I think one of FIRST things they need to do is pay for their software. You wouldn’t believe how many of those offices run on cracked / downloaded software and outdated 2015 versions.
But then Skyscraper turned to a point this blogger has made many times: retaining inactive patients’ data and connecting it to the internet. As he noted, even small practices tend to amass thousands and thousands of patients’ records over many years, putting even former patients at risk of becoming victims of a hack.
As Skyscraper wisely commented at another point in the interview, “Data doesn’t need to be accessible for anyone on the other side of the world.”
And maybe we should just let that sink in, too.
If you are a parent of an under-18, do check with a major credit bureau to see if there’s already a credit report on your minor child (there shouldn’t be). You can also find helpful information on the Federal Trade Commission’s site as to how to repair problems if they have already occurred.
Update: In February, 2019, CBS News did an episode in which they reported on Skyscraper as part of their reporting. I tweeted something about how I had reported on this threat actor in the past. Someone then responded that I had *paid* Skyscraper and was somehow paying criminals to extort people. The person who tweeted those defamatory statements was an employee at a clinic that had experienced a devastating hack. I had discovered the breach and alerted the clinic to it and then delayed publication to allow them to start incident response. This one employee, however, seemed to believe that I should have waited to report until the clinic had notified everyone themselves first. I don’t know a single journalist who would have sat on the story that long, and indeed, given that patient data had already been sold on the dark web, it was important to alert patients as quickly as possible.
When he was made aware of her inappropriate behavior, her employer, who had been grateful to me for alerting them to the breach, apologized to me for her rude behavior.
But to be clear: I did not pay Skyscraper for the sample of data he had provided me for reporting purposes for this story. He gave me data. Many hackers give journalists samples to prove their claims, and this was no different. I have never bought data, nor paid anyone for data. Anyone who claims otherwise is mistaken or just maliciously lying.
Something to note: I have yet to see a EMR/EHR that allows for data purge after the time
has passed and a practice can legally destroy it. In the old days a paper chart could be shredded, not so easily done now days.