The email in my inbox on Friday night had the subject line, “Hey sexy,” and appeared to come from “[email protected]” <[email protected]>. Under normal circumstances, I would have just sent it to trash, but the Twitter user known to me as “Pompompurin,” had alerted me to check my email for what he described as a funny email he had sent me.
“Hi its pompompurin,” the email read. “check headers of this email its actually coming from fbi server #SUS”
To my surprise, the headers did confirm that it was coming from the FBI’s server (SpamHaus subsequently provided a sanitized version of the headers from a hoax email sent to thousands of entities).
The [email protected] address is part of the FBI’s Criminal Justice Information Services division, and is used to send notifications from the Law Enforcement Enterprise Portal (LEEP), a “secure platform for law enforcement agencies, intelligence groups, and criminal justice entities.”
Pompompurin told me not to try to reply to the email, as he couldn’t receive replies at that address, but he could send from it, he wrote.
Hours later, Spamhaus tweeted that thousands of companies had received emails from that same government email address. Those emails did not have a “Hey sexy” subject line, however. Those emails had a subject line: Urgent: Threat actor in systems and contained what purported to be an urgent alert about a systems intrusion.
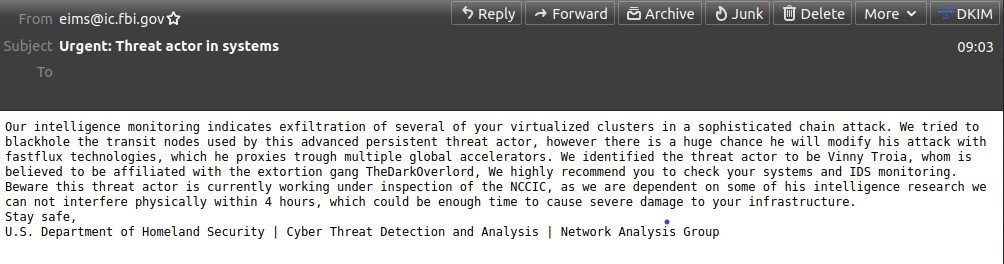
The warning email (text) contained a number of errors that led some people to flag it as a hoax, but many people were reportedly alarmed by it and flooded the FBI with calls. Their reaction surprised Pompompurin, who later told DataBreaches.net that he had felt it was “quite clear with all the random words that it isn’t real. It doesn’t even make any sense.”
Brian Krebs, who also got an early email from Pompompurin, has a detailed write-up of how Pompompurin discovered a one-time passcode embedded in the html for getting a registration confirmation email, and how using that enabled him to send out the hoax email. Pompompurin told DataBreaches.net that he had scraped the email addresses from the ARIN database, and that was the only database he used to send emails to.
As Pompompurin told Krebs, he could have done real harm if he had chosen to (the hoax email did not include any action items for recipients so there was no danger from that, at least). Real harm also could have occurred if state actors or other adversaries had found and exploited the flaw.
Yesterday, the FBI said that no data had been stolen from their server and that the agency had fixed the software vulnerability that allowed the attack.

It Only Took 5 Minutes to Open the Door to Potential Chaos
According to Pompompurin, it only took him about 5 minutes to discover the passcode that he used to send the hoax emails. “I was just going through the registration process because I was bored, and then I noticed it when sending the verification email,” he said.
Pompompurin notes that the warning at the bottom of the LEEP page probably has scared off responsible security researchers from exploiting it if they found it. When asked why he wasn’t scared off and why he hadn’t tried responsible disclosure, he answered, “Responsible disclosure for government websites is always a pain. I highly doubt I would’ve ever got the attention of anyone there. I took responsibility because it was already obvious that I did it.”
When asked if he explored any other government sites to see if they had the same vulnerability, he responded, “No, its a very rare thing to see these days, and I’m surprised as much as everyone that the FBI made such a mistake.”
But What’s Troia Got to Do With This?
For those who were already aware of some people’s history of trolling Vinny Troia of NightLion Security and ShadowByte, the inclusion of Troia’s name and one sentence about him in the urgent email would have clued them that email was a hoax:
“We identified the threat actor to be Vinny Troia, whom is believed to be affiliated with the extortion gang TheDarkOverlord.”
Troia has written a book in which he claimed he had identified some of the key threat actors in thedarkoverlord. He has named them publicly on a number of occasions, and after “Pompompurin” had appeared on Twitter last year, Troia claimed that “Pompompurin” was just another alias for the Canadian known as “WhitePacket” whom Troia had named as thedarkoverlord. In his most recent statement below, Troia now seems to be backing off on claiming that Pompompurin is actually WhitePacket, and he is now described him as collaborating with WhitePacket or being a front or patsy for him.
Pompompurin does not deny developing a relationship with WhitePacket, but has always denied being WhitePacket. “I am not Whitepacket, Vinny has provided zero evidence to support his idiotic claims. I became friends with Whitepacket after the fact,” he told DataBreaches.net.
When it was pointed out to Pompompurin that some news sites were claiming that his motivation — or one of his key motivations — was to tarnish Troia’s reputation, he replied, “My motivation was to have fun. It wasn’t to “Tarnish” his reputation per se, but it is funny thinking about a bunch of people thinking Vinny hacked their systems.”
If he thinks that is funny, how much more fun does he have planned? On his blog, Pompompurin has added a blog post that reviews past allegations of wrongdoing or questionable behavior by Troia. If that’s not an attempt to discredit Troia or to try to get Troia viewed as a criminal, I’m not sure what would be. But Pompompurin denies any end goal.
“I have no end goal, I just find it funny to troll him,” Pompompurin told DataBreaches.net. “I also think it’s funny to mess with him since he acts like a security researcher, when we all know he’s just as bad as many of the people on RF who leak databases.”
Later, he told DataBreaches.net that he thinks Troia should be arrested for leaking databases. When asked whether that means he and others who leak databases on RaidForums should also be arrested, he replied:
“well. not “Should” be arrested,” he answered. After a pause, he changed his answer to:
“Actually yes, since its illegal
Technically”
That sounds like an honest statement, but one that probably won’t win any popularity contests on RaidForums, where Pompompurin and others leak and/or sell databases.
Pompompurin is correct in at least one other statement, though: if Troia has any hard proof that Pompompurin is WhitePacket or engaged in any criminal activities with WhitePacket, he has not made it public. But according to Troia’s statement to DataBreaches.net, he will be making what he claims is evidence of a connection between the two public in the immediate future.
When asked if he had any statement about the hoax and the inclusion of his name, Troia provided the following statement to DataBreaches.net last night. All spelling and typos are as in the original, but DataBreaches.net has redacted the real name of WhitePacket because he has never been arrested or charged:
first, I absolutely believe this was a smear campaign by the actor PomPompurin. Whenever he comes after me, he always (sadistically) tells me something is coming a few hours before. In this case, he told me something was coming about 8 hours prior to the FBI emails going out.
For example, prior to that, PomPom hacked the national center for missing and exploited children’s website (image attached) just to list me as a pedofile in their blog. Before that, I believe he was involved in personally wiping tens of thousands of elasticsearch servers globally, leaving my name as a calling card.
These are very childish actions intended to discredit me for putting out a report which exposed his identity and involvement in several other hacking groups including the dark overlord, gnostic players, and shiny hunters.
As far as PomPompurin directly, I have recently come into evidence that directly links him to [REDACTED]. That being said, I also don’t believe that PomPompurin (by himself) is [REDACTED]. Much like all of the other groups before him, [REDACTED]’ MO is to use a patsy to be the front person for his hacks. With Gnostic it was Gabriel, with Shiny it was Nassim, and with TDO it was Wyatt. PomPompurin on RaidForums and Twitter does not seem intelligent enough to have carried out these sophisticated attacks, so it stands to reason that he is just another in a long line of people designed to take the fall for him.
That being said, he recently made a critical error which I can tie back directly to [REDACTED]. I have already shared this information with law enforcement and have been holding onto it – but given the recent attacks against me, I will be publishing a blog with this information in the coming weeks.
On a personal note, I happen to believe [REDACTED] is one of the most gifted hackers I have ever met.
But he is becoming bolder and much more blatant with his attacks. Going after the FBI then publicly giving an interview (to Krebs) admitting how he did it is incredibly wreckless – it’s almost like he is taunting everyone because he doesn’t believe the US will be able to extradite him. And to some extent has has been right. Calgary police have all but given up coming after him – I don’t know why the FBI has not extradited him yet, but I believe it has something to do with Canada’s strict privacy and cyber laws.
My team and I have been working with Congressman Correa to help bring him to justice and hopefully sidestep some of the extradition challenges. Correa will be issuing a press release on the matter tomorrow.
DataBreaches.net notes that a lot of Troia’s assertions about who did what in the statement above are unproven claims and he seems to be talking about different people interchangeably. For example, where Troia states, “These are very childish actions intended to discredit me for putting out a report which exposed his identity and involvement in several other hacking groups including the dark overlord, gnostic players, and shiny hunters,” who is the “he” Troia is referring to — Pompompurin or WhitePacket? You might think he was referring to Pompompurin, but Troia’s report did not identify Pompompurin nor link him to the hacking groups mentioned in that statement. So he appears to be talking about WhitePacket in that statement and equating WhitePacket with Pompompurin, even though later on he says that he does not believe that Pompompurin by himself is WhitePacket.
So Troia seemed to be equating Pompompurin with WhitePacket but then sentences later, he claimed that they are not the same person. And if that’s the case, then why does Troia claim that it was WhitePacket who was responsible for the hoax email when it was a low-level incident that Pompompurin executed and took responsibility for? Troia provides no evidence that the hoax email involved WhitePacket at all, despite asserting that he was responsible for it and that it somehow proves WhitePacket is getting bolder and taunting people because he does not believe he will be extradited.
This type of interchangeability of aliases and individuals in Troia’s writing and attributions has been a long-standing source of DataBreaches.net’s critique of Troia’s research and attributions. Although Troia blames Canadian law enforcement or Canadian laws for the lack of an arrest of WhitePacket, after reviewing his book and technical report, DataBreaches.net had concluded that Troia had not provided any compelling evidence that WhitePacket was thedarkoverlord. That is not to say that DataBreaches.net is claiming that WhitePacket is an innocent angel who has never done anything wrong. What it is saying is that in this blogger’s opinion, Troia did not provide any compelling evidence that WhitePacket was thedarkoverlord – or that he was with GnosticPlayers or ShinyHunters. And now he has added another attribution to his evidence-deficient attributions.
If Troia has actual evidence to support his claims about Pompompurin and WhitePacket, it would be helpful to publish it. As of a few minutes ago, he has indicated that he will be publishing something tomorrow.
Updated Nov. 16: Troia has published his post about Pom and attribution here. Much of it seems to be based on Pom purchasing and using a domain (og.money) that WhitePacket used to own and using the same (old) source code. I’m not sure that proves anything other than Pom bought one of WhitePacket’s old domains and used the same source code that was originally used for it, but Troia does have other data in his post that is worth reading and considering as to whether it provides any real indication that Pom is connected to WhitePacket and others that he presumably wouldn’t know as a relative newcomer. I just wish the chat screencap wasn’t redacted and was more complete.