When CoPilot Provider Support Services recently disclosed a security incident that they had known about since 2015, their statements might have led you to believe that a disgruntled former employee had hacked them or misused previously authorized access, and that law enforcement might be looking into criminal charges. If you thought that, you were wrong on both counts.
CoPilot Provider Support Services (“CoPilot”) describes itself as a “healthcare administrative services and information technology organization.” One of its services enables physicians to determine if their patients’ medical insurance would cover them for injections of Monovisc and Orthovisc, injections used to treat osteoarthritis. Monovisc and Orthovisc are distributed by Depuy Mitek, a division of Johnson & Johnson. If authorization is approved, the medications may be provided by CareMed Specialty Pharmacy, CoPilot’s affiliated firm. CareMed and CoPilot are both owned by Moby Kazmi; the President of the firms is Nuaman Tyyeb.

In 2015, a database with 220,000 patients’ protected health information was involved in a data security incident. In its notification to patients more than one year later, CoPilot wrote, in part:
On December 23, 2015, CoPilot received complaints claiming that personal information submitted to the site, including health information, was accessible for downloading from the website. ……… As a result of CoPilot’s investigation, CoPilot believes that it identified the individual who accessed CoPilot’s database through unauthorized means and downloaded certain health information, and that the data was not accessible for downloading by the general public from the website. Subsequently, CoPilot referred the matter to law enforcement. Our understanding is that the law enforcement investigation supports CoPilot’s conclusion about the identity of the responsible individual.

The unnamed individual appears to be John Witkowski, who was their Senior VP of Marketing and Sales for seven years, ending in February, 2015. In an extended interview with DataBreaches.net, Witkowski claimed that CoPilot and CareMed have engaged in multiple fraudulent activities over the years, and that several inaccurate claims they’ve made about the data security incident are only the tip of a very large iceberg.
Witkowski explained that in 2014, CareMed settled federal and state charges under the False Claims Act. As part of the settlement, CareMed admitted that its employees posed as employees of physicians’ offices when they sought approval for medications, and that employees also fabricated patient clinical information to get insurers to approve the treatments.
According to Witkowski, almost immediately after settling those fraud charges, CareMed/CoPilot principals engaged in more deceptive conduct: purchasing a pharmacy in New Jersey so that they could get a contract with Express Scripts, who had cancelled their contract after CareMed admitted guilt on the fraud charges. Not knowing that they were dealing with the same principals, Express Scripts would give the new entity network status and CareMed’s principals would continue to have a lucrative contract, Witkowsi claims.
Witkoswki says that when he discovered what CareMed/CoPilot had done, he submitted his resignation, citing their conduct and risks to patient safety that he alleges were also uncovered during due diligence. He claims that the firm initially did not accept his letter of resignation, later tried to terminate him, and has alternately offered him settlement packages and threatened him with litigation. Witkowski showed DataBreaches.net a $1.8m settlement offer from March 2015 that he refused.
The 2015 Security Incident: What Really Happened?
Witkowski claims that CoPilot’s notification and statements contain a number of significant misrepresentations or flat-out lies, including how the incident occurred, and the extent to which the patient data were freely available to the public.
Witkowski claims that in May, 2015, he heard that a CoPilot database was exposed on the internet without any login required. He did nothing at that time to investigate what he had been told, he says, but in October, while doing competitive research for a firm he opened to compete with CoPilot, he visited the site and found that the database was (still) exposed. Anyone just visiting the site, he claims, would see the phpMyAdmin panel, as the home page automatically redirected to it, he claims. A screenshot, taken on October 26, 2015, shows part of the exposed patients database.
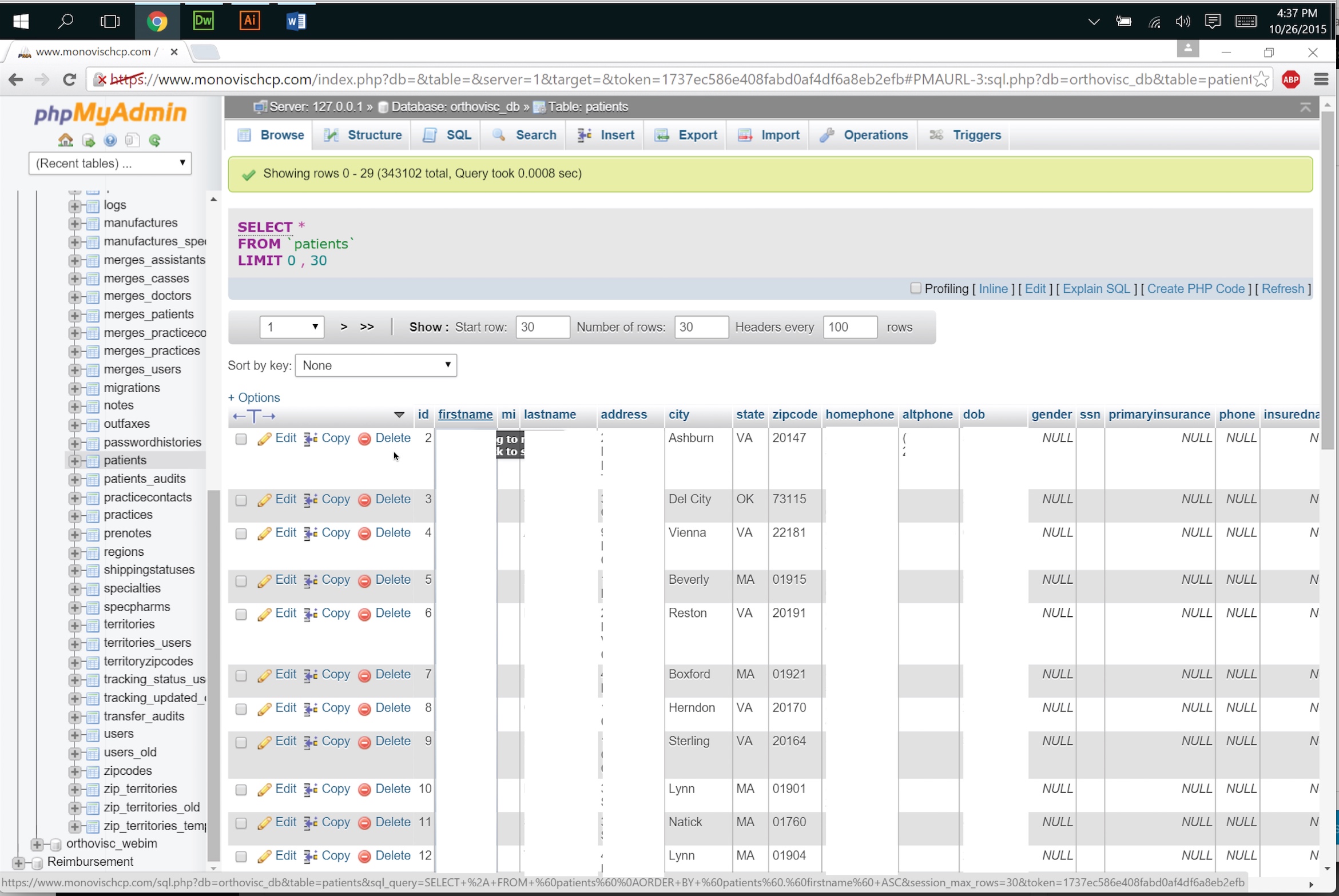
There were more than 350,000 records in the exposed database, including patients’ names, addresses, telephone numbers, date of birth, insurance information, and for some patients, Social Security numbers. DataBreaches.net is not suggesting, however, that the 220,000 figure reported by CoPilot is inaccurate, as many databases have duplicate records or test records.
The screenshot also reveals a security problem with the site’s SSL certificate.
DataBreaches.net was not provided with any evidence or witness statement that the data had been exposed beginning in May, 2015, and frankly, it is hard to imagine that the phpMyAdmin panel was exposed like that and no physician/client noticed it or had reported it. Perhaps the forensic report, which CoPilot has not publicly released, could clarify exactly when the database was exposed or accessible without the encryption and security CoPilot claimed it had, as the screenshot provides no evidence that there was any encryption at rest: all of the data were in clear text.
In any event, Witkowski informs DataBreaches.net that he downloaded the data, and began notifying some people of the problem. He did not notify CoPilot/CareMed directly, but according to him, one of the parties he alerted contacted Depuy Mitek. Witkowski tells DataBreaches.net that a Depuy Mitek employee, Amy Gladfelter, promptly called CoPilot’s IT Director, Tynan Markey, to alert CoPilot to the problem on October 26, 2015.
If his statement is true – if CoPilot was actually notified on October 26, 2015 – why did their notification letter claim that they first discovered the breach on December 23, 2015?
DataBreaches.net sent Depuy Mitek emails last week asking them to confirm or deny that Ms. Gladfelter notified CoPilot of the exposed database on October 26, 2015, but they did not reply. DataBreaches.net also sent CoPilot email inquiries last week asking them to respond to Witkowski’s claims that the data had been freely exposed on the internet beginning no later than May, 2015 and that they were first notified on October 26, 2015 by Gladfelter. They, too, did not reply.
But the difference in the length of the data exposure and the date of discovery are not the only parts of the notification that Witkowski has challenged. CoPilot’s notification to patients also claimed that “… the data was not accessible for downloading by the general public from the website.” And that, Witkowski tells DataBreaches.net, is a lie. According to Witkowski, anyone who went to the monovischcp.com site would have immediately seen the database and been able to download it.
Witkowski’s claim received some confirmation from one of the people he claims he notified on October 26, 2015. That individual, a friend of Witkowski’s, informed DataBreaches.net that when s/he typed in the URL Witkowski had provided, a file that “looked like an Excel file” with a lot of patient data appeared on the screen immediately.
When asked how many people he knew of who had viewed the patient data, Witkowski replied, “Currently, I’ve been made aware of at least 3 other people that viewed and accessed the information. I do have indications that more have as well.”
In its emailed inquiry, DataBreaches.net asked CoPilot why they claimed the data would not have been downloadable by the general public. They did not reply to that question, either.
So was Witkowski’s downloading of the data “unauthorzied,” as CoPilot claimed? Well, yes, in the sense that he had no explicit authorization to download it. Then again, there was no pop-up or any login required or notice that would prevent him – or anyone else, he says – from downloading it.
CoPilot’s notification indicates that they referred the matter to law enforcement. Nowhere, however, do they claim that law enforcement ever asked them to delay notification of the incident. So why did it take CoPilot more than one year to begin notifying patients, states, and HHS?
On December 23, 2015, Witkowski filed a complaint with HHS about the incident. At the time, he requested anonymity.
2016: CoPilot Variously Sues, Threatens, and Offers to Settle
In January 2016, CoPilot sought, and obtained, leave to file under seal a Does 1-4 suit in the Eastern District of New York (CoPilot Provider Support Services, Inc. v. Does 1-4). The case was voluntarily dismissed in November, 2016 without any complaint seeming to ever have been filed. It would have been interesting to see what the allegations actually were.
If CoPilot delayed filing any complaint because they hoped that the FBI would recommend prosecution of Witkowski as a criminal, they were likely disappointed. The FBI did investigate, and Witkowski tells DataBreaches.net that he cooperated with them fully. He showed DataBreaches.net a copy of text messages from September, 2016, in which Special Agent Peter Casson notified Witkowski that they were ready to return his Surface to him. Special Agent Casson also reportedly told Witkowski that they were closing their investigation and had found no evidence of any criminal intrusion.
DataBreaches.net contacted the FBI, who confirmed Witkowski’s claim. FBI spokesperson Kelly Langmesser told DataBreaches.net that the FBI has “closed the investigation into the alleged data breach of CoPilot and we are not bringing forth charges against any person.”
So by September 2016, there was no longer any FBI investigation and yet CoPilot still didn’t notify patients or state attorneys general. Why?
Witkowski believes that part of the explanation for their delay may be that throughout the year, they were trying to get him to sign a settlement agreement that might absolve them of responsibility for the breach and obviate the need for any notification.
In fact, as recently as January 25, 2017, they offered him a settlement that would give him $150,000 for acknowledging responsibility for the breach, withdrawing the complaint about the incident that he had filed with OCR on December 23, 2015, and not disclosing any further details about the incident or the company.To that end, they drew up a letter they wanted his lawyer to sign on his behalf:

Witkowski did not accept the offer. Nor is he concerned about threats of legal action, recently writing to their lawyers, in part:
Now, if anyone would like further clarity, feel free to call me at [redacted]. Otherwise, tell your chicken-shit clients that they get what’s coming to them and if I find out they are fucking with patient safety or privacy again, I’ll make sure they pay the appropriate price again.
But does HHS/OCR have authority to enforce any action on CoPilot? As it turns out, that’s another wrinkle in this case. Read more about what CoPilot claims and what some lawyers think in this companion article.
DataBreaches.net will continue to follow this case. If CoPilot or Depuy Mitek do respond to the inquiries sent by this site, this post may be updated.