Everyone has their own definition of a good day. Mine includes preventing breaches of patient medical information. Today qualifies as a good day, thanks to Project Insecurity.
OpenEMR is open source software for managing electronic medical records (EMR) and other practice management functions. According to Wikipedia, OpenEMR is one of the most popular free electronic medical records in use today. With so many entities using OpenEMR, the security of the software is obviously of significant concern.


Today, Project Insecurity, a London-based group, released their report on 18 vulnerabilities they found in OpenEMR v5.0.1.3. The team withheld release of the report until developers could address all of their findings.

When asked why Project Insecurity decided to code audit OpenEMR, CEO Matt Telfer told DataBreaches.net, “We’ve seen a lot of medical-related breaches in the media lately and it made us think about the entire transition from regular handling of medical records to them being dealt with electronically and the security implications of that, so we decided to look into EMR/EHR systems. After some googling we found that OpenEMR was the most widely-deployed open-source electronic medical record application on the internet. And the fact that it’s open source meant that we could test it without any negative legal implications.”
Findings
So what did Project Insecurity find? You can read their full report on their web site. I’ve pulled out just two of their findings to give you a sense of how serious some of the vulnerabilities appeared to be.
One of the vulnerabilities the team discovered would enable an attacker – or anyone for that matter – to bypass the patient portal authentication. They report that bypassing authentication was easy: an attacker would merely have to navigate to the registration page and modify the requested url to access the desired page. They provide a list of all of the pages in the portal directory that would then be accessible to the attacker. This screenshot is a redacted patient profile (redacted by them) as part of their walk-through on how the vulnerability could impact patient privacy and data security.
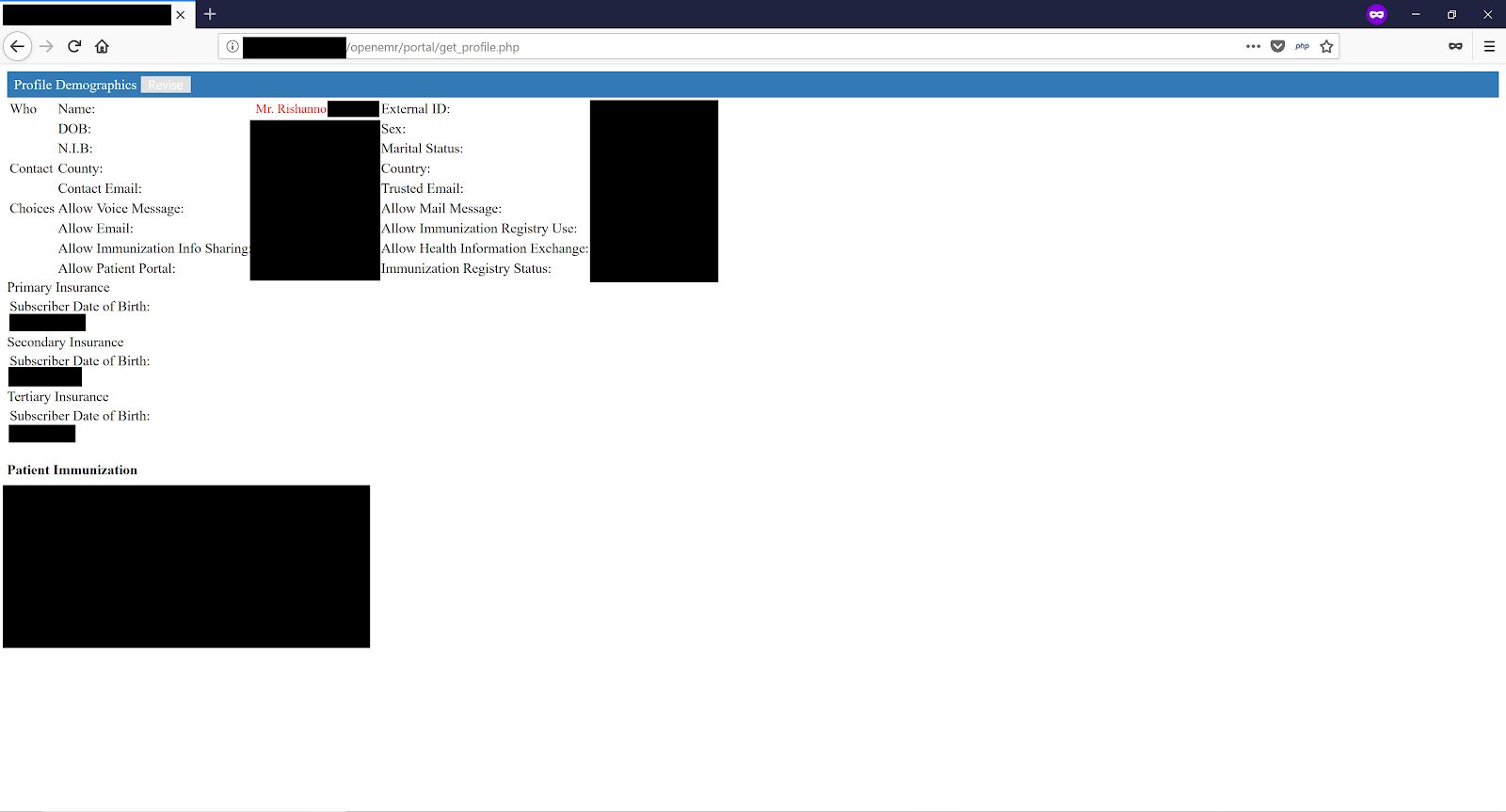
The team also created a video to help illustrate what Manny Mand, Security Operations Manager, described to DataBreaches.net as a realistic attack against an OpenEMR web application:
When I asked Mand to comment on what he thought was their most significant finding, he said, “The biggest thing would be the significance of the authentication bypass, it’s so simple but it can lead to viewing sensitive information from customer’s records.

Cody Zacharias, Red Team Lead, agreed, adding, “The authentication bypass vulnerability was the most significant vulnerability our team discovered because not only does it open the web application to SQL injection, but also it gives the attacker the ability to view and tamper with a person’s records affecting both the privacy and the integrity of the EMR.”
Translating all that into layman’s terms, Project Insecurity CEO Matt Telfer tells DataBreaches.net, “Some of the information which could be stolen as a result of this flaw includes patient demographics, all Electronic Medical Records, prescription and medical billing information, appointment schedules, and more. There are almost 100 million patients’ records stored in total, with over 10 million of those being within the USA.”
DataBreaches.net reached out to OpenEMR for comment. Brady G. Miller, CEO of OpenEMR.org sent the following statement:
The OpenEMR community is very thankful to Project Insecurity for their report, which led to an improvement in OpenEMR’s security. Responsible security vulnerability reporting is an invaluable asset for OpenEMR and all open source projects. The OpenEMR community takes security seriously and considered this vulnerability high priority since one of the reported vulnerabilities did not require authentication. A patch was promptly released and announced to the community. Additionally, all downstream packages and cloud offerings were patched.
It’s nice when the system works as it should: responsible disclosure and rapid response.
While the first vulnerability appeared to be the most serious, a second vulnerability the team discovered would “enable an attacker who authenticated in the patient portal to make a crafted request to upload any type of file, including php, to the system. This could later be used by the attacker to achieve code execution and escalate privileges.”
So anyone who exploited this vulnerability might be able to corrupt patient records, delete patient records, or just access and download the entire patient records database to sell it on the dark web somewhere.
Project Insecurity reports that they filed the appropriate CVEs for their findings.
Kudos to Project Insecurity for their volunteer efforts to help make OpenEMR a more secure option for patient records and practice management. And from the preview they gave me of some of their other projects, you will definitely want to stay tuned to see what other vulnerability reports they will be issuing in the near future. You can also follow them on Twitter at @Insecurity.
Very cool!
Isn’t it? I love reporting things like this!