That Pacific Union College (PUC) experienced a cyberattack is not a secret. The college even posted a notice on their website on April 7 stating that they were experiencing “Additional complications relating to the ongoing cybersecurity issue, which has recently affected some of our internal networks, phone systems, and web services. The remainder of the notice provided the status of various types of systems and services and assured the community of updates “as new information becomes available.”
But the next update on the website wasn’t until May 3, when they wrote )emphasis added by DataBreaches):
Several weeks ago, Pacific Union College experienced what we now know was a targeted ransomware attack. Federal authorities were contacted, and other cybersecurity teams were recruited to work with our IT department.
They have been diligently working around the clock to mitigate the situation and also to restore and protect our systems for the future. We want to reassure you that we do not have evidence that personal information has been compromised.
We know that many of you have questions regarding services not working, websites being inaccessible and financial awards not yet sent. These have all been greatly affected by the ransomware attack.
These cyberattacks on higher education institutions have unfortunately increased in recent years. We sincerely apologize for the inconvenience and delay this has caused. We fully expect that our systems will be operating normally within the next few weeks. In the meantime, please know our faculty and staff are committed to helping you navigate all your academic and financial processes.
There have been no updates since then.
While PUC has ignored or stonewalled inquiries from this site, the Trigona ransomware group has provided DataBreaches with additional details on the incident and recently added PUC to their leak site. Their listing claims that anyone who buys the data will have access to “120 GB of the University`s confidential data, including employees’ and students’ personal data, commercial contracts, NDAs and other confidential high-cost info.”
In response to questions from DataBreaches, Trigona filled in some of the blanks in PUC’s notifications. According to Trigona, PUC was attacked on March 27. “We had been in their network 1-2 weeks before that, transferring their files to our clouds,” a spokesperson for the group informed DataBreaches.
Trigona is asking for $200,000.00 for the data. If the school pays them, they claim they will delete all the data and give them a report on how they were able to access them. If the school doesn’t pay, anyone who is willing to pay can buy the data from Trigona. Unlike ransomware groups that leak the data of victims who do not pay, Trigona auctions off or sells the data. One consequence of an approach that sells the data rather than leaking it is that the victims may never find out exactly what data the threat actors had acquired and individuals may not know if their personal or protected health information is in criminal hands.
When asked whether PUC had ever contacted them at all to negotiate the ransom demand, Trigona’s spokesperson stated:
They contacted us and negotiated for a month. They were shown sample data and a listing, but they were not impressed. Their network was encrypted twice.
In this case, then, PUC probably does have some idea of what files the attackers acquired, depending on how representative the sample was or how complete the file list was.
Employee and Student Personal Information Compromised
Trigona provided DataBreaches with a sample of files that included files with some personnel data as well as some files with students’ personal and financial information.
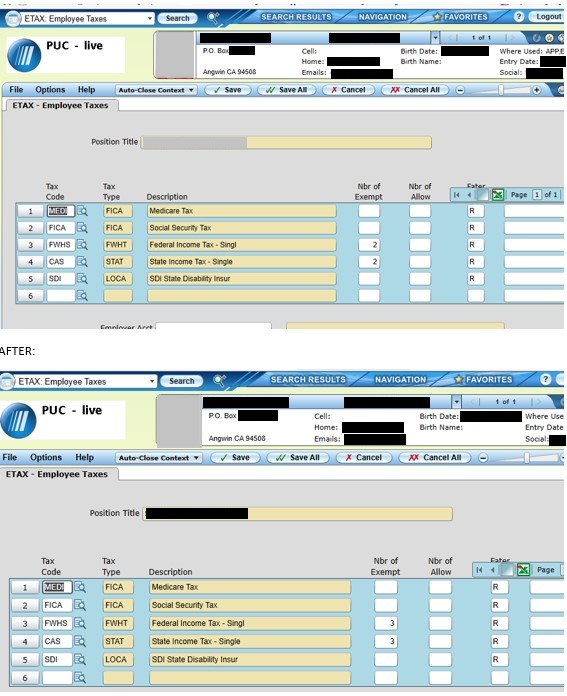
The image of the ETAX form, shown above in redacted form, was from 2010, which means that the college likely has former employees to notify and offer credit monitoring and identity restoration services to because ETAX forms contained the employee’s picture, name, address, date of birth, full Social Security number, and what taxes with what exemptions to take from the employee’s paychecks. DataBreaches does not know what payroll or personnel information the attackers might have on current employees.
Some of the student-related files DataBreaches reviewed contained even greater amounts of personal and financial information, as well as parents’ personal and financial information in some cases. Financial aid applications and related files are multi-page forms that collect a significant amount of personal information.
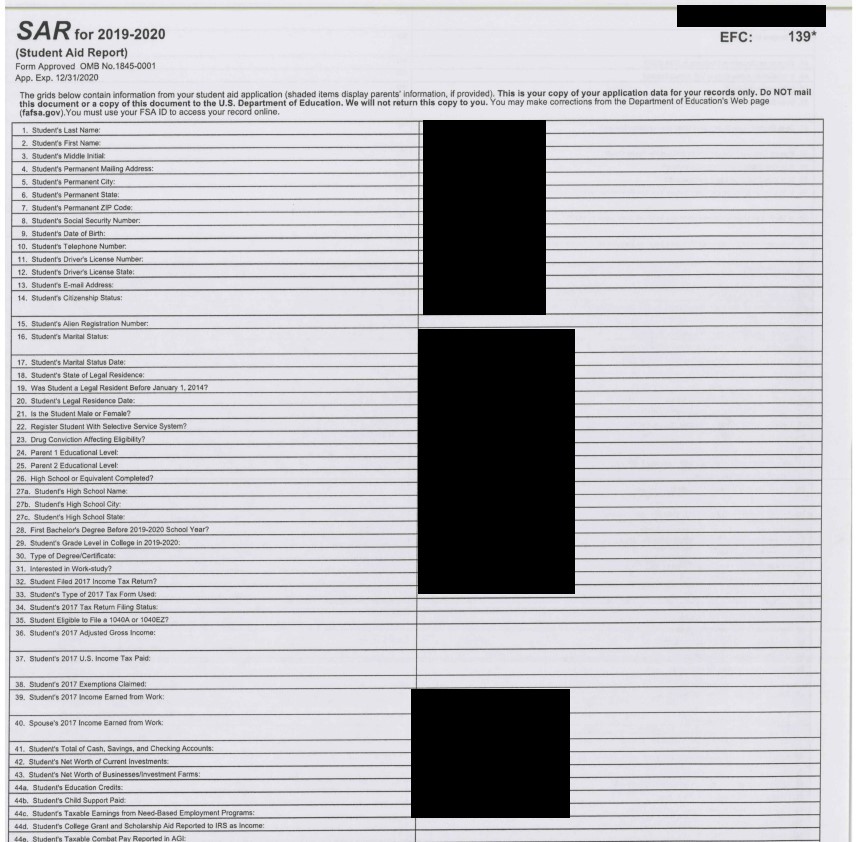
The second figure, above shows just the first portion of an 8-page Student Aid Report (SAR) from 2019-2020 that is related to financial aid. The SAR reports a lot of personal information on the student, and also asks about taxes they have paid, whether they have had any drug or criminal convictions, their marital status, and their plans. But the detailed record also includes information on their parents, including names, their incomes, taxes paid, etc. Inspection of other files with filenames that included “FAFSA Verified” revealed multipage files that were each 22 pages in length with detailed tax return data provided by the IRS on parents of student applicants. FAFSA stands for “Free Application for Federal Student Aid.”
DataBreaches saw dozens of names of students who had sought financial aid in the sample provided to this site. As DataBreaches has reported in other cases, applications for federally funded student financial aid are to be secured and protected under the Gramm-Leach-Bliley Act (GLBA).
In addition to personnel and student information, DataBreaches also saw a few files with detailed information on donors, including their names, addresses, email and phone number, date of birth, partial SSN, marital status, spouse information, schools, employment information, and histories of donations and how they paid, etc. There did not appear to be any financial account information or full SSN, but the information could potentially be misused to scam these donors because anyone calling them would have detailed knowledge of the past donations they had made.
“We do not have evidence that personal information has been compromised”
Given the fact that Trigona acquired personal information, and it has been more than two months since the first attack, why hasn’t PUC corrected or revised its published claim of May 3, “We want to reassure you that we do not have evidence that personal information has been compromised.”
DataBreaches contacted PUC on May 21 by site contact form and email. DataBreaches contacted PUC again via email on and again on June 4. Other than an auto-acknowledgment on May 21, they have not replied at all.
At some point, will PUC tell employees and students that they did negotiate with the attackers for a month and knew that personal information was compromised but decided not to pay? Will PUC tell them why they decided not to pay and why it took them so long to disclose that they knew personal information had been compromised?
To be clear: DataBreaches is not criticizing PUC for any decision not to pay ransom to threat actors. DataBreaches is, however, criticizing PUC for its lack of transparency when it already knew personal information had been compromised.
Where is the Federal Oversight?
With all the colleges and universities that have been the victims of cyberattacks, and all the student financial aid-related files that have been stolen by now, should we be surprised that we have not heard of any enforcement actions by the Federal Student Aid / U.S. Department of Education and the Federal Trade Commission (the latter has the authority to enforce GLBA)? These are financially related files, and as such, have higher mandated protection than general education records under FERPA.
Should colleges and universities with inadequate security for student financial aid still be allowed to participate in federal financial aid programs? It would be a tremendous hardship for students — and colleges who would lose enrollments — if the government limited schools with a history of poor data security until they demonstrate adequate or reasonable security for financial aid records, but is that what needs to happen?
Maybe it’s time to contact FSA/DOE and ask how many reports they have received of student financial aid forms being stolen in cyberattacks and what FSA is doing these days in the way of monitoring and enforcement of security standards. Are they even being informed of all these breaches?