The education sector has always been a relatively easy target for cybercriminals. One group in particular — Pysa — earned a reputation for its ransomware attacks on schools. Despite analyses and alerts in March, 2021 by threat intel firms and the U.S. government indicating that Pysa was a major threat to the education sector in the U.S. and U.K., school districts continued to fall prey to Pysa, including an Indiana k-12 district in April 2021. In June 2021, as U.K. schools continued to fall for the phishing lures and brute-force Remote Desktop Protocol attacks that Pysa favored as initial access techniques, the U.K.’s NCCSC published yet another report, noting:
The NCSC has previously highlighted an increase in ransomware attacks on the UK education sector during August/September 2020 and again in February 2021. As of late May/June 2021, the NCSC is investigating another increase in ransomware attacks against schools, colleges and universities.
That same month, DataBreaches reported on an attack on a New York k-12 district that had been claimed by Pysa threat actors. In August, DataBreaches reported on six more k-12 school districts that had fallen prey to Pysa. In October, 2021, we added two more k-12 districts to our coverage.
But there were other education sector victims claimed on Pysa’s dark web leak site — victims who were named but for whom no data had been dumped. There were no updates to the site for months, and then Pysa’s site disappeared altogether.
In this report, we report on non-U.S. schools and one U.S. school that were listed by Pysa as victims. In only two cases had Pysa leaked data before the site was shuttered. We also report on one non-U.S. university that did not appear on Pysa’s site at all, but was reported to be a Pysa incident by the media citing a university source.
For each of the claimed victims, we searched the victim’s website to see if there were any notices on the site concerning any incident. We also searched archive.org, ran a google search for news and other possible coverage, including any mentions on Twitter. Dark web markets and leak sites were also searched for any indication of a breach or leak. If nothing was found at all, Freedom of Information requests were filed with the Information Commissioner’s Office for the U.K. schools. Each school was also contacted via email to ask for confirmation and information on any breach.
Findings
Odyssey Trust for Education (U.K.)
Odyssey Trust for Education is the administrator of Townley Grammar School and Henry School. On June 8, 2020, the trust announced a data security breach. According to their notice, an email account had been compromised between March 27 and June 3, 2020. Their preliminary investigation suggested that mainly trust suppliers were involved, but they notified the Information Commissioner’s Office (ICO) and took their guidance.
On May 13, 2021 — almost one year after the school’s announcement — Pysa added Townley Grammar School to their leak site and dumped 17 GB of data. The leak appeared to include both student and employee data. Some files were labeled “confidential,” while other files contained passports, disciplinary investigations, mailing lists, parent contacts, and other files.
Because the school’s 2020 notice stated that the Trust had notified the ICO, DataBreaches wrote directly to Townley to ask some follow-up questions. They replied to our inquiries by confirming that they had not paid any ransom to Pysa and that had notified a total of 3,609 students and employees of the incident.
Ruskin Community High School (U.K.)
Ruskin Community High School was also added to Pysa’s leak site in May 13, 2021, with the threat actors dumping 2 GB of data. The data appeared to include some limited employee/personnel information, but also personal and in some cases, sensitive, information on students that included their names, pictures, and special education needs and plans.
Ruskin announced the attack as a ransomware incident on May 13, 2021.
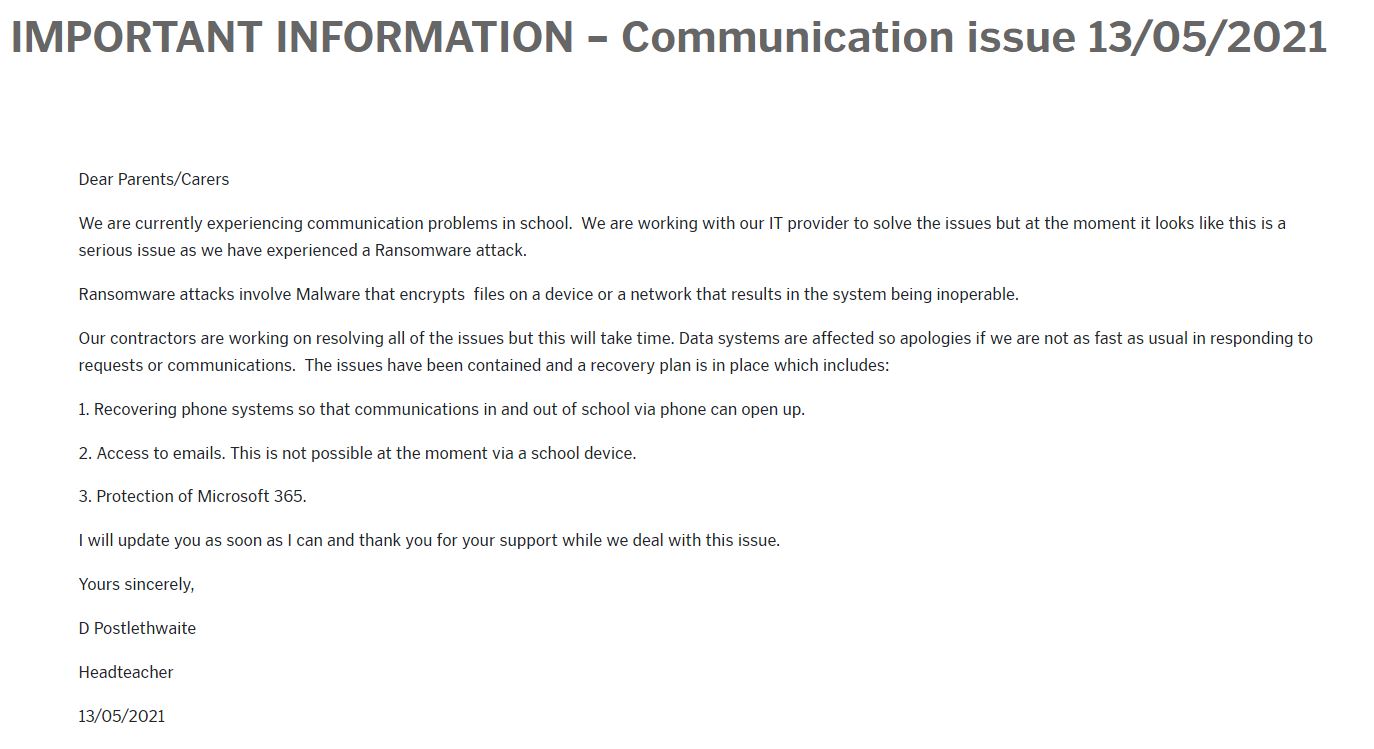
Databreaches.net sent email inquiries to Ruskin Community High School about the attack but received no reply. The ICO responded to our Freedom of Information request by noting that they had received a data breach report from Ruskin High School in 2021. The report provided by Ruskin High School to the ICO had indicated a ransomware attack and that no ransom had been paid in connection with this incident Ruskin had reported that 87 staff members and 720 students were notified about the incident.
The Skinners Kent Academy (U.K.)

The Skinners Kent Academy appeared on Pysa’s leak site in November 2021, but no data was ever leaked on that site. Our research discovered that there had been a statement on the academy’s site on June 10, 2021 that was archived at archive.org. The statement began:
On Wednesday 2 June 2021, we learnt that The Skinners’ Kent Academy and Skinners’ Kent Primary School servers had been attacked by hackers who have stolen and encrypted Trust data. We are currently working with our data protection company, the police, Action Fraud and the National Cyber Security Centre to investigate this attack and restore all affected systems.
There is a detailed FAQ and HR addendum to the statement, as the unnamed attackers who we later learned to be Pysa significantly impacted the school’s ability to function and the protection of personal and sensitive data. The school explains, in part:
No data that was held in the Cloud has been compromised but both servers at the Trust were hacked, some of it stolen, some of it encrypted. Data stolen includes; a wealth of teaching resources, school trip information, policies, human resources files and a significant amount of staff data, some student data including medical information and data pertaining to our iPad scheme. Data encrypted (and therefore not accessible to the school any more) includes our management information system, which contains the bulk of contact details for parents. Therefore, it is the latter that we have had to ask parents to re-submit to the Trust.
Details of hirers, contractors and suppliers were involved but this did not include their financial details.
The FAQ notes that it would be prudent to inform banks that details may have been stolen:
Yes. It would be very wise to let your bank know that your bank details may have been taken. Whilst third parties such as Squid do not seem to have been affected it would be very wise to let your bank know that your bank details may have been taken. The details of bank accounts may have been accessed through details taken for the iPad scheme for example.
BBC reported on the incident at the time.
The school responded promptly to DataBreaches’ follow-up questions, responding that they had never had any subsequent evidence of student data or employee data being leaked on the internet or misused. They also explained that they notified all staff, parents/carers, Governors, and other relevant stakeholders, including some suppliers. The ICO, DfE, ESFA, police, and NCSC were also notified, as were approximately 10 former or current employees.
Woodchurch High School (U.K.)
Woodchurch High School was also listed on Pysa’s leak site but no data were leaked on their site and we could find no confirmation of the claimed breach anywhere. Woodchurch did not respond to email inquiries from DataBreaches, but a Freedom of Information request to the ICO revealed that the ICO did receive breach reports from the school in 2021. The ICO’s office processed the reports as two separate personal data breach cases. According to the ICO’s office, both cases indicated ransomware attacks. The reports did not indicate whether any ransom was paid.
According to the information submitted to the ICO by Woodchurch High School in both cases, data subjects were not notified about the incidents, and there is no mention of any students or employees being notified. Without having seen any data from the attack, and with no response from the school, it is not clear whether notifications to students or employees would have been needed or appropriate.
Westvale Academy (U.K.)
Westvale Primary School was also named and listed on Pysa’s leak site without any data leak. DataBreaches filed a Freedom of Information request with the ICO for any breaches reported to them in 2021 by Westvale Primary. The search returned no results, but a response from Westvale Primary School by Tracy Atherton, School Administrator Westvale Primary, made us realize that perhaps we had been querying the wrong school. She wrote:
This incident occurred at Westvale Primary School in Yorkshire.
Initially we thought it was our school although no ransom was requested. After the police investigated they confirmed that it was Westvale school in Yorkshire that had been the target of the Pysa attack in September 2021.
With that correction, DataBreaches then sent requests to Westvale Academy and to the ICO with the name of Westvale Academy. The school never replied, but the ICO responded that they had received a data breach report on November 12, 2021. Because the case is still under investigation, however, they could not answer our other questions about the report.
Cyprus University of Technology (CY)
Cyprus University of Technology (Τεχνολογικό Πανεπιστήμιο Κύπρου) was also listed on Pysa’s leak site without any data. Databreaches.net sent an inquiry to the university via email and also contacted the Cyprus data protection commission. Michael Kitromilides responded for the DPC:
The practice followed by our Office is to publicize the number of yearly data breaches notified to our Office, and information about selected cases for which a Decision has been issued by our Office. The summaries and/or the full text of such Decisions are published on our Website at the Decisions section (Γραφείο Επιτρόπου – Αποφάσεις) and the Annual Reports section (Γραφείο Επιτρόπου / Ετήσιες Εκθέσεις) (only available in Greek).
Our Office did not publicize any Decision regarding a data breach at the Cyprus University of Technology.
Because the university did not respond to multiple requests, we do not have any information on this claimed incident.
University of Liechtenstein
Although Pysa never listed the University of Liechtenstein on their leak site, the university was reportedly a victim in August 2021. As reported by Inside IT at the time, the university was unable to initially determine if any data had been exfiltrated. In October 2021, the university issued a statement:
We are back: uni.li is online again.
With a picture of the cheering students from the graduation ceremony, we are back. After a ransomware attack in the summer, the University of Liechtenstein website www.uni.li is now back online.
The notice made no mention of whether any student or personnel data had been stolen. Databreaches.net sent an email to the university to find out more about this incident. An inquiry was also sent to the data protection authority of Liechtenstein. Dr. Marie-Louise Gächter, Head of the Data Protection Authority, responded that the university had met obligations under article 33 of the GDPR:
Art. 33 GDPR concerns the notification of a personal data breach to the supervisory authority. This is an internal process and the information received by the Authority is not public. All we can say is that the University of Liechtenstein respected its obligations under Art. 33 GDPR.
The university never responded to DataBreaches’ inquiries.
Thunderbird Adventist Academy (U.S.)
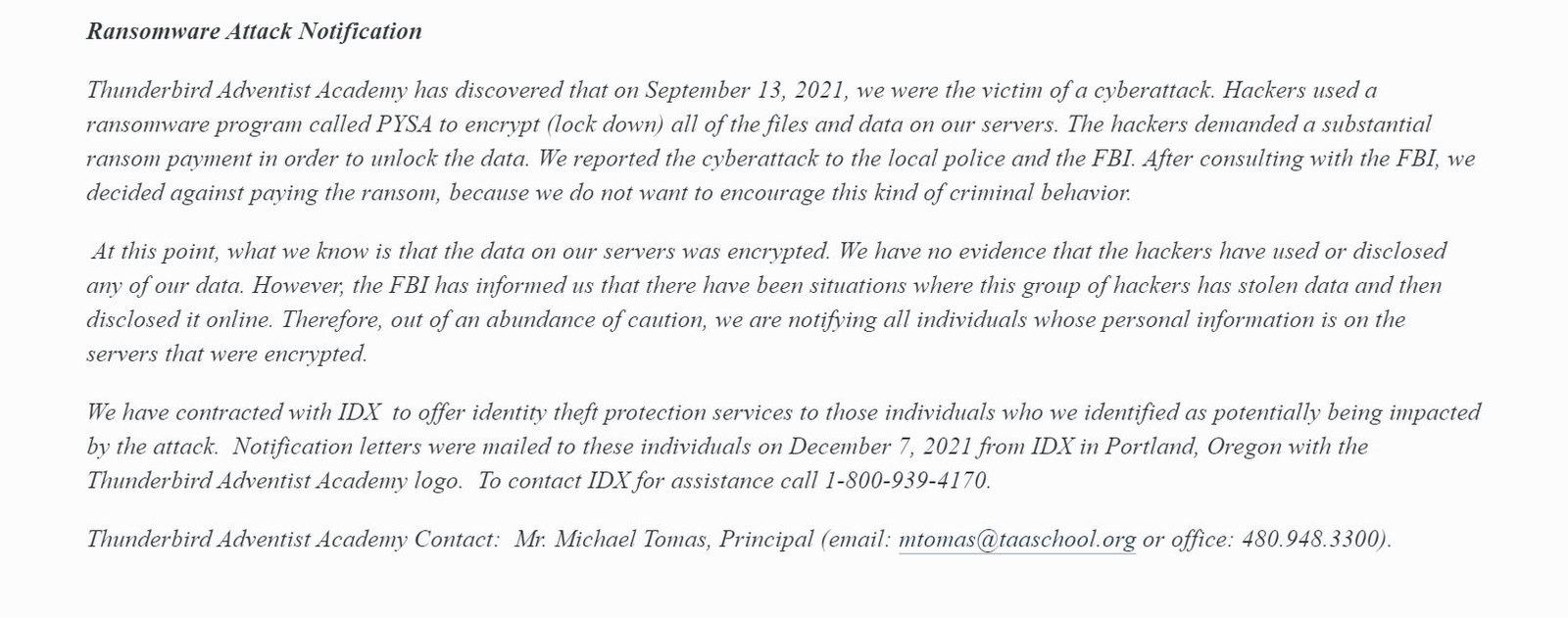
Thunderbird Adventist Academy was also listed on Pysa’s site but without any data leaked publicly. DataBreaches was able to locate an archived copy of a notice on their site that begins:
Thunderbird Adventist Academy has discovered that on September 13, 2021, we were the victim of a cyberattack. Hackers used a ransomware program called PYSA to encrypt (lock down) all of the files and data on our servers.
DataBreaches sent inquiries to Thunderbird to ask about whether there were any further issues, but received no response.
Lucton School (U.K.)
Lucton School was also added to Pysa’s leak site without any data leak. When Lucton did not respond to inquiries from DataBreaches, we filed under Freedom of Information with the ICO. The ICO’s office responded to our inquiries, writing, in part:
I can confirm that we have some information within the scope of your request.
Lucton School informed us of a data breach incident on August 25, 2021. This was investigated and the case was closed on January 6, 2022 with an outcome of “No further action”.
The ICO’s response indicated that the incident was reported to ICO as a ransomware response but the school’s report made no mention of whether any students or employees were notified about the incident.
Where are the Data?
DataBreaches’ research confirmed that these nine incidents were linked to Pysa threat actors, but with the exception of the incidents where Pysa leaked data on their leak site, we were not always able to discover whether personal information of students or personnel had been exfiltrated. Nor was it easy in many cases to learn whether the schools had notified those who data may have been accessed or stolen.
And what happened to the data presumably stolen in these attacks? DataBreaches found no evidence of any data from these incidents on any leak sites where such data might typically be found for sale or download. Because many schools did not respond to inquiries, nor do we know if they ever learned of any evidence of misuse.
So have students’ and personnel’s personal information been shared or sold privately? We do not know, but will continue to keep an eye out for it. In the meantime, DataBreaches reminds schools that Pysa was not the only group targeting schools. Vice Society threat actors are still active and adding schools to their leak site, and other groups also occasionally attack schools.
****
For more information on Pysa, see:
- Pysa script shows exactly what files they are after
- Cybereason analysis: September 2021
- Deep Dive Into PYSA Ransomware – December 2021 – Kroll
- PYSA Ransomware Group In-Depth Analysis – April 2022 — Prodraft
Research for this report was conducted by @Chum1ng0. For any questions, contact him via Twitter or via email to [email protected]. Writing assistance and editing for this article provided by Dissent.