Some ransomware groups have pledged not to attack healthcare facilities. Vice Society is not one of them, as their recent attack on a Spanish hospital reminds us.

Amaveca Salud provides a number of in-patient and outpatient services and therapies. Last year, they inaugurated a private hospital, Hospital Centro de Andalucia in Lucena, Spain.
When the hospital was the target of a ransomware attack by Vice Society threat actors in mid-December, Amaveca Salud opted not to pay any ransom demands.
The incident was first revealed this week when Vice Society dumped data and added them to their leak site.
DataBreaches.net sent multiple email inquiries about the alleged attack to Amaveca Salud. They did not reply to any of them but then issued a notice on their website on January 11 that stated that a cyber incident had occurred involving the hospital. The notice did not mention impact to any of their other units.
A machine translation of their notice includes, in part:
Despite the measures outlined above, this cyber incident has occurred, which, due to the rapid actions taken, has not compromised the normal operation of the center, which continues to focus on the care of its patients. The forensic analysis work, which is in progress, does not yet allow us to conclude the exact details of the amount and types of data stolen, however, as soon as this analysis is completed, we will report in detail the final scope.
AMAVECA SALUD has reported the facts to the National Police, and proceeded to the notification of the security breach to the Spanish Data Protection Agency.
After reading Avameca’s statement that suggested that only the hospital was attacked, DataBreaches.net sent an email inquiry to Vice Society to confirm whether they had hit only the one hospital’s system or if they had hit Avameca Salud’s central servers. Vice Society’s spokesperson replied:
We attacked 2 domains, some of the backups were not affected, they were able to restore their network quickly. Anyway, they knew about the documents and about us. The documents were downloaded from both domains.
At this point, then, Avameca Salud likely needs to analyze all the files in the data dump to determine what notifications may be required under the GDPR and Spain’s own national data protection laws.
As viewed by DataBreaches.net, the data dump consisted of 127 GB of compressed files. Some of the files contained internal documents such as invoices, budgets, templates, and commercial contracts. But there were also some files relating to employee information such as COVID-19 status, photocopies of employees’ DNI (Documento Nacional de Identidad), resumes, professional fees, and a list of contracts.
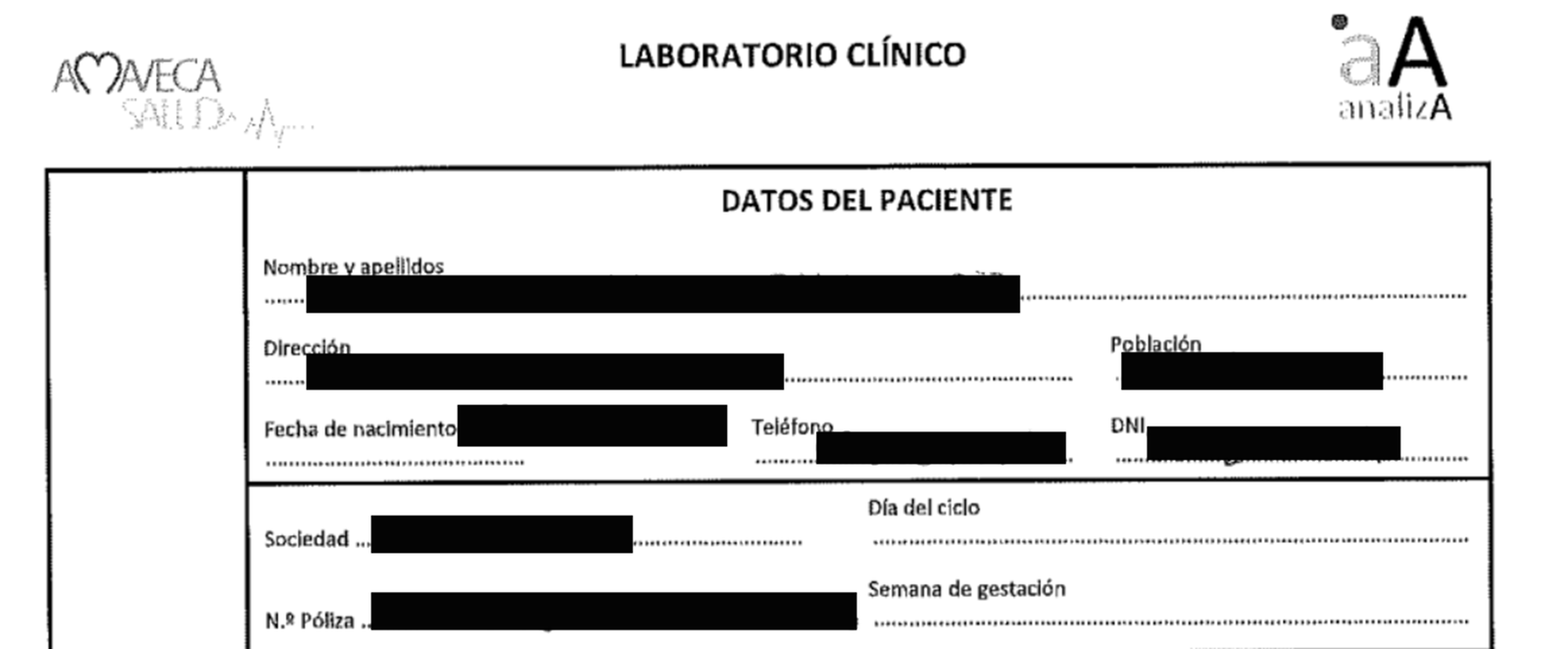
Some limited patient-related files were also spotted in the data dump, such as results of testing for COVID-19, patient consent forms for treatment, some medical reports or records, mammography appointments, and outpatient visits. Some forms contained patients’ demographic information as well as policy information and specific medical information, such as the redacted laboratory record below:
Vice’s Other Victims in the Healthcare Sector
Vice Society is relatively new to ransomware, and not much has written about them other than their ransomware is thought to be related to the HelloKitty ransomware and that they are nimble in adapting quickly to new possible attacks (such as PrintNightmare).
In addition to Avameca Salud, other healthcare facilities that they have attacked include:
- Barlow Respiratory Hospital
- United Health Centers of San Joaquin Valley
- Eskenazi Health
- Waikato District Health Board
- Centre Hospitalier D’Arles
These are the ones we know about, anyway, as they did not pay ransom or disclosed publicly. We have no idea how many other healthcare facilities may have been attacked and chose to pay and try to cover up the attack.
Reporting by Chum1ng0; editing by Dissent.