Australia has ordered an Australian national, David Kee Crees, extradited to the U.S., where he faces 22 counts involving hacking, fraud, and aggravated identity theft. Two of Crees’ better-known aliases were “Abdilo” and “DR32.”
“Abdilo”
DataBreaches started reporting on Crees in 2015 when he was known to this site as “Abdilo.” At the time, he targeted so many educational institutions that this site reported on him about a dozen times. But his hacks of educational institutions were not his only activities; he was also attacking Australian businesses and government agencies. In those days, however, his attacks on government agencies did not cause severe damage as he attacked web applications that contained either public information or information that would be made public.
In December 2014, Brian Krebs reported on abdilo in a post about Lizard Squad, the group that spoiled Christmas 2014 for many people by launching a DDoS attack on PlayStation Network and Xbox Live. Discussing abdilo, Krebs wrote, in part:
It’s worth noting that the individual who registered LizardStresser is an interesting and angry teenager who appears to hail from Australia and uses the nickname “abdilo.”
In the comments under the post, a commenter named abdilo as “David Crees” and mentioned other aliases of his: Notavirus, Surivaton, and Grey Hat Mafia’s Bitch. His Surivaton alias most recently appeared on March 1 of this year on Github for a “RemoteBGPHijack” repository.
Although abdilo was a bit of an energizer bunny in his hacking back then and even live-streamed his SQL injection hacks, he was either unconcerned about getting arrested or had poor OpSec. In early 2015, Abdilo had already been raided by the Australian Federal Police, but even that didn’t deter him.
What happened after that is not as well publicly documented as his earlier activities. In fact, in 2018, this blogger even tweeted a query as to whether he was still around or active. Abdilo got in touch with DataBreaches, but didn’t say much about what he was involved in or doing at that point.
Some open source searches revealed that in 2019, Crees registered a business in Australia that he called SQLI. It was registered at an address in Oaklands Park. In 2021, Crees registered a second business that he called ROOTKIT. It was registered at an address in Collinswood. Court filings by the U.S. allege that these businesses were used for money laundering purposes.
 |
 |
Although DataBreaches lost track of abdilo, he was reportedly very busy. In 2021, the U.S. presented a case to a grand jury in Colorado. On December 7, 2021, the grand jury indicted Crees on 22 counts. The case arose from an investigation by the U.S. Department of Homeland Security, Homeland Security Investigations (HSI) and covered a period from approximately June 2020 to July 2021. During that time, DHS/HSI used undercover agents who made deals with Crees and investigated his claims.
In all of the incidents described below, Crees was dealing with one undercover agent who claimed he was representing a buyer or potential buyer. A second undercover agent would sent payments to Crees as part of the deals being made.
Consistent with U.S. policy in filing indictments and documents that will be made public, the names of the victim entities are not included in the indictment and affidavit in support of the extradition request. Only general descriptions of the entities are provided in the court filings, although Crees will be informed of the actual identity for defense purposes.
Note: The bulk of this report is based on the indictment by the grand jury in Colorado and the affidavit in support of the extradition request. These documents are not publicly available in the U.S. at this time and are still under seal here. They were obtained from the Australian court that heard and ruled on the extradition request, with the understanding and agreement that DataBreaches would not reproduce the filings in any publication. Any images included in this article were obtained by DataBreaches via OSINT research and not from any court documents. Typos in quoted statements by DR32 are as in the court filings.
Who Is David Crees?
Crees is a 24 year-old Australian national who at times, has used his real name on internet forums and platforms. The pictures of Crees in his Twitter header, below, match other photos of him obtained by the U.S. government. Crees was very engaged in biohacking and would post pictures of his hands and arms to show implanted LEDs. The photos he posted of himself were used by law enforcement to help confirm his identification.
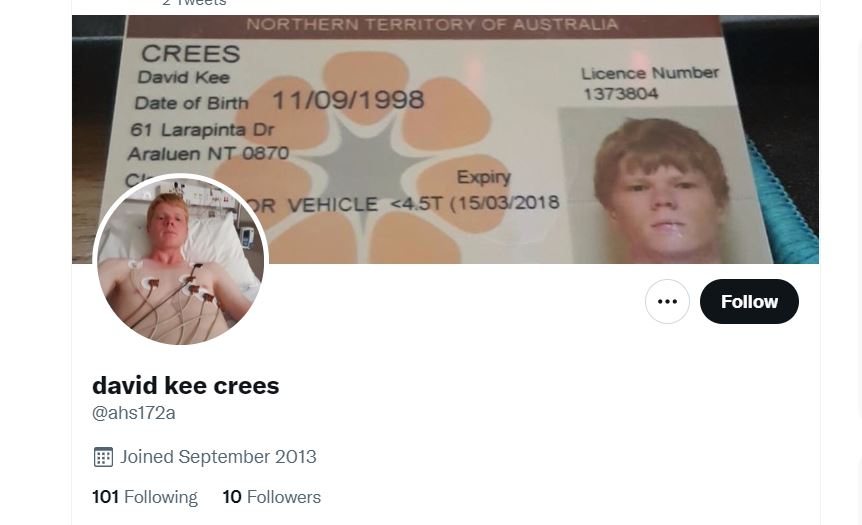
U.S. law enforcement did not find it terribly challenging to identify DR32 as Crees. In his conversations with the undercover agent, Crees told the agent that he lives in Adelaide, Australia and used to live in Alice. On another occasion, Crees mentioned that he had acquired a famous email address. When the agent received an email from that address, the name on it was “David Crees.”
But there was more. Because Crees was so involved in biohacking and posted on a manufacturer’s forum, the government was able to get the manufacturer’s records as to whom and to where they had shipped items Crees had posted about. It didn’t hurt that Crees had actually posted as “Abdilo/David Crees.” The manufacturer’s records show that they had shipped to David Crees at 8 Redmond St Unit 4, Collinswood, South Australia. That is the same address where Crees had registered his “Rootkit” business under his real name (see figure above).
In addition to the aliases mentioned above, Crees did have other aliases, some of which were shared.
Crees Charged with 22 Counts
As an overview of what Crees has been charged with, the following is a summary of the 22 counts he is facing:
| Counts | Description |
| Counts 1-7 | Fraud and related activity in connection with computers, and aiding and abetting, in violation of Title 18, United States Code (U.S.C.), Sections 1030(a)(2)(C), 1030(b), 1030(c)(2)(B)(i), and 2, which carries a maximum penalty of five years in prison for each count; |
| Counts 8-14 | Fraud and related activity in connection with computers, and aiding and abetting, in violation of 18 U.S.C. Sections 1030(a)(5)(A), 1030(b), 1030( c )( 4)(A)(i)(I),20 and 2, which carries a maximum penalty of five years in prison for each count; |
| Count 15 | Money laundering, in violation of 18 U.S.C. Section 1956(a)(I)(B)(i), which carries a maximum penalty of 20 years in prison; |
| Count 16 | Fraud and related activity in connection with identification documents, in violation ofl8 U.S.C. Sections 1028(a)(7) and 1028(b)(2)(B), which carries a maximum penalty of five years in prison; |
| Count 17 | Fraud and related activity in connection with access devices, in violation of 18 U.S.C. Sections 1029(a)(2), 1029(b )(1 ), and 1029( c )(1 )(A)(i), which carries a maximum penalty of 10 years in prison; and |
| Counts 18-22 | Aggravated identity theft, in violation of l 8 U.S.C. Section 1028A, which carries a maximum penalty of two years in prison for each count, to be served consecutively to any other prison term imposed. |
DataBreaches will not attempt to calculate the maximum prison terms Crees might be facing because even if he was convicted on all counts, some sentences would run concurrently while others (like Counts 18-22) would run after other sentences had been served. DataBreaches also points out that even when numbers are calculated by those who know how to calculate them, in reality, most cases settle for a plea on one or two counts.
In the incidents described by the government, summarized later in this post, Crees allegedly engaged in hacking, then advertised what he accomplished by offering access or source code or data for sale. In some cases, he also allegedly engaged in selling stolen credit card information. He is also accused of money laundering, which he allegedly actually admitted to and described to an undercover agent this way (it appears the undercover agent’s responses were omitted from this):
“time to slowly convert this all into xmr, then launder it through my business”
“then i did my taxes”
“no legit”
“btc > xmr > xmr> xmr> xmr> btc> exchange> business> bank + tax”
Between July 16, 2020 and January 24, 2021, the first undercover agent made arrangements to pay DR32 $250,000 for five purchases for access to victims’ networks or exfiltrated data. The payments were sent to Crees by the second undercover agent, and the government was able to trace the transactions, as explained in a foot note:
“Specifically, in tracing DR32’s digital currency transactions with the money paid to DR32 for the hacks of Victim-1, Victim-2, and Victim-3, investigators used law enforcement software that organizes bitcoin transaction data from the publicly available bitcoin blockchain ledger. For each transaction, investigators followed the initial funds UC-2 sent as the funds were broken down into smaller amounts and sent to bitcoin addresses identified as belonging to an online digital currency exchanger.”
Crees’ alleged admission to the undercover agent about money laundering wasn’t his only alleged admission to that agent or to others. Here is an overview of the 7 victim entities and incidents:
Victim-1:
On June 3, 2020, DR32 posted on a forum that he had hacked a software company in California and was selling root access to their network and exfiltrated source code for $50,000 in BTC or XMR. HSI’s undercover agent negotiated the purchase of the source code and then the access.
NOTE: In all cases where an undercover agent bought access or data from DR32, an HSI forensic analyst confirmed that the access or exploit worked, etc. The affidavit in support of the government’s case contains many more details about each incident than are being included here at this time.
Victim-2:
Also in June 2020, and using his [email protected] Jabber account, DR32 contacted the undercover agent and told him that he had access to a social media company headquartered in California and would sell access for $30,000. DR32 allegedly told the undercover agent that the buyer would have to use DR32’s shells to gain access, but then would have access to 20,000 computers on the network because they all used the same root password. DR32 eventually accepted an offer of $15,000.
On July 17, HSI notified Victim-2 of the breach. On July 28, Victim-2 notified HSI that they had discovered malicious code on their servers and evidence of an extensive hack and data exfiltration. The webshell they found on their server was identical to the script found on Victim-1’s server.
Victim-3:
On July 19, 2020, DR32 reached out to the undercover agent again, and explained exactly how he hacked and exploited Amazon Web Services keys and credentials. DR32 told the agent that it was how he had hacked [a list of entities that DR32 named to the agent but not listed in the affidavit], including a payment platform in Massachusetts. The undercover agent then made arrangements to purchase data from, and access to the payment platform. HSI was able to determine that DR32 had gained unauthorized access to an employee’s credentials that enabled him to steal bulk data with databases, other credentials network topography, and more.
Victim-4:
In August 2020, DR32 informed the undercover agent that he had “access to an underwater sea cable that connects 13 countries. Which is worth at minimum 300k. which I was close to selling for 500k. but china pulled out.”
DR32 later specified that the hack was of an international submarine telecommunications network (”Victim-4″), and he provided the type of computer system he had hacked, suggesting that the undercover agent research the system.
DR32 subsequently allegedly stated “this is an apt level job” and “its [a U.S. intelligence agency]’s wet dream.”
According the government filing, Victim-4 is a 15,000-kilometer submarine communication cable system that provides backbone internet connection to 13 countries in Europe, North Africa, the Middle East, and India.
DR32 offered to sell “access to the original controller,” but told the agent that they buyer would need a “team of engineers to… pivot… to access the rest.” He would be providing:
“how to break in, creds, hwo [sic] the networks operate, and enough to begin an operation that will wiretap 11 countries and give [the buyer] the ability to have a parital [sic] God’s Eye view of the internet which would deanonymize anyone and everyone, welcome to the private NSA. and also smtp and other shit is plaintext so the amount of fucking creds you would get would be moist.”
The agent agreed to a price of $200,000, with 50% to be in an escrow account for the buyer.
There are additional details in the court filing about what DR32 said to the agent and provided.
Victim-5:
Victim-5 is described as a well-known university in Massachusetts. DR32 allegedly used SSH to access its server.
Victim-6:
In March 2021, DR32 notified the agent that he had hacked the “enterprise ticketing system” for a networking hardware company located in California and had stolen data. The government’s filing indicates that DR32 allegedly provided the undercover agent with a service ticket from Victim-6’s system, “which revealed detailed information about a device owned by a client of Victim-6.”
DR32 also provided the undercover agent with a download link for a file called “domains” and claimed the domains in the file were the “domains that use [the Victim-6 ticketing system].” DR32 allegedly claimed he had “200k records of this, plus i can write to mongo and elastic, and file, and i can modify anything, and its enough to call any customer nsa dhs google btc exchanges etc and claim u are from cisco.” DR32 was asking $500,000 for access, exfiltrated information, notes, and additional exploits.
After examining the domains file and seeing that it included top-level military, gov, technology, defense, finance, and healthcare domains, HSI decided not to buy the hack and just notified Victim-6. Victim-6 was subsequently able to identify the vulnerable server and secure it.
Victim-7:
In November 2020, DR32 notified the undercover agent that he had hacked a cybersecurity firm in California. The asking price was for the exploit was $50,000, but when it hadn’t purchased by months later, DR32 reportedly lost access and wound up trying to sell exfiltrated data, source code and notes for $2,000. As part of the interactions, it appears that DR32 gave the agent a login to DR32’s own server where he stored files on Victim-7.
Ransomware Group:
Although the government does not list this as a “victim-8,” it appears that DR32 managed to hack a ransomware group’s server. In September 2020, he told the undercover agent:
“Ive got all their notes. Ive got 500k cvvs [credit card records]. Ive got so much crap
man. And l’ve rootkitted it.”
During this same conversation, DR32 allegedly asked the undercover agent: “care to value them [CVVs] and help me sell em?” DR32 provided the agent with links to data. Inspection of the data set led the government to believe that the dataset had been obtained by the ransomware group through a compromise of an online retailer of women’s clothing.
The government contacted Colorado residents whose credit card data were found in the data set. They are listed by their initials in the indictment. The incidents listed in the government filing are just a drop in the bucket of what Crees has allegedly done, but more on that another time.
Order Granted
On August 26, Magistrate Stratton-Smith in the Adelaide Magistrates Court granted the extradition order.
DataBreaches does not know whether there is any appeal since pending or whether Crees is still in Australia or has already been extradited here. An unconfirmed rumor shared with DataBreaches is that Crees was to be held at ADX Florence in Colorado. ADX Florence is a super-max (super maximum security) prison, but it does have six different levels there. Attempts to locate Crees through the federal inmate locator website returned no results for a search of his name.
As noted earlier, the court filings in the case appear to be non-public at this time. The case is United States of America v. David Kee Crees, 21-cr-00402-DDD. When contacted about the extradition and case, the U.S. Department of Justice declined to comment. DataBreaches continues to attempt to get more information about the case and its status.
Update: The Australian court has informed DataBreaches that Crees is in custody awaiting extradition. There are no further court hearings on this matter.
Accidental duplication of some material in this post removed post-publication. The date of indictment was also previously mis-stated and has been corrected to December 7, 2021.