Hackers who claimed to have stolen all of a Canadian home healthcare agency’s patient and employee data have issued a deadline and new threat to their victim: either pay us or we will start contacting your patients and giving data to the Ontario privacy commissioner’s office. And to prove their claim that they have sensitive patient data, they have provided DataBreaches.net with more than 20 GB of patient records.
The hack of CarePartners was first disclosed by the agency in June, 2018. In July, after receiving some proof of claim from the hackers, CBC reported that the patient and employee records were being held for ransom and that there appeared to be more than 80,000 patients’ records. At that time, CarePartners did not confirm that a large number of patients and employees had had their data stolen. CBC reported:
The company says its forensic investigation has so far identified 627 patient files and 886 employee records that were accessed. But the sample provided to CBC News appears to contain names and contact information for more than 80,000 patients alone.
But CarePartners did not pay the hackers anything, and that’s where things seemed to remain in terms of statements from the hackers, at least until February, 2019, when the hackers, identifying themselves as “Team_Orangeworm,” contacted DataBreaches.net with a link to a paste. That paste provided links to two data archives. One contained employee and corporate data (described in more detail in this post). The second archive allegedly contained encrypted patient data (as reported in this post). The hackers did not provide this site with any of the actual patient data at that time, but recently agreed to provide this site with access to the compressed 7 GB archive of alleged patient data.
The sample contains various kinds of patient files, including tens of thousands of detailed home visit records in folders labeled with team numbers. Those records include the patient’s name, the date of the service, the patient’s diagnoses, and other notes about the visit or needed follow-up. Each multi-page record of a visit or contact also included the names and phone numbers of the patient’s relatives who were caring for them or who should be contacted, as well as the physician contact information for the patient.
But although a single team folder might have more than 50,000 home visit records with patient information, the number of unique patients represented by those files appeared to be considerably less. An analysis of one of the folders, for example, resulted in 820 – 930 unique patients out of approximately 50,000 detailed records. For the entire sample, then, DataBreaches.net estimates that there was likely somewhat more than 5,000 unique patients’ detailed records in the team folders. DataBreaches.net does not know how many other team folders there are that were not included in the sample, so that figure is likely only a portion of one kind of files, and theere other kinds of files as well.
As one example of what else the hackers acquired, the following figure shows the fields in some of the patient databases or tables this site was given access to. Not all the fields were actually populated, but from what I did see, there was a lot of patient information that was not just accessed, but acquired, by the hackers. Some of these databases had a few thousand entries or rows for different patients; others had more than 20,000.
RECNUM,CLIENT_NUMBER,CLIENT_SURNAME,CLIENT_GIVEN,CLIENT_INITIAL,INTAKE_WORKER,INTAKE_DATE,SALUTATION,
DATE_OF_BIRTH,MARITAL_STATUS,SEX,ADDRESS_LINE1,ADDRESS_LINE2,CITY,PROVINCE,PHONE_AREA_CODE,PHONE_EXCHANGE,
PHONE_NUMBER,POSTAL_CODE,LAST_UPDATE,DATE_ADDED,HOUSEHOLD_SIZE,DIRECT_LINE1,DIRECT_LINE2,DIRECT_LINE3,PETS,
INTAKE_TYPE,MUNICIPALITY,OHIP_NUMBER,HIGH_RISK,HEALTH_NUMBER,AREA,SUB_AREA,CAR_REQD,SEE_ALSO,FILE_STARTED_ON,
FILE_STARTED_BY,FILE_DECISION,FILE_DEC_DATE,FILE_DEC_REASON,DIET_NUMBER,DEL_COMMENTS1,DEL_COMMENTS2,ALPHA_KEY,
CALL_DISPLAY_YN,UNLISTED_YN,RISK_NUMBER,FUNDING_INFO,VERSION_NUMBER,SUPERVISOR,CURRENT_CLASS,ADD_DATE,ADD_TIME,
ADD_USER,LAST_EDIT_DATE,LAST_EDIT_TIME,LAST_EDIT_USER,SIGN_TSHEET,PATIENT_ID,PRIMARY_DIAG,SECONDARY_DIAG,
ENTRANCE_CODE,USER_SORT1,USER_SORT2,C5TRNZON_ZONE,USER_SORT3,IVR_FLAGS,OVERALL_STATUS,DEPT_ACTIVE,DEPT_HOLD,
DEPT_WAIT,DEPT_TERM,FILE_STATUS,CLOSE_DATE,CLOSE_TIME,CLOSE_USER,REOPEN_DATE,REOPEN_TIME,REOPEN_USER,FUTURE_USE1,
FUTURE_USE2,FUTURE_USE3,CP_AREA_CODE,CP_EXCHANGE,CP_NUMBER,UNIT_NUMBER,ORIGINAL_CITY,BIRTH_PLACE,LATITUDE,
LONGITUDE,SIN,PHONE_EXT,DEFAULT_ROUTE,DEFAULT_POS,EXPORT_TO_TRACT,BP_AREA_CODE,BP_EXCHANGE,BP_NUMBER,BP_EXTENSION,
EMAIL_ADDRESS,FP_AREA_CODE,FP_EXCHANGE,FP_NUMBER,L_WORKER_NUMBER,DOB_EST_OR_ACT,HP_CALL_SAFETY,HP_MSG_SAFETY,
HP_NOTES,CP_CALL_SAFETY,CP_MSG_SAFETY,CP_NOTES,BP_CALL_SAFETY,BP_MSG_SAFETY,BP_NOTES,FP_CALL_SAFETY,FP_MSG_SAFETY,
FP_NOTES,CP_UNLISTED_YN,CP_CDISP_YN,BP_UNLISTED_YN,BP_CDISP_YN,FP_UNLISTED_YN,FP_CDISP_YN,ENTRY_CODE,REBOOK_WORKER,
UOM_HEIGHT,HEIGHT_KEY,UOM_WEIGHT,WEIGHT_KEY,WEIGHT_UPDATED,C7LHIN_ID,DIRECT_LINE4,ADDRESS_911,EXPORT_TO_NOVUS,
DECEASED_DATE,DECEASED_USER,DECEASED_NOTES,SITE_PREFIX,DEL_COMMENTS3,CCACCLIENTID,EXPORT_TO_MS,FACILITYORHOME,
ADD_SOURCE,OL_ADD_DATE,OL_ADD_TIME,OL_ADD_USER,OL_EMAIL_DATE,OL_EMAIL_TIME,OL_IMPORT_DATE,OL_IMPORT_TIME,
OL_PURGE_DATE,OL_PURGE_TIME,SEND_TO_MAIN,SEND_TO_OFFLINE,OL_RECORDS_ADDED,ORGANIZATION,FILEAS,EMAIL_ADDRESS2,
ALIAS_GIVEN,NICKNAME,PREFNAME,TEAM,SUB_TEAM,TOTAL_DONATION_AMOUNT,DONATION_COUNT,FIRST_DONATION_DATE,FIRST_DONATION
_AMOUNT,LAST_DONATION_DATE,LAST_DONATION_AMOUNT,LARGEST_DONATION_DATE,LARGEST_DONATION_AMOUNT,LAST_NAME_AT_BIRTH,
USE_CBI,STATUS_SUMMARY,FORMATTED_ADDRESS_LINE1,NO_HCNUM_REASON,L_DONOR_ID_NUMBER,V6CON_ID,BRN_LIST,
CCACCLIENTID_LIST,vwCon_conID,C9PERSON_ID,vwBiz_code,vwBizOff_code,LAST_MAPLE,SUPERVISOR_SUMMARY,
LENGTH_OF_SERVICE_DAYS,LAST_SERVICE_DATE,HCN_EXPIRY_DATE
Other files contained the patients’ name and notes in plain text about the patient or their care, such as instructions to only do home visits at a certain time, what the patient prefers to be called, or to call the patient’s named daughter or son (with their phone number) for any issues. Some entries noted whether the patient had any pets, if the patient was “high-risk,” and as an additional safety concern, the numbers of any lock boxes. The following are redacted and clipped by DataBreaches.net from files provided to this site by the hackers.

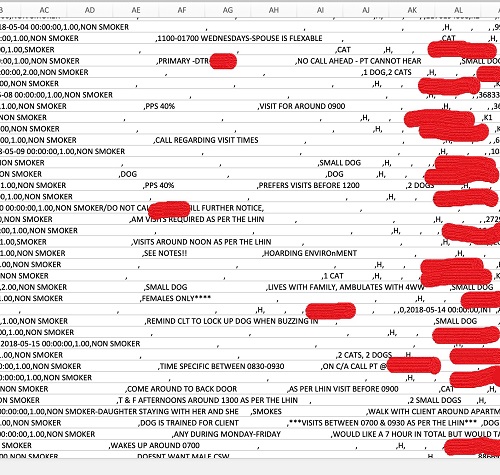
Yet other files contained personal information, but not necessarily sensitive medical information.
But perhaps some of the most sensitive files were the ones relating to palliative care of cancer patients whose unencrypted records appeared with notations such “Expected to die at home.” Knowing that someone at an address is dying of cancer opens up all kinds of nefarious opportunities for criminals.
Other sensitive information, apart from the kinds of diagnoses you might expect for this type of service, included a few patients with psychiatric diagnoses.
So “Team_Orangeworm,” as they call themselves, had not given up on trying to get paid by CarePartners, it seems, and may have been hoping that more media coverage on the hack by this site might pressure CarePartners into paying them. But while they game the media, or try to, there’s also the issue of whether patients really do need to be notified that their information is in the hackers’ hands. CarePartners notified those whom they knew had their data acquired, but what about the tens of thousands of others who also had their data acquired?
DataBreaches.net sent CarePartners a screenshot of the directory of the contents of the sample showing the names of the folders and a few of the files.DataBreaches.net did not send CarePartners individual filenames if the filenames had embedded patient names – and filenames in the team folders all used patients’ last names as part of the filenames. Nor did DataBreaches.net send CarePartners the contents of any spreadsheets or tables that would reveal any patient names or details. DataBreaches.net requested a statement from CarePartners, but has not yet received one. From my conversation with their spokesperson, however, it didn’t sound like they would be giving in to the hackers’ demands, but they haven’t actually put that in writing to this site.
For its part, when asked for a comment about the hack itself, Team_Orangeworm was somewhat terse:
CarePartners security was nonexistent. Nothing was encrypted.
[…]
we stole hundreds of gigabytes of data from their servers with no problems.
that should tell you everything you need to know.
Well, not really, but it will have to do for now, I guess. And they did tell this site that if they didn’t hear back from CarePartners within seven days, they would start emailing the patients to tell them where they could find their information. I hadn’t seen any patient email addresses in the databases I reviewed, so I’m not sure if this is an empty threat on the hackers’ part or not, but the hackers have repeatedly claimed to have other files that they have not yet publicly dumped. So far, we have seen less than 10 GB of the hundreds of gigabytes they claim to have acquired.
In addition to threatening to contact the patients directly, the hackers are also threatening to send a copy of all the data to the province’s privacy commissioner to show the regulator how much data they were able to acquire.
“Team_Orangeworm” by Any Other Name
Based on a number of similarities, I’ve previously suggested that “Team_Orangeworm” is the same group who has called themselves “Anonymous Threat Agent,” “Team_Tesla_,” and “Angels_of_Truth.” In other words, I’m pretty confident that “Team__Orangeworm” is the same group that FireEye has called “FIN10.”You can find FireEye’s 2017 report on FIN10 here.
Are the Data in the Wild?
Of note, DataBreaches.net has been unable to determine whether any data from this hack have ever been put up for sale on any dark web forum or marketplace. The Waterloo Regional Police politely refused to answer that question and the RCMP did not respond to inquiries.
This post will be updated if more information becomes available.