In August, DataBreaches.net highlighted ransomware threat actors known as Pysa who have been attacking both the medical sector and the education sector — two sectors near and dear to this site’s publisher. Today, we report on two more school districts attacked by Pysa.
Consolidated High School District 230
The Consolidated High School District 230 in Illinois includes Carl Sandburg High School, Amos Alonzo Stagg High School, and Victor J. Andrew High School. DataBreaches.net was unable to find any previous media coverage of any breach involving this district, and we found no notice on their web site or any mention of a breach in their school board minutes for the relevant time period. Inquiries sent to the district’s superintendent and executives have received no reply, and a public access request filed with the Illinois Attorney General’s Office has not yet received a response. As far as we can determine, then, this report may be the first disclosure or mention of this breach. [Update: we subsequently received confirmation from the Illinois Attorney General’s office that they had not received any breach notice from the district as of the date of our inquiry.]
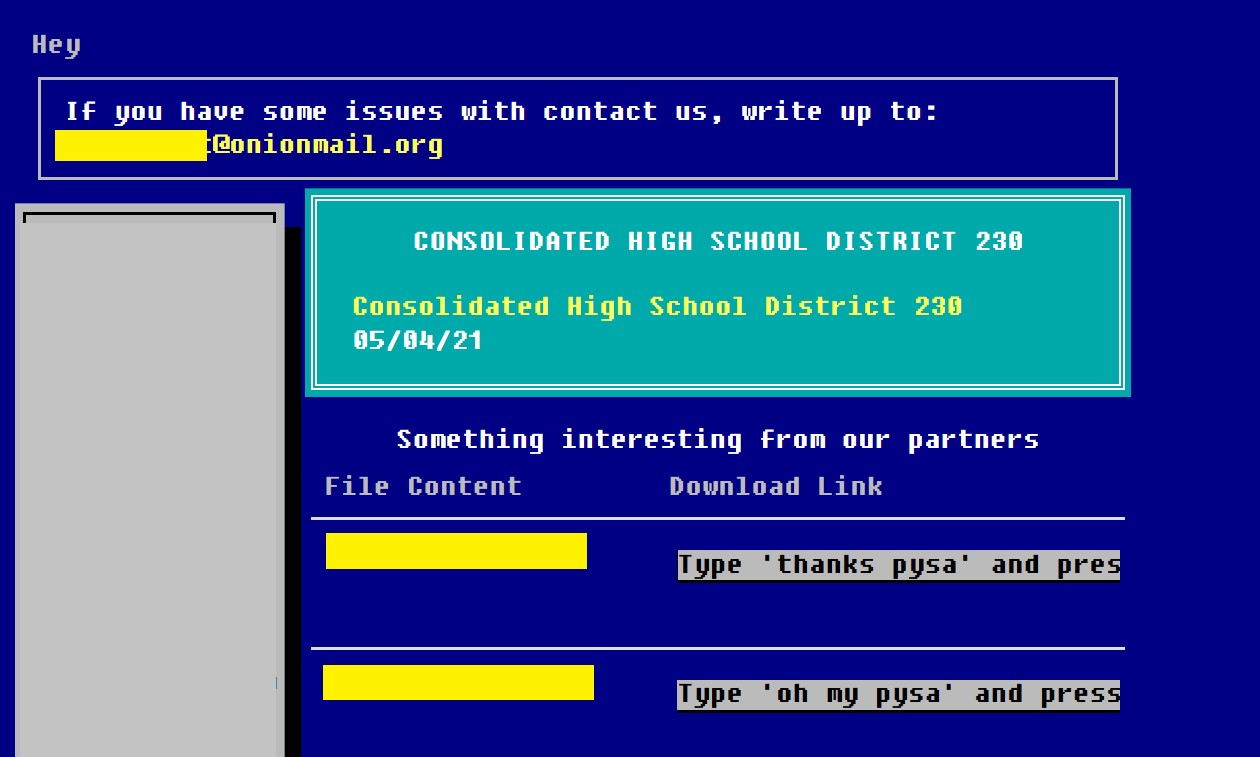
D230 first appeared on Pysa’s leak site this past week, with a date of 05/04/21. It is not clear whether Pysa is claiming that that is the date of the attack or not.
The data dump, in more than 30 parts, included more than 10 GB of files, compressed. Many of the files did not contain personal or sensitive information, but rather, routine district operations related to IT and other topics. Of note, however, we did find personal information on both students and personnel in some files or folders. The following are just some examples:
Student-Related: Some files contained lists of students first and last names with their Medicaid ID numbers. There was more than one year of such lists. The lists do not indicate whether Medicaid was actually billed for any services for the students. Other files for Skyward contained .csv files with students’ ID number, first name and last name, email address, and plaintext passwords. We also noted a few dozen files with named students’ child health examination certificates from the state. We did not spot any databases with education records such as GPAs, courses, testing results, etc., but we did find isolated files with disciplinary or other types of reports.
Personnel-Related: Skyward .csv files contained some personnel information, but thankfully, we did not spot any databases with SSN, although names, positions, email addresses, and date of birth were disclosed. There were also some salary-related files that dealt with contributions to employee benefits, etc. We did not see any payroll databases exposed in this dump. Some isolated files dealing with personnel issues such as harassment complaints were found in the dump.
There were also numerous emails in the dump.
DataBreaches.net is not including a description of other files that might contain information on the physical or cybersecurity configuration of the district, even if the information might be outdated.
Legislation Proposed in Illinois

DataBreaches.net contacted the office of Illinois State Representative Lamont Robinson, Jr., Chairperson of the Cybersecurity, Data Analytics, & IT Committee, to inform him about the incident, as it is the second incident recently reported by this site involving an Illinois school district where we had been unable to find any evidence that the district had ever notified those impacted or disclosed the breach accurately.
Representative Robinson thanked this site for reporting on these breaches and keeping his office informed. He recently proposed a state bill, HB 4152, that would require districts to notify the state board of education as soon as they determine that there has been a security breach of the school district’s computer network or system.
As a result of our discussion, Representative Robinson indicated that he will add a provision to the bill that parents of students and/or employees whose personal information has been compromised in a breach must be notified by the district. That is a significant protection for parents and employees, as many breaches involving school districts compromise parental personal information and personnel information. Simply notifying the state board of education does not help those who need to protect themselves from identity theft or fraudulent use of their information. They need to be notified directly — especially when the data has been dumped publicly for everyone to take and misuse.
Haverhill Public Schools
Unlike D230 where we could find no previous disclosure, Haverhill Public Schools in Massachusetts had disclosed their ransomware attack that forced the cancellation of classes in April. At the time, they did not name the threat actors or what types of data may have been involved, but they did inform the parents and community:
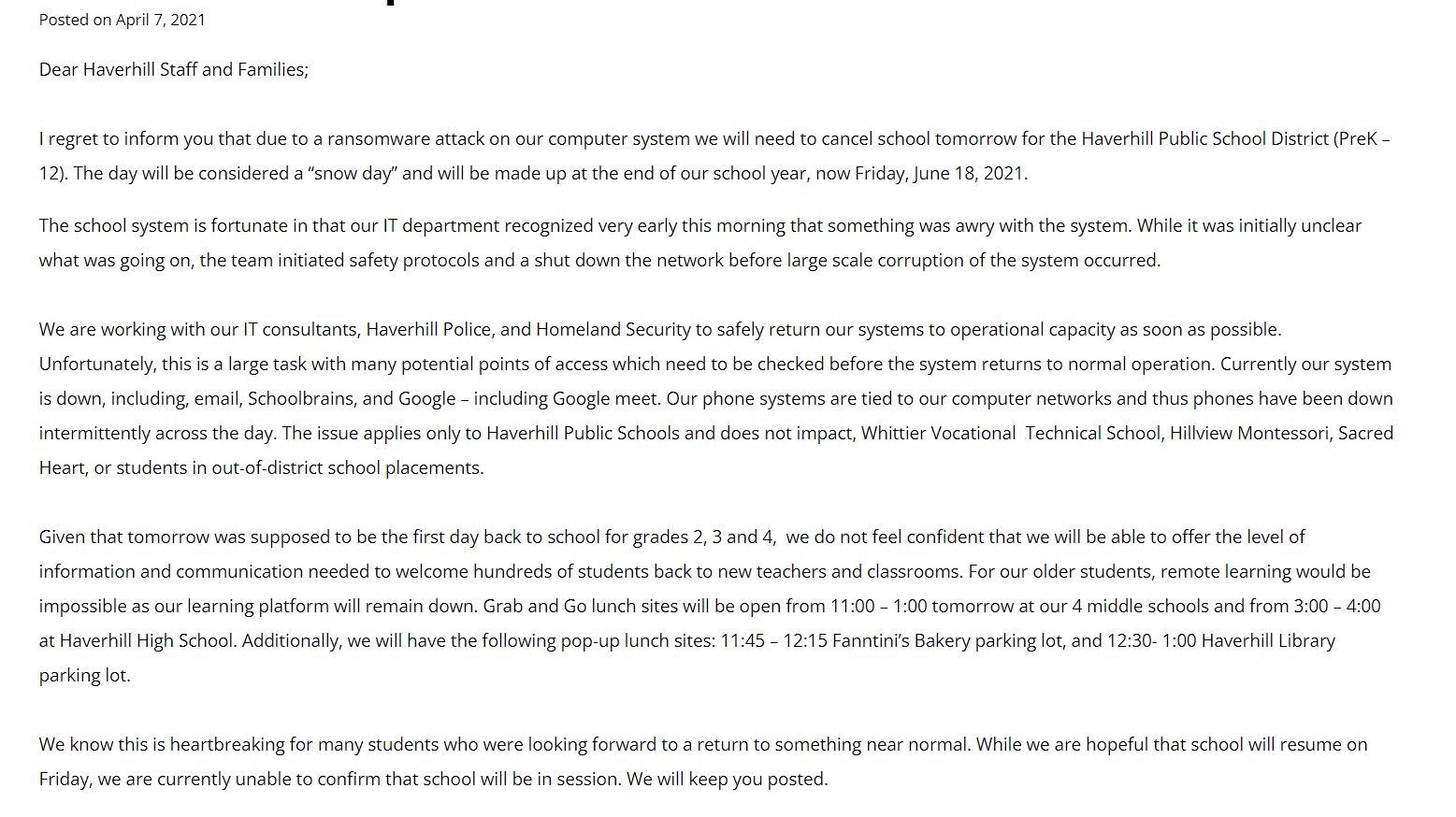
This week, Pysa threat actors added Haverhill to their leak site with a date of 04/07/21. In this case, it would seem that the 04/07 date corresponds to the date of the attack.

While the Haverhill data dump was significantly smaller than the D230 dump, consisting of less than 2.5 GB of files, compressed, the dumped files contained a lot of personal or sensitive information for both students and personnel. As examples:
Student-Related: In one folder, there were dozens of files with personal and education-related information on special education students, such as their required progress reports in meeting the goals set for their Individualized Education Program (IEP). Such reports are required to be kept confidential under the federal Individuals with Disabilities Education Act (IDEA). One such file, clearly labeled “Confidential” identified a named teenager whose medical history was significant for anxiety and depression. Such records, supposedly protected under FERPA as part of a student’s education planning and records, could be upsetting to a student or family if they were widely shared. And yet other folders contained approximately five dozen student applications to register in the district. These applications contained not only information on the students, but on their parents and families, including work information such as phone and email contacts, birth certificate records on the student, driver’s license of the family member, etc.
Personnel-Related: In some folders, there were dozens of contract-related forms for named contractors with their name, address, contract amount, and SSN or TIN. What makes these files somewhat more frustrating is that some of them are quite old, but yet the individual’s name and SSN would still be exploitable by ne’er-do-wells. Other files included completed tax files with personal info, including SSN.
The preceding descriptions are not a complete listing of everything that was in the data dump, but should give readers a sense of how much personal information is now in the wild. Did Haverhill know all these files were exfiltrated? Did they notify affected current and former students and current and former personnel or are they first discovering the scope of the exfiltration now? DataBreaches.net sent email inquiries to the district but received no reply by the time of this publication.
About Pysa
Pysa threat actors use mespinoza ransomware to encrypt their victims’ files. They generally exfiltrate the victims’ data and use a “double extortion” model whereby they try to extort a fee for providing a decryption key to the locked files, and if the victim refuses to pay because they can restore from backup, Pysa can still try to extort ransom by threatening to dump or sell the victim’s data. On their leak site, they refer to their victims as their “partners.” Pysa ( which stands for “Protect Your System Amigo” can be used on both Windows and Linux operating systems.
Pysa is considered a top-tier or second-tier ransomware group that mainly attacks the education, healthcare, and local government sectors. They have been active since the end of 2019.

Other attacks on the k-12 education sector by Pysa previously reported on DataBreaches.net include:
- Affton School District (Missouri)
- Gering Public Schools (Nebraska)
- Zionsville Community Schools (Indiana)
- Palos Community Consolidated School District 118 (update) (Illinois)
- Brookfield Public Schools (Connecticut)
- Winters Independent School (Texas)
- Logansport Community School Corporation (update) (Indiana)
- Sheldon ISD (update) (Texas)
- Buffalo Public Schools (New York)
In March, 2021, the FBI issued a Flash Alert about Pysa’s attacks on the education sector. We encourage school districts to read it carefully and take preventive measures suggested in the alert. Pysa often gains access by using compromised Remote Desktop Protocol (RDP) credentials that they find or purchase. They also use phishing to gain access.
Research and reporting by Chum1ng0 and Dissent.
Have tips about attacks on the education sector? Contact us on Twitter @chum1ng0 or @pogowasright and we’ll tell you how to reach us securely.