School districts continue to be low-hanging fruit for threat actors. While Grief threat actors hacked and then dumped data from Clover Park School District in Washington, Booneville School District in Mississippi, and Lancaster ISD in Texas, Vice Society hacked and then dumped data from Whitehouse ISD, also in Texas.
On June 28, DataBreaches.net emailed Whitehouse ISD to ask about Vice’s claimed hack. The threat actors had not uploaded any proof of claims at that point, and Whitehouse did not respond at all to this site’s inquiries. On July 8, however, the district issued a statement on their web site:
Whitehouse ISD recently experienced a disruption to certain computer systems due to a cybersecurity incident. We responded immediately to contain this incident. We are working diligently with third-party forensic specialists to investigate this matter, confirm its impact on our systems, and restore full and secure functionality to our systems as soon as possible.
Whitehouse ISD’s primary concern remains its students and community. Although our investigation is ongoing, unfortunately it appears that limited information relating to certain student and employee records was compromised. To the district’s knowledge, this information might include, but may not be limited to, personally identifiable information such as home addresses, phone numbers, and social security numbers. Because of this, in addition to the technical experts we have partnered with to ensure our system is secure, we are also working with law enforcement and legal counsel to ensure all appropriate parties are notified and appropriate steps are taken to investigate this matter.
We appreciate your patience and understanding and apologize for any inconvenience. As the investigation continues, we ask that you direct all questions to WISD Communications Specialist Nikki Simmons at (903)839-5500 or by email at [email protected]
DataBreaches.net had directed questions to Ms Simmons on June 28 and then again on July 15, but received no answers at all. The remainder of this report, then relies on partial review of more than 18,000 files in the threat actors’ data dump.
Employee Data
The data dump contained personal and personnel information on both current and former employees.
One file alone contained more than 700 records on those who applied for jobs between 2007 and 2009. DataBreaches.net has redacted the fields, but they contained full Social Security numbers with the applicants’ names and addresses.
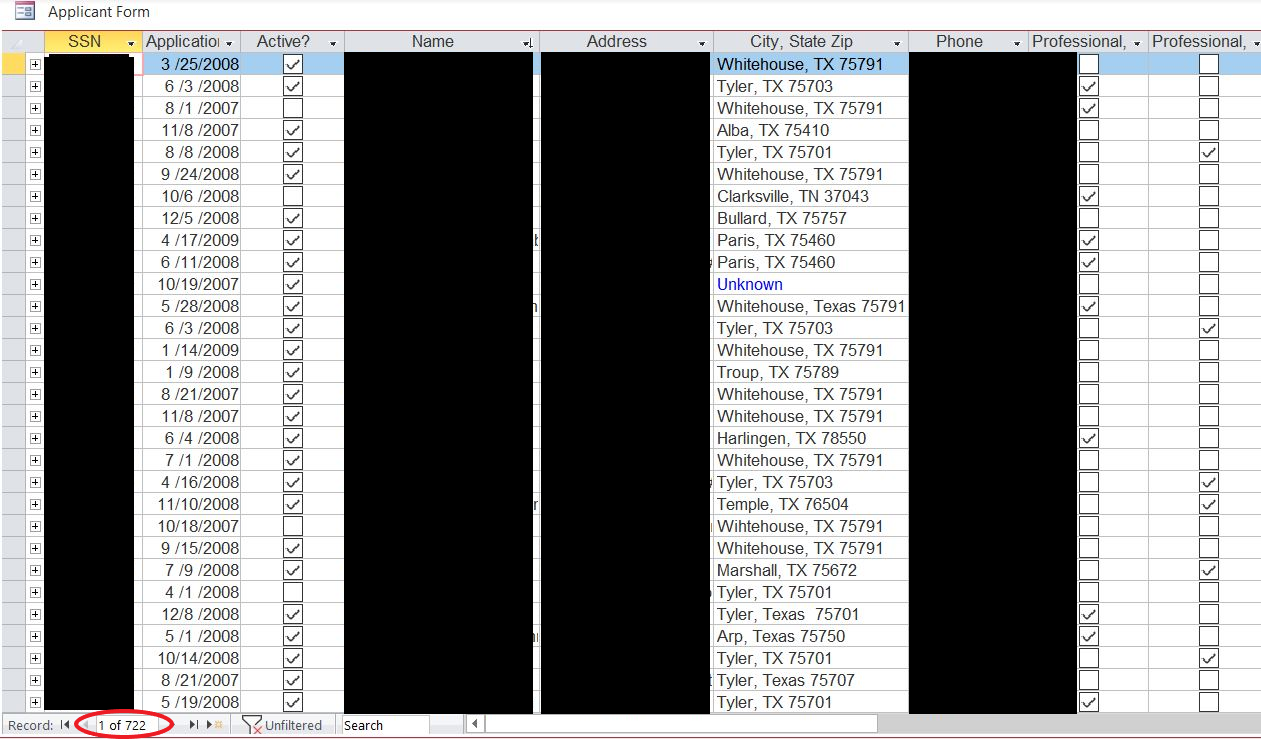
Another file contained more than 770 records on employees in 2015, complete with full SSN (redacted, below):
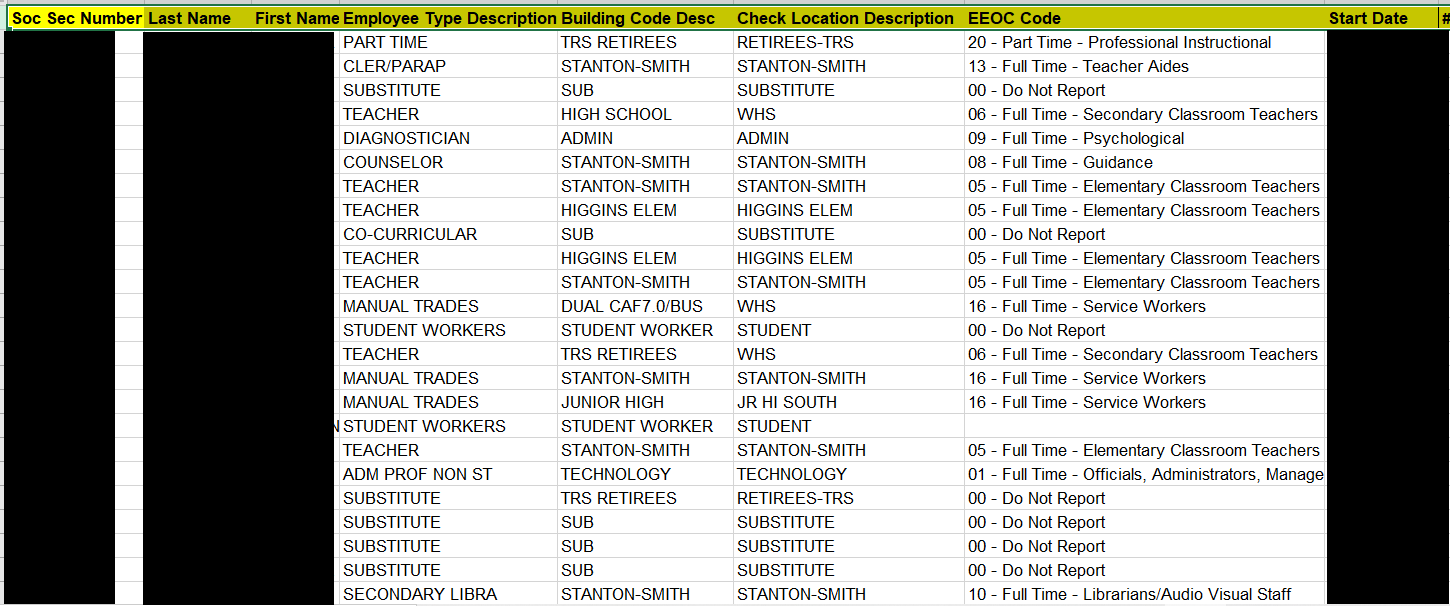
A similar file for 2016 has 892 entries, and a file for 2020 employees has 967 records with names, postal addresses, and SSN. In addition, there are similar databases with information on substitute teachers, with years ranging from 2010-2020. For some years, there were hundreds of substitute teachers entered with their information and SSN.
In addition to thes types of files described above, we also noted some payroll-related information, as well as personnel files such as employee appraisals and corrective action files. The corrective action files were not just for the current year, but went back to 2017.
There were also numerous employee benefits-related files such as Texas retirement system-related records. One file alone, for part of 2016, had 441 pages (one for each employee, it seemed). The following is a redacted entry for just one employee showing all her information and her family’s/dependents’ information:

From our less-than-complete inspection of the data dump, then, it appears that Whitehouse will have a significant number of notifications to make for former and current staff and employees, even allowing for overlap between years. In addition to former and current employees, there is also the dependents for whom notifications will need to be made. One file with a dependent census from 2016 had more than 2000 dependents of employees listed with their names, date of birth, and full SSN.
And then of course, there’s the issue of student data that may have been exfiltrated.
Student Data
As a precursor to this section, we remind readers that there are many elements of student information that are considered publicly available or “directory information” under the federal law protecting the privacy of education records (FERPA). A district may declare what it considers directory information and give parents an opportunity to opt their child out of such disclosures. Directory information often applies to name, address, telephone listing, date and place of birth, participation in officially recognized activities and sports, and dates of attendance. DataBreaches.net could not locate where Whitehouse defines directory information, so the above is just a general guideline.
In terms of files in the data dump, much of the personal information on students that likely is protected by FERPA involved REACH Personal Graduation Planners and Texas Achievement Records. The former includes a student’s name, date of birth, phone number, date of enrollement, and provides specific information on courses taken and grades as this redacted partial form depicts:


In addition to all the graduation planners, there were approximately 150 Academic Achievement Records for named students from the classes of 2020 and 2021, complete with name, address, date of birth, SSN, and education records. Another folder contained more than 130 records on transfer students from the 2019-2020 school year. These records contained more than just class information, as they also contained information on immunization records, the family, and other factors. For each of these students, there was also a second file that contained other information, including SSN. There were also a number of 504 Accommodation Plans that contained sensitive and confidential information about named students who needed accommodations because of disabilities.
Comments
A Vice Society spokesperson informed DataBreaches.net that the school district never responded to any of their messages, which is why they dumped the data publicly. They also informed this site that they dumped all of the data they had exfiltrated — there is nothing else that they acquired, they say.
As we noted with the Clover Park School District breach and the Lancaster ISD breach, Whitehouse ISD maintained a large amount of older personnel-related files on their server, thereby significantly increasing the number of employees and individuals who had their personal and in some cases, sensitive, information stolen and dumped on the dark web.
In September, 2020, Texas announced an initiative with FireEye to provide lower-cost services to k-12 districts to boost cyberdefenses and to assist with any incidents. Did Lancaster ISD ever seek proactive consultation or advice from FireEye or any other experts hat might have resulted in them not keeping so much older data on their server? Did Whitehouse ISD?
Not all aspects of security require costly or sophisticated solutions.
Why, in 2021, after all the warnings to school districts about the risk of cyberattacks, are districts still keeping so much old data on servers connected to the internet? Should cyberinsurance policies have an exclusion that says “We won’t cover your incident response costs for notifications and mitigation services if you leave unencrypted data from years gone by on your server?” Would that help? Should the U.S. Department of Education offer a small grants program to any district that wants to clean up its servers by purging or moving older data? Would that help?
It’s way past time for k-12 districts to stop offering threat actors a feast of poorly secured personal and identity information.
Update of July 19: The Whitehouse ISD spokesperson responded and basically declined to answer this site’s question on advice of counsel because of the ongoing investigation. She did confirm, however, that the district did not pay any ransom.