—– A DataBreaches.net report by Dissent and Chum1ng0 —–
Since 2018, threat actors known as “Pysa” (for “Protect Your System Amigo”) have used mespinoza ransomware to lock up victims’ files after exfiltrating a copy of them. In early 2020, alerts about these “big-game hunters” were published by both the FBI and CNIL . Since then, Pysa has continued to pose a threat to the medical and education sectors. Like a number of other ransomware-as-a-service (RaaS) groups, Pysa maintains a dedicated leak site on the dark web where they list victims who do not pay their ransom demands and then dump their data. They call them “partners.”

In the first part of this 2-part series, we looked into 11 attacks listed on their site involving U.S. entities that would be covered by HIPAA or that collect health or patient information without necessarily being covered by HIPAA. In Part 2 of this series, we will look at attacks on k-12 districts in the U.S.
Overview
Of the 11 entities discussed in this first report, three disclosed the attacks and also reported them to the U.S. Department of Health & Human Services (HHS). In the eight other cases, we were either unable to get confirmation that the incident involved medical or health data (three cases) or we found clear evidence of protected health or medical information but no disclosure by the entity, no notice on any web site, and no report to regulators (five cases).
Three Incidents Reported to HHS
Three of Pysa’s medical sector victims did report the attacks to HHS, to patients who were impacted, and to the public:
- Assured Imaging was added to Pysa’s site on September 13, 2020 after the mobile digital mammography firm did not pay ransom after a May attack. The data dump was uploaded to Mega.nz, who removed it for violation of their terms of service. Assured Imaging reported the breach to HHS as impacting 244,813 patients and posted a notice on their web site in August, 2020. According to the notice, which has since been removed, the types of patient information compromised included full name, address, date of birth, patient ID, facility, treating clinician, medical history, service performed, and assessment of the service performed, including any recommendations on future testing. In May, 2021, Assured Imaging got some good news when a court dismissed a potential class action lawsuit against them, finding that the plaintiffs hadn’t demonstrated any injury in fact or any evidence of a “certainly impending injury.”
- Piedmont Orthopedics / OrthoAtlanta was added to Pysa’s site on August 6, 2020. In September, 2020, OrthoAtlanta notified HHS and the public that 5,600 patients were impacted. They also posted a notice on their web site . Pysa uploaded copies of the exfiltrated data to file-sharing site Mega.nz, who removed it for violation of their terms of service, but OrthoAtlanta’s notice claimed that the patient data included a variation of patient names and addresses, birthdates, phone numbers, medical or health insurance information and social security numbers.
- LifeBridge Community Gastroenterology, LLC dba Woodholme Gastroenterology Associates was added to Pysa’s site with a date of February 1, 2021. In April, they notified HHS that 50,000 patients were impacted by an incident. According to the notice to patients on their web site, the data was exfiltrated on February 25. Inspection of the Pysa’s data dump reveals that the threat actors exfiltrated both employee and patient data. According to Woodholme’s statement, the patient data involved the following data types: patients’ names, addresses, email addresses, dates of birth, patient identification numbers, diagnoses and/or treatment information may have been contained in the files. In limited instances, the files also included patients’ Social Security numbers, driver’s license numbers, and/or health insurance information. But while Woodholme informed patients that data was exfiltrated, they also wrote, “ We have no indication any patient information has been misused.” The notice did not tell those impacted that their protected health information was dumped on the dark web for people to freely download.
 We know there is no legal requirement to tell patients that their data has been dumped on the internet, but we think patients should be told so that they can better gauge their risk and take steps to protect themselves.
We know there is no legal requirement to tell patients that their data has been dumped on the internet, but we think patients should be told so that they can better gauge their risk and take steps to protect themselves.
Three Incidents — Were There Medical Records?
In three cases, we were unable to confirm the breach of any patient protected health information (ePHI) or health data. In two cases, Pysa’s proof did not completely download correctly and the entities never responded to our inquiries:
The Children’s Network is an agency involved in foster placements and we could not determine whether any of the exfiltrated files contained health data on the children although it seemed clear that personal information on parents and children were involved. They did not respond to multiple inquiries sent to them in June and July.
The data for the Drug Alcohol entity included a lot of business files and some files that seemed likely to contain personal information – but was any of it patient information? Email inquiries to both DATCS and the threat actors did not result in responses by publication time.
- Upstate Home Care was also listed as a victim.
In Upstate’s case, we were able to inspect the proof of claim data, but it did not appear to contain any significant patient data and appeared to be corporate and employee data. Upstate was contacted via their web site to inquire whether any patient data was involved, but no reply was received by time of this publication.
UPDATED November 29: Upstate submitted a notification to the Maine Attorney General’s Office on November 24. Their notification indicates that a total of 5,114 people were impacted by the incident. And while they do not segment the number by employees vs. patients, their notification letter states
Some of the information involved and released may have included; full names, date of births, addresses, telephone numbers, email addresses, driver’s license numbers, banking information, social security numbers, treatment information, physician names, patient ID’s, and/or Medicare/Medicaid numbers. The information released about you fell into at least one these categories.
Upstate’s notification does not provide a date for the incident, but Pysa’s leak site indicates that data were allegedly exfiltrated on March 11, 2021. Only a small proof of claim file was provided on the leak site.
Five Incidents That Involved Patient Data But Weren’t Reported?
Disclaimer: We did not find any evidence that any of the five incidents in this section were reported to HHS or to patients, but that does not mean that they were not disclosed somehow or that the five entities have violated HIPAA or any laws. As is too often the case, the entities did not respond to inquiries.
Bolton Street Pediatrics (Marlborough, Massachusetts)
On February 23, 2021, Pysa added a listing for what they called “Marlboro Pediatric Dentistry,” which they linked to https://marlboropediatrics.com/ . Chum1ng0’s attempts to verify the claim quickly led him to realize that although there had been a Marlborough Pediatrics in the past (and there is still a listing under that name on Facebook), the victim in this case is actually Bolton Street Pediatrics, a pediatrics practice located in the Malrborough Medical Center. Bolton Street Pediatrics is not a dental practice.
Inspection of the small data dump (less than 13 MB) provided by Pysa revealed personal and protected health information on what we estimated to be well more than 1,000 patients in 122 files. Two files called “members roster” from 2015 included 986 patients’ name, address, telephone number, date of birth, gender, SSN, and other information. Eighty other files contained batched insurance claims information for 2018, 2019 , and 2020. For each entry, there was a patient’s name, their diagnosis/es, service description, date of service, and health insurer information. There appeared to be hundreds of patients represented in these batched files.
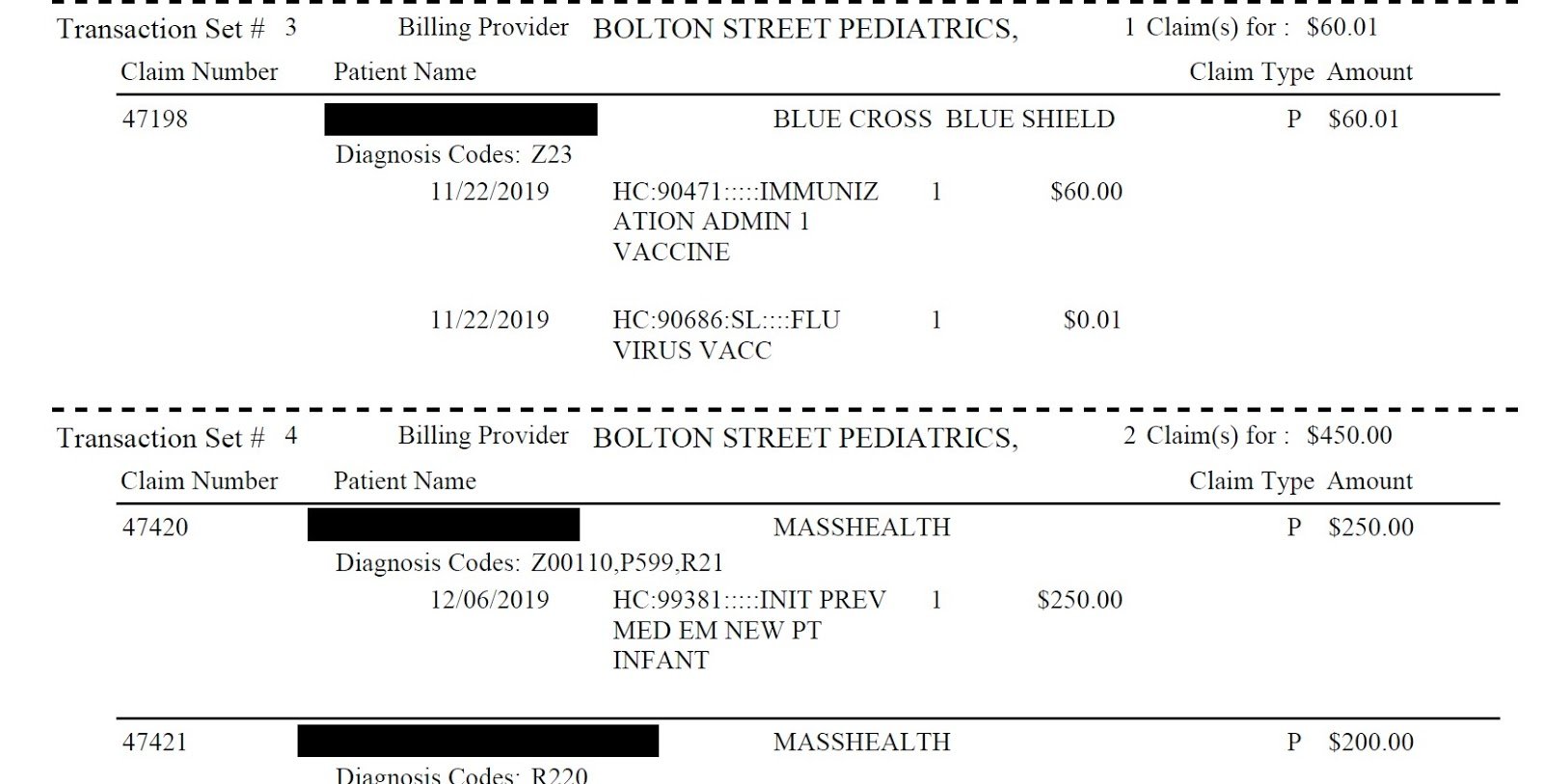
Bolton Street Pediatrics was contacted via email twice to ask them about the apparent breach and whether patients, Massachusetts, and/or HHS had been notified. No replies were received.
Overlake OB/GYN (Bellevue, Washington)
Pysa added Overlake Obstetricians & Gynecologists, P.C. to its leak site with a date of November 29, 2020..The data dump consisted of more than 8,900 files and more than 3.8 GB of data.
There were numerous files with detailed medical history records of pregnancies and visits as well as demographic information on the patients with name, address, date of birth, SSN, and other data types. Unsurprisingly, there were numerous files relating to insurance billing. One file alone contained 297 pages with multiple entries on each page.
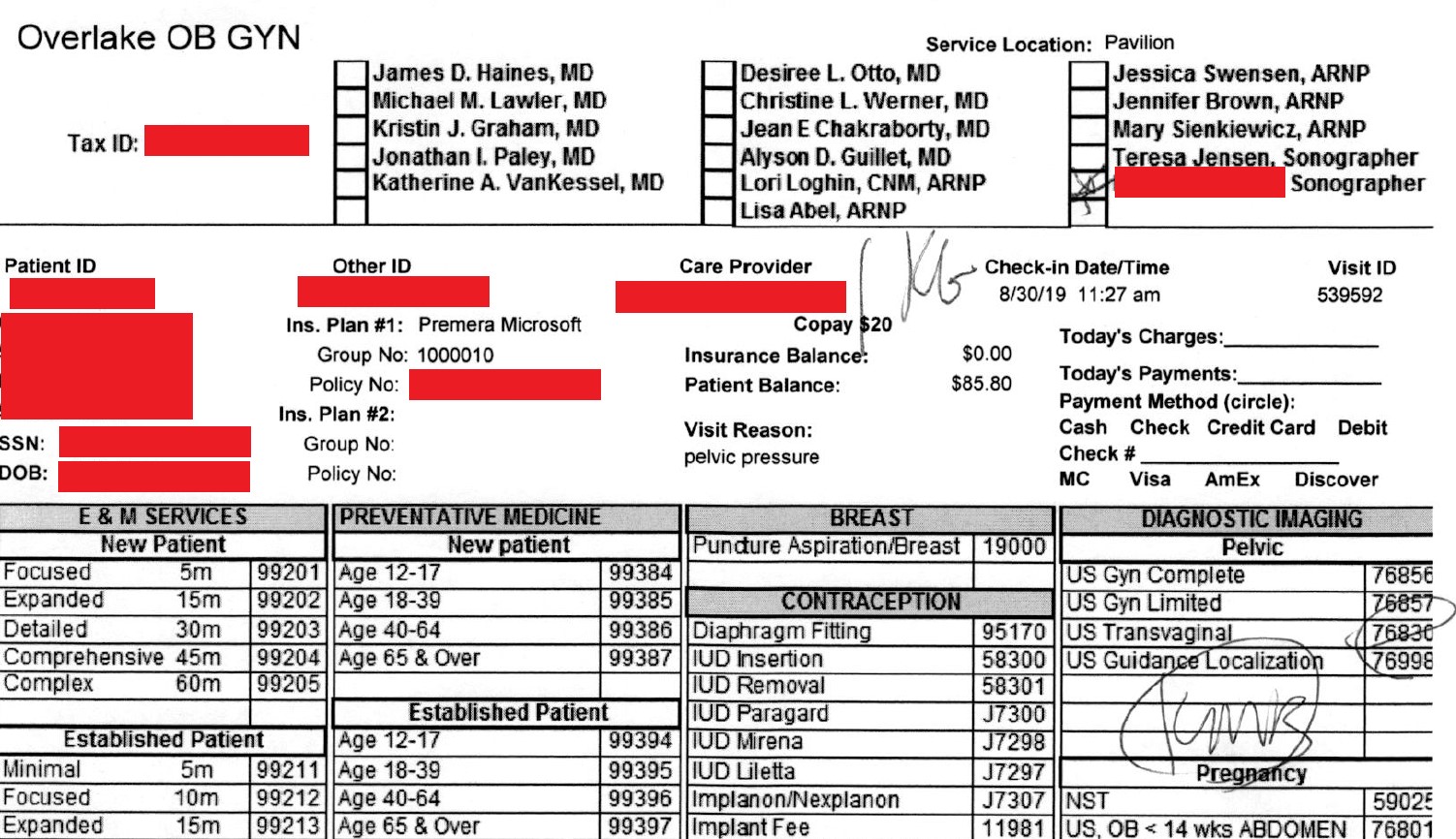
Not all of the files were current, as one file listed every expected birth by month and date with the patient’s name and where they were expected to deliver in 2014.
DataBreaches.net did not attempt to calculate the number of unique patients or employees impacted by the dump, but this certainly appeared to be a reportable breach under HIPAA.
The data dump also contained information on the medical practice’s personnel as well as the group’s financial statements and business operations files.
DataBreaches.net sent Overlake email inquiries on July 27 and 29, but received no replies.
Mid-Florida Pathology (Florida)
Pysa added Mid-Florida Pathology to their leak site with a date of November 22, 2020. DataBreaches.net was unable to download all of the data that was dumped, but was able to download enough of it to confirm that the data did appear linked to Mid-Florida Pathology, as there were folders of critical event reports on Mid-Florida’s letterhead. Those reports contained patients’ name, type of test to be conducted, type of specimen, and notes. Date of birth was also included on many of the reports.

Other folders in the data dump mentioned “Cockerell.” The contents of those folders were reports from Cockerell Dermatopathology sent to Mid-Florida. Yet other folders were labeled “MFD Logs,” where MFD apparently references Mid Florida Dermatology. There were also files with protected health information sent to Mid-Florida Pathology by LabCorp and Quest.
DataBreaches.net sent email inquiries to Mid-Florida Pathology, but received no reply.
St. Margaret’s Hospice (Louisiana)
St. Margaret’s Hospice at St. Luke’s Living Center in New Orleans was added to Pysa’s leak site with a date of November 25, 2020. Most of the parts in the data dump do not contain personal or protected health information on patients but one part of the data dump did. There appeared to be fewer than 500 files with patient information in that archive, but it is not known to us whether Pysa has already dumped everything they exfiltrated or not. This incident might be reportable to HIPAA but for the < 500 reporting rules.
The patient-related files that were dumped were not all of one type. Some contained pharmacy or prescription-related information for patients. Others contained medical records information requested for determination of Medicare coverage for ambulance service. Some contained narratives involving behavioral issues or concerns about patients.

DataBreaches.net sent an email inquiry to the hospice asking if HHS and patients had been notified and for a statement about the incident, but has received no reply.
Bridgeway Inc. (Oklahoma)
Bridgeway is a mental health, alcohol and substance abuse rehabilitation treatment facility that is CARF-accredited. They are headquartered in Ponca City, Oklahoma. Pysa added them to their leak site with a date of March 14, 2021 and a link to a no-longer live url at bridgewayincpc.org.
The data dump is not large but it contains more than 2,500 files, many with personal and sensitive information relating to histories of anxiety, depression, early diagnoses and issues, past and current substance use history, criminal proceedings, and more. Many records concerned offender screening, jail screening, reports of monthly urine testing, biopsychosocial assessment, behavioral history assessment, and other records with personally identifiable information.

Because Bridgeway does not seem to currently have a web site or a posted e-mail address, DataBreaches.net called them and spoke to a woman who identified herself as their director. She confirmed that they had some IT issue in March, but claimed to have never seen any ransom demand, and It was not clear whether she had known or not that their client/patient info had been dumped on the dark web. When asked about that and their incident response, she said she would have their IT director call me back “to start there.” That was yesterday morning. No call has been received as of the time of this publication.
What Next?
As it has done in other cases, DataBreaches.net will continue to monitor these incidents to see if they are publicly disclosed in any way that we can find. If any of these entities replies to inquiries, this post will be updated.
But if there is still no evidence of any disclosure or notification within one month from the publication of this article, DataBreaches.net will likely file watchdog complaints asking HHS to investigate whether the entities had notified them and if not, whether they were required to notify them and to notify patients.
In Part 2 of this report, coming soon, DataBreaches.net will discuss Pysa attacks on the k-12 education subsector in the U.S.
Research and verification attempts by Chum1ng0 and Dissent. Writing by Dissent.