- Copies of fax cover letters from three pharmacies found exposed in an unsecured Amazon s3 bucket
- Faxes reveal patients’ names, addresses, dates of birth and their medications and doctors’ names
- Audio recordings in the second unsecured bucket reveals marketers claiming to represent firms that do not appear to exist as they try to get consumers to agree to let a pharmacy send them “free upgrades” to diabetic supplies
- Buckets appeared to be linked to an entity likely associated with K&C Pharmacy Depot, d/b/a Chesapeake Bay Pharmacy
I’ve covered a lot of leaks over the years, including one affecting almost 1 million consumers that involved telemarketers calling consumers to offer diabetic supplies. The market is huge and growing as our population ages, so it is not surprising that pharmacies would like to be able to entice patients to become their customers.
On June 23, a researcher notified DataBreaches.net that he had found an unsecured Amazon s3 bucket that contained 1.8 million patient-related records that appeared to be from American pharmacies. Because the bucket name did not provide any clue as to bucket ownership, DataBreaches.net started looking into the records to figure out whom to notify. The researcher asked this site not to name him for fear of retaliation in this climate of “shoot the messenger” and false accusations of hacking against researchers.
The files appeared to be text copies of completed fax cover letters records that appeared to be from three different pharmacies. The faxes were to physicians, asking them to approve their patients’ requests for diabetic supplies or other medications.
The three pharmacies whose names and fax numbers that appeared in the records were:
Lynchburg Drug Store in Tennessee, Chesapeake Bay Pharmacy in Maryland, and Milton Medical & Drug in Florida
Chesapeake Bay Pharmacy is the dba of K&C Pharmacy Depot, which appears to be a mail-order pharmacy. I could find no brick-and-mortar store for it. Nor could I find web sites for any of the three, although Lynchburg appears to have a Facebook page.
The fax requests all used the same template. that included a physician’s name, fax number, and NPI number, and the patient’s name, address, date of birth, and the name of the medication(s) the pharmacy was seeking authorization to provide.
Sample fax cover letters found in the file appear below after redaction by DataBreaches.net
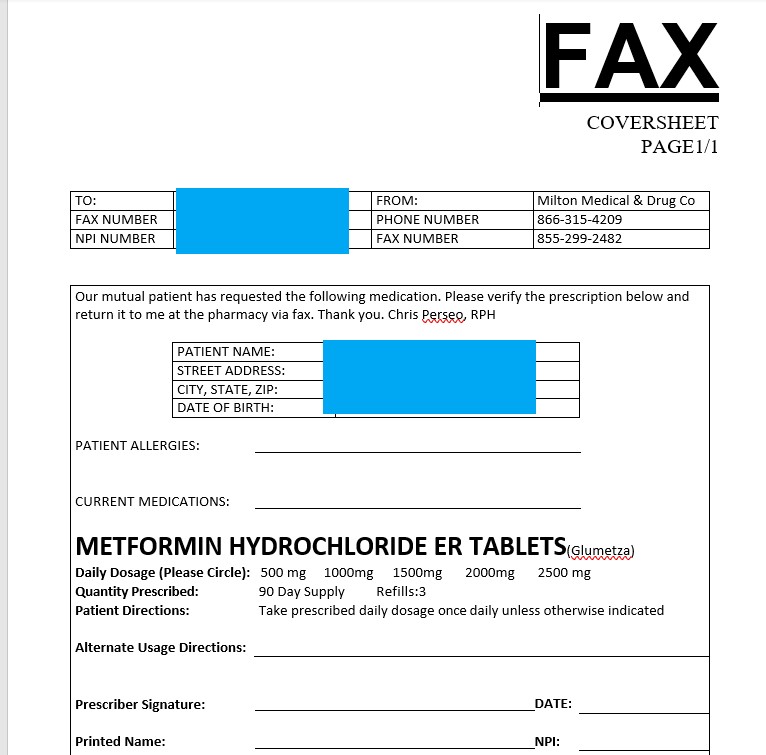

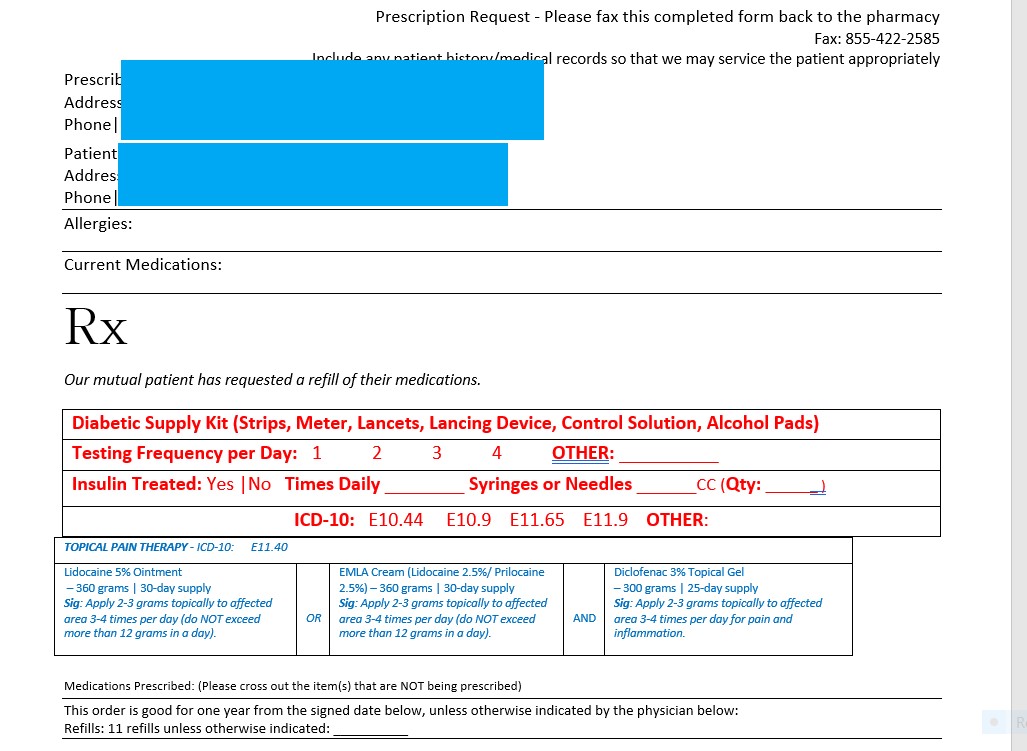
DataBreaches.net could find no evidence of any shared ownership of the three pharmacies, but inspection of the fax cover properties and other files suggested a possible link to a domain called cbprx.net, a domain that is currently listed as a “parked domain” by GoDaddy. Additional research led to an email address: [email protected]. The “shawn” appeared to be Shawn Campbell, whose name appeared as author of the fax templates, and whose name and login credentials appeared elsewhere in an exposed file. A google search for “cbprx.net” also led to a second name: [redacted — see post-publication update], a managing partner at Chesapeake Bay Pharmacy. Somehow, then, two other pharmacies appeared connected to Chesapeake Bay Pharmacy or their associated “cbprx.net” domain and employees.
Oh, Wait… a SECOND Bucket is Leaking, Too?
Before DataBreaches.net could start making phone calls or emailing cbprx.net, however, the researcher notified me that he had found some audio recordings in the bucket and a link to a second unsecured Amazon s3 bucket. This one, he wrote, had more than 1.2 million recordings. The recordings appeared to be telemarketers calling consumers to get them to agree to have a pharmacy send them supplies.
The recordings were made by a variety of individuals. Some claimed to be calling from “HealthConnect” or “Diabetic Solutions.” Some claimed to be calling from “Health Pros” or “Diabetic Stores.” Some said they were calling from “Chesapeake Bay Pharmacy,” and a few said they were calling from “idsinfotech.”
They generally claimed that they were responding to an inquiry or call and wanted to help the person obtain a free upgrade on their diabetic supplies, but they just had to update their information on the person to see if they qualified for the upgrade.
Recordings were stored in folders with various names, including “ldsinfo,” “rcinfotech,” “rlsolutions,” “sai,” “sjc,” and “umg.”
Because many people seemed willing to give out their personal, medical, and insurance info (with the last four digits of their Social Security number) to total strangers who called them, these recordings are concerning. But because it is impossible for me to redact the phone recordings and the filenames may reveal phone numbers and the names of the patients, I will not upload any here as a sample.
Notification Did Not Go Exactly Smoothly
On July 16, I emailed [email protected]. To try to prevent my email from going to spam, I included what appeared to be his username in the subject line. My notification did get his attention, but I didn’t know it at the time, because he did not acknowledge the notification. So I emailed him again on July 17, and this time I added [redacted — see post-publication update] to the email. Neither one replied.
On July 19, I called Milton Medical & Drug to ensure that they knew about the leak. After I explained why I was calling, my call was transferred, and then I was put on hold… and disconnected. I called back and tried yet again. This time, as I was speaking with someone, a third party joined the call and started literally screaming at whoever I was on with…. telling them to hang up on me and that I was the person he had told them about who… something something something… I couldn’t quite make out everything he was yelling about, but it seems that the username I had included in the subject line to get Shawn Campbell’s attention was his password and not his username. Oops.
In any event, rather than thanking me for taking the time and trouble to notify them of their massive leak, whoever had joined the call seemed more concerned that others not speak to me about their massive leaks. After a minute or so of trying to get things on a more professional track, I hung up, unwilling to put up with his rudeness and verbal abuse.
But the phone call convinced me that somehow, Milton Medical and cbprx.net were connected and that someone at cbprx.net had clearly gotten my email and recognized Campbell’s password.
Minutes later, my phone rang. It was someone identifying himself as “Taylor Rockwell.” On inquiry, he said he was Vice-President of Operations. His phone number in Florida showed up on my caller ID as being registered to a Zenrin Belmond. He apologized for the other person’s behavior and he asked me some questions about the leak. I told him what the researcher had found and shared with me. He told me he would call me the following week.
I never heard from him again.
On August 1, I emailed [redacted — see post-publication update] at his cbprx.net email address to ask for his comments about the leak and to ask him some questions about it. He did not reply.
On August 6, I called Lynchburg Drug Store to verify that they even knew about the leak involving their patients’ PHI. The pharmacist knew nothing about any patient data leak, and knew nothing about Milton Medical, but said she thought Chesapeake Bay Pharmacy had closed. She suggested I email the owners of Lynchburg Drug Store and gave me their email address. I emailed them twice that day.
No one from Lynchburg Drug Store replied.
On August 6, I called “Taylor Rockwell” at the number he had presumably called me from. I left a voicemail asking him to call me about the leak we had discussed. He did not return the call. Later that day, I sent him a text message.
No response to that, either.
So Milton Medical, Lynchburg Drug Store, and Chesapeake Bay Pharmacy have all been notified that protected health information of their patients was exposed in an unsecured Amazon s3 bucket, but they haven’t all even acknowledged the notification or indicated what they are doing in response to the incident.
As to the telemarketing firms calling consumers, well, I made no attempt to reach any of those firms, as whoever owns the bucket or hired them should deal with that, and I’m not sure if that’s cbprx.net or Chesapeake Bay Pharmacy or some other party. But there are 1.2 million consumers whose names, telephone numbers, and in most cases, personal and medical/insurance health information were also exposed online for some unknown length of time and were potentially downloaded by others.
The recordings may not be protected health information under HIPAA, but I wonder whether those recordings where the callers claimed to be from Chesapeake Bay Pharmacy might be considered PHI because they were allegedly being made by a covered entity. I’d be interested to know what HHS/OCR thinks about that.
So What’s Next?
We are still within the 60-day window from discovery of a breach to required notification to individuals under HIPAA and HITECH. But that window only applies if these are reportable HIPAA breaches — and I don’t know if the entities will decide that these were not reportable incidents. And I am not sure if this incident has to be reported to individuals and state attorneys general under various state laws. These patients and consumers are located all over the country.
But apart from HIPAA and state breach notification laws that might apply, telemarketers called consumers and often claimed that they were returning calls — when they probably were not. Or they claimed that they are responding to an inquiry — when there probably was no inquiry. I’ve received numerous calls like that myself, and while I have no proof that these callers were actually cold-calling, I strongly suspect that they were simply working off a leads list and there had been no inquiry or call at all.
They also appear to be lying about who employs them and using fraudulent business names to make them sound more legitimate to consumers.
Could the FTC Act have anything to say about the deception as well as the failed data security?
So OCR and FTC: check your inboxes, as I submitted watchdog complaints to both your agencies. I hope you investigate this one.
Update and Correction of September 12, 2020: This site was recently contacted by an individual named in this story. He explained that he was not involved with any of the companies or activities described in this post, having sold his business the previous year. Because the sale included the domains and associated email accounts, he never received any emails that had been addressed to him at the domain email. He states that he never received other communications that had attempted to reach him, either.
Because he has provided this site with documentation confirming his claim that he had sold his involvement well before the activities described in this post occurred, his name has now been removed from the story. DataBreaches.net apologizes for any error.