On February 25, popular hacking-related forum RaidForums.com (RF) appeared to have been seized. It was not the first time it had appeared to have problems, but in the past, the owner, “Omnipotent” had reappeared briefly to restore the site somewhat. Now it did not appear to be working at all and had been replaced by what appeared to be a phishing page.
Omnipotent made no public statements, and moderators “Jaw” and “Moot” posted notices on the forum’s Telegram channel stating that the forum had been seized, and that anyone who had attempted to login to the phishing page should change their passwords and clear their logs. Since then, there really have been no substantive updates and it’s not clear whether Omnipotent has continued to remain in contact with Jaw or if not, why not.
While law enforcement agencies contacted by DataBreaches.net declined to comment or just didn’t answer at all, one of RF’s most active users, “Pompompurin,” (Pom) took steps to try to protect users from accidentally exposing their credentials on the phishing page. He started DDoSing the RF site to save users from themselves if they hadn’t detected the phish, but his attempt failed after CloudFlare started rate-limiting.
Now Pom has opened up his own site to pretty much provide the equivalent of RF. Breached.co, also known as BreachForums, opened this week. Its theme, contents, and rules, are pretty much identical to RF, although not all sections or services are in place just yet.
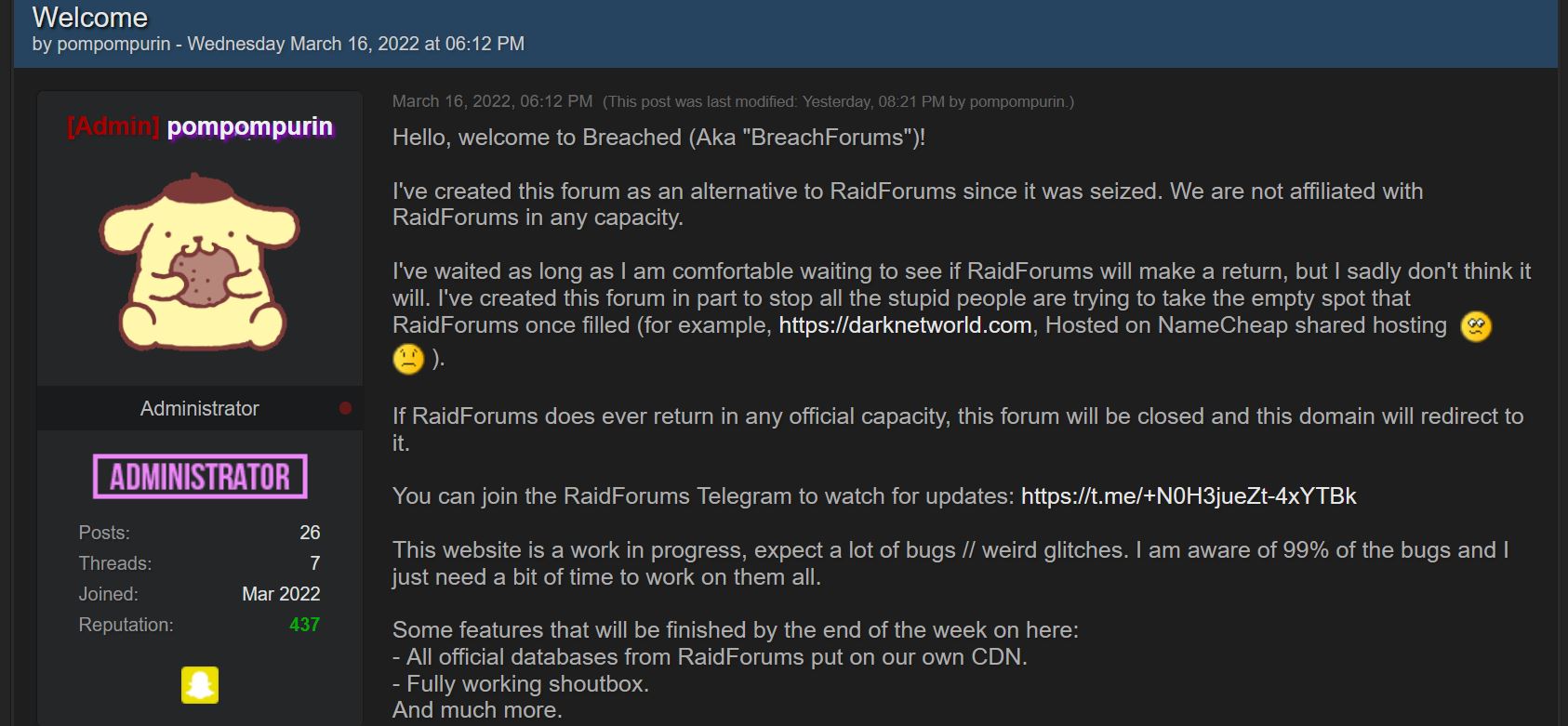
Part of his motivation in creating the forum, he wrote, was to “stop all the stupid people are trying to take the empty spot that RaidForums once filled….”
In an interview with “Alex” of DataKnight blog, Alex cut to the chase, asking Pom how Breached could avoid the same fate as RF.
Alex: So, What is Breached doing to ensure that it doesn’t suffer the same fate as RaidForums? And what kind of security can users expect to receive when using your site
Pom: Passwords are configured to be in argon2id [Password Encryption Algorithm], I am pretty confident that we will be able to last a long time. There will be a person with full access to the servers, backups, and everything needed to relaunch unaffected within hours if I am arrested or if one of the domains//servers are seized..
Alex: I can see that you’ve put a lot of work into this… but don’t you think that there’s a reason that the FBI took down RaidForums? Why would you want to bring it back up knowing that you may face that same fate whatever it [may be]
Pom: [Redacted], it doesn’t really bother me. If I get arrested one day it also wouldn’t surprise me, but as I said I have a trusted person who will have full access to everything needed to relaunch it without me. This person will also never be made known to the public, so it wouldn’t be possible for the police to also target them in the event that they want to get the forum taken down for good.
Pom certainly has good reason to fear arrest given his history of involvement in certain activities such as misusing the FBI domain to blast out spam emails as a hoax and getting involved in the sale of Robin Hood data. Despite what would seem to put a large target on his back, Pom has repeatedly shrugged off any questions about whether he has any fear of arrest, claiming that if it happens, it happens, but that his OPSEC is so good that he is not really concerned.
But in addition to what Pom told Alex in their interview, Pom has actually taken other steps to avoid the same fate as RF. In an exchange with DataBreaches.net, this blogger pursued the question Alex had raised:
DISSENT: If you don’t know for sure why RF got seized (assuming at this point that it was seized), isn’t your forum likely to run into the same problem?
POM: No, I doubt my forum will run into the same problem. From looking at previous seizures that LEA [Law Enforcement Agencies] have done, they almost always seize domains by going straight to the TLD // ccTLD holder. In the case of RaidForums and WeLeakInfo, both domains were likely seized by the Feds going straight to Verisign (current operator of .net and .com). Breached is currently using the .co ccTLD (Colombia) and we have also bought breached.to as a backup (ccTLD for Tonga).
Given that law enforcement is likely in possession of RF user data and private messages, is it smart to encourage Breached users to use their RF usernames and credentials? Wouldn’t they be safer creating new identities even if it costs them their reputation or status? Are they now sitting ducks because law enforcement can still find them online? When asked, POM replied:
As long as they practiced proper OPSEC when using RaidForums (Always on a VPN, not using a personal email, not sending personal things via PM etc) then I personally think it’s fine to use the same alias. As for the passwords, I beleive most people are aware by now that RaidForums has turned into a honeypot. If someone decides to use the same password they entered into the phishing page I can’t really control that
In looking at Breached, this blogger noticed that “Jaw” and “Moot” were not moderators for the new forum. Pom was asked about their role in Breached:
DISSENT: Will Jaw and Moot be involved in this forum? And do you already have people designated/approved as middlemen for sales/escrow?
POM: That would be ultimately up to them. If they wish to be apart of it then I will let them. At this current point in time we don’t have any middlemen services. Still need more time to figure out the specifics.
DISSENT: It sounds like you are not motivated/particularly interested in having them continue as mods or anything. I thought you all got along, but it sounds like maybe not so much…?
POM: No we do, but it’s just I don’t wanna force them to join lol
There’s a difference between not forcing people and not even asking them. Were they even asked? When contacted, Moot informed this site that he had not been involved in setting up Breached and currently had no involvement in it.
I would signup but I don’t use hacking forums, maybe if they added a section for baking recipes.
Well okay, then…
As noted in his site’s welcome message and his statements to both DataKnight and this site, Pom has stated that he will give up Breached if RF comes back. In the meantime, Breached users are currently debating what happened to RF.
Breached currently has the same rules and policies as RF in terms of what can and cannot be posted. And that means that politically motivated postings are not off-limit. Prior to the seizure (assuming for now that it was a seizure), one moderator had posted that anyone posting from a Russian IP address would be banned. That, Pom, says was just a joke. Will anti-Ukrainian posters like “FreeCivilian” begin listing Ukrainian leaks again now that the site is under new ownership? We’ll have to wait and see. There is already one posting claiming to be by Anonymous promoting #OpRedScare.
Breached already has 217 registered members in less than two days.
Wow very insightful thanks