Update: On December 23, DataBreaches.net received a statement from Uncle Maddio’s public relations firm saying this is not their database:
“Thank you for contacting Uncle Maddio’s Pizza. After investigating the information you provided from the third party and reviewing our information security standards and systems, we believe you may have us confused with another company. The information to which you refer does not correspond to the information we keep regarding our customers and employees. We take these claims seriously. We understand the immense importance of protecting information we receive from our employees and customers and have adopted standards and practices to protect that information, including separation of employee data from customer data, outside our payroll providers not storing SS#’s of employees and not storing credit card information. If you have additional information, please let us know.”
DataBreaches.net has forwarded their statement and request for additional information to Chris Vickery, so he can provide them with additional information. Although DataBreaches.net did not publish anything about it, some of the files in the database were from what appeared to be November newsletters and promotions/rewards for Uncle Maddio’s.
At the present time, then, this leak is in dispute. DataBreaches.net will update as more information becomes available.
Original post follows….
 Uncle Maddio’s Pizza Joint describes itself as a fast casual restaurant chain serving pizzas, salads and sandwiches. Headquartered in Atlanta, Georgia, they have dozens of locations, and as of last week, over 164,000 customers who receive their newsletter or offerings.
Uncle Maddio’s Pizza Joint describes itself as a fast casual restaurant chain serving pizzas, salads and sandwiches. Headquartered in Atlanta, Georgia, they have dozens of locations, and as of last week, over 164,000 customers who receive their newsletter or offerings.
Chris Vickery discovered that their database was leaking and reported it to this site.
Screencaps provided to DataBreaches.net revealed that 972 former and current employees had their name, address, phone number, hire and termination date (if no longer employed), pay rate, and Social Security numbers in plain text stored in the database. Not all employees had SSNs in the database, which humorously, has directories called “Kerrigan” and “Sarah.”
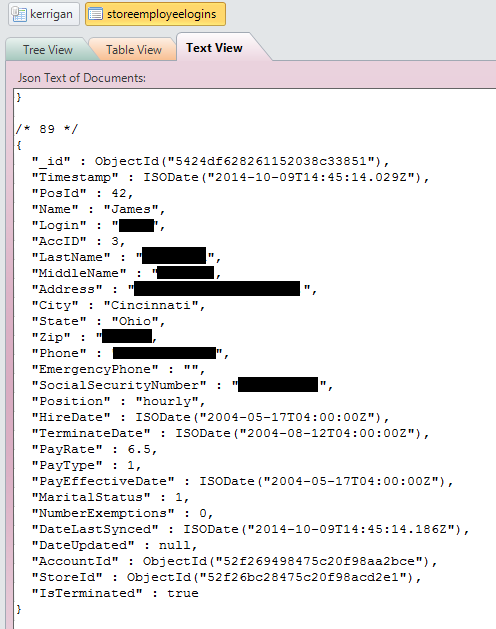
Other screencaps also indicated that Uncle Maddio’s stores data on 164,018 customers. The site has a subscription email newsletter and a rewards program where customers provide their first and last names, email addresses, and their favorite Uncle Maddio’s location. These data also appear to have been stored in plaintext, and one table also included their telephone numbers. Credit card data from customer orders or bills did not appear to be stored in plain text, however.
DataBreaches.net first notified Uncle Maddio’s on December 15 by email, phone, and the site’s feedback form. They received the notification and acknowledged it promptly, asking for additional details which this site provided, but the database remained unsecured, despite reminders from this site days later that the leak put their employees at risk of identity theft. Attempts to get their Twitter’s team attention were unsuccessful, as was an attempt by Chris Vickery to get a response from a firm in the Philippines that might be involved in securing the database. Their web team ignored a request from this site for their corporate headquarter’s phone number, which is not easily located online.
On December 20, DataBreaches.net provided final notice to the site, and indicated that absent a response from them indicating that they were actively addressing the leak, DataBreaches.net would publish this report on December 22. They did not respond to that communication, either. As of the time of this publication, then, one week after initial notification, the database remains unsecured.
The next time you’re thinking of giving your information to your favorite restaurant or store, think about whether you’re okay with the whole world having your information. If you’re not, maybe thinking about not signing up.
And if you’re a past or current employee of Uncle Maddio’s, perhaps you should call your boss and ask them what they’re going to do – immediately – to protect your identity information and Social Security number. You are at risk of identity theft if the data are downloaded by criminals.
This post will be updated if additional information becomes available.