– Personal, public, and some non-public information on 191 million registered voters exposed
– Efforts to identify database’s owner to notify them unsuccessful
– Database still exposed
A misconfigured database leaking the personal information of over 191 million voters was reported to DataBreaches.net by researcher Chris Vickery. This report includes some of the results of an investigation by Vickery, DataBreaches.net, and Steve Ragan of Salted Hash.
UPDATE: As of earlier this evening, the database is no longer publicly available. Earlier today, NationBuilder issued this statement.
UPDATE2: i360 subsequently responded to an inquiry from DataBreaches.net and confirmed that the data were not theirs.
Backgrounder: What Data Are in a Voter’s List?
Voter lists or databases may include a lot of information about you in addition to the information you are required to provide when you first register as a voter. They may contain your first and last name, your home and mailing addresses, your date of birth, gender, and ethnicity, the date you registered to vote, your telephone number, your party affiliation, your e-mail address if you provided one when you registered, your state voter ID, whether you’re a permanent absentee voter, and whether or not you’re on the Do Not Call list.
Lists of voter registration information may be obtained from your state and then combined with other data sources by marketing firms or those serving as consultants to political parties or political campaigns. Who can obtain the state’s voter list, and how it may be used depends on the state’s laws. So databases developed for political campaigns may also include whether or not you voted in the last general and primary elections, whether you appeared to follow a party line vote, and there may be a score predicting whether you’re likely to vote in an upcoming election or for a particular party or candidate. Databases developed for issue-oriented campaigns or non-profits doing fundraising may contain even more personal information such as your religious affiliation, whether you’re likely to be anti-abortion, whether you’re a gun owner, etc.
While the majority of states make their voter registration lists available as a matter of public record and do not restrict use, some states restrict use. For example, South Dakota requires the requestor of voter registration data to sign a statement:
“In accordance with SDCL 12-4-41, I understand that the voter registration data obtained from the statewide voter registration database may not be used or sold for any commercial purpose and may not be placed for unrestricted access on the internet.”
In California, information on voter registration cards is considered confidential, and subject to many restrictions to access and use. One of the restrictions is that the information may not be made available to persons outside the U.S. And in Hawaii, voter registration information may only be used for elections and by the government.
But for the most part, not only can political organizations acquire information about you, they may be able to post it publicly, or even create an app with the information.
Not surprisingly, the more complete the list or database, the more costly it may be. A database with information on all American voters, for example, might go for about $270,000, according to one marketing firm consulted by researcher Chris Vickery.
Voter lists have a number of recognized uses. Even though a percentage of the records are likely to contain inaccuracies, these databases are a goldmine of potential voters for political parties and campaigns, as well as pollsters. The recent political flap when some of Bernie Sanders’ staffers accessed the Clinton campaign’s data shows how highly prized such information is for political purposes. Voter lists or databases also provide a treasure trove of leads for non-profit organizations doing fund-raising, and they are a valuable resource for journalists investigating election issues or candidates, for scholars, and for the government itself.
Researcher Chris Vickery Uncovers a Gold Mine
On December 20, researcher Chris Vickery contacted DataBreaches.net to say he had found a database with 191,337,174 million Americans’ voter information exposed due to a misconfiguration of the database.
He admits he got quite a shock when he found his own information in it, and sent along this screenshot:
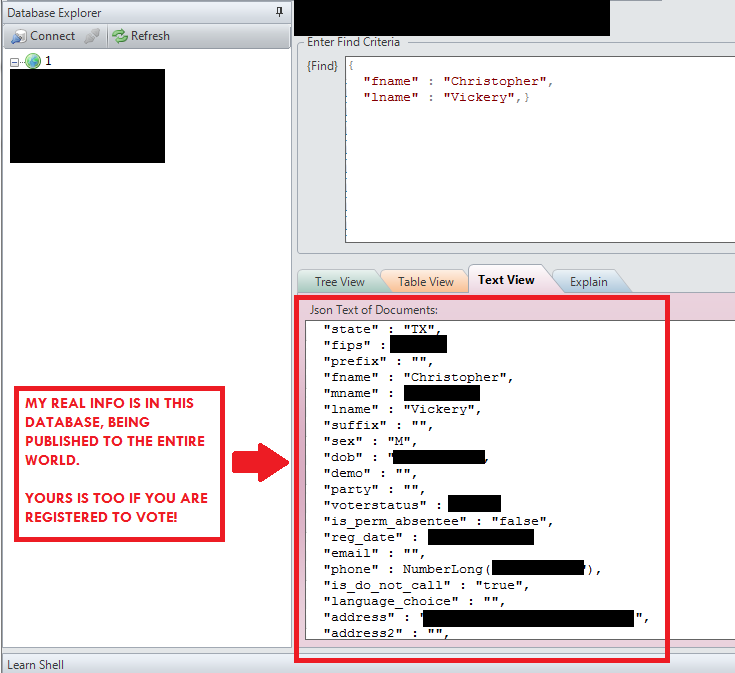
Chris wasn’t the only to get a rude shock. “Sam,” a police officer known to DataBreaches.net who asked that we not use his last name, was also concerned when DataBreaches.net showed him accurate details on himself.* To protect his and his family’s safety, Sam does not have a publicly listed phone number or address. When shown the information on him in the database, Sam’s response was “Oh man. … I deal with criminals every day who know my name. The thought of some vindictive criminal being able to go to this site and get my address makes me uncomfortable. I’m also annoyed that people can get my voting record. Whether I vote Republican or Democratic should be my private business.”
While states may suppress police officers’ voter registration records if they individually request it, it appears that there is no uniform automatic suppression of law enforcement personnel’s records in publicly available voter registration lists.
Thankfully, there are no Social Security numbers, driver’s license numbers, or any financial information in this particular database, but full name, date of birth, and address and phone number with political party and other fields – are problematic enough when it comes to protecting our privacy and security.
To see an almost-complete list of the data fields in this leaky database so you can find out what information about you may now be publicly available, see a redacted entry, here.
Who Dunnit?
Based on preliminary investigation by Vickery and DataBreaches.net of some data field labels that looked like they might be unique or proprietary, DataBreaches.net reached out to Nation Builder, the online service of 3dna, Corp., to inquire if the database was one of their databases or if it might be one of their clients’ databases. But after 24 hours with no response, and although we really wanted to know who had left this database available to the entire world, Vickery and DataBreaches.net agreed to turn to law enforcement who might be able to get the database removed or secured more quickly.
Both the FBI NY field office and IC3 were contacted, as was the California Attorney General’s Office. California was contacted as they are one of the states that restrict what cannot be disclosed. When one of their attorneys asked, “Well how much data are we talking about?” and I read her the list of data fields and told her that we had access to voter records of over 17 million California voters, her response was “Wow,” and she promptly forwarded the matter to the head of their e-crime division. The California Attorney General’s Office has not replied to follow-up e-mail inquiries since then, however, and the FBI would not comment when DataBreaches.net tried to follow up with them to find out what, if anything, they were doing.
When DataBreaches.net eventually reached someone at Nation Builder. Ben Handzo, Product Director, followed up and reported that the IP address was not one of their IP addresses. Nor, he said, was it an IP address for any of their hosted clients. Although we were – and remain – pretty certain that the database involves Nation Builder’s data because of unique data field labels and because the numbers match their database as it was in March, 2014, we had hit a dead end there. Could Nation Builder reach out to all of their customers to ask them to check to see if they were the source of the leak? Yes, but we realize that they’re really under no obligation to do so.
Meanwhile, based on the “User” in the leaky database, DataBreaches.net also reached out to a congressman’s PAC to inquire whether it might be their database. To date, they have not responded, but a staffer for the congressman said it was unlikely to be theirs as they only worked regionally and not nationally.
Enter Steve Ragan of Salted Hash, who offered to put on his deerstalker hat to help investigate after we reached out to him.
Steve began contacting some big political consulting and software firms, as he reports today over on Salted Hash. So far, none of those leads has resulted in identifying the owner of the leaky database.
Potential for Abuse?
More than one week after Vickery first discovered the leak and we began trying to locate the responsible party, the database remains online and exposed – despite countless hours on our part trying to track this leak down.
If you are a registered voter, we cannot offer you reassurance that your details have not been obtained and won’t be misused. We don’t know for how long this database has been left unsecured and how many people may have accessed and downloaded it. At this point, all we’re pretty sure of is that the data in the database include data from Nation Builder. Could it be one of their non-hosted clients leaking the database? Maybe. Could it be that someone hacked one of their clients and stored a copy of the database at this IP address? Maybe. Could it be that an employee of a client decided to make themselves a copy for their own purposes? Maybe. The possibilities are numerous. We really don’t know and DataBreaches.net declines to speculate.
Head on over to Salted Hash to get Steve Ragan’s report and insights.
And then maybe call your Senator and Representative in Congress and tell them that as a constituent, you want them to ensure that there are adequate laws protecting the privacy of our information. It’s too easy to upload a database with all of our contact details, our date of birth, and our political affiliations and voting history to the Internet where anyone can grab it. Tweet them a link to this article with #ProtectMyPrivacy.
Do You Know?
And if anyone has any knowledge of who might be responsible for this database, please contact [email protected] or contact me on Twitter or WICKR (“PogoWasRight”). For encrypted tips by e-mail, my OpenGPG key: 0x0625E4BA.
DataBreaches.net, Chris Vickery, and Steve Ragan will keep investigating this leak and will update our reports as more information becomes available.
—
* N.B.: Sam’s data was only retrieved from the database after Sam was asked for, and gave, his permission to do so.
I’m sure you’re this far already, but my guess is you have an analytics or scratch database of a large national campaign or PAC on the Republican side. I say that because pretty much everyone on the Democratic side with data on that magnitude uses NGPVAN data. My guess is a campaign/PAC data staffer with little security knowledge set it up.
someone should post a link to the db
That’s not going to happen here. Not while it’s still unsecured, anyway.
To just blindly assume it’s automatically Republican incompetence is really ignorant. Is there anything the left won’t blame them for?
This could’ve easily been the work of a rogue foreign entity for all we know. And that’s just the point — we don’t know.
hey stupid, how about blowing me? Get up off your high horse and smell the coffee. You’ve got Trump, kinda’ says it all, doesn’t it? Who the hell else would do this kind of cheap shot crap? foreign entity my ass. And for that matter, what the hell is going on in the supposed “high tech” field? You geniuses can’t figure this shit out? then tear it down until you get a hold on reality.
And here, we see the defense mechanism of the “tolerant” liberal when presented with hypotheses that may conflict their own bias. The tolerant liberal resorts to ad-hominem attacks, coarse language, and insults before weakly attempting to argue their point, finishing their post on an angry note without actually proving anything.
Hilary put all here info on an unsecured personal server, Bernie’s staffers accidentally gained access to DNC’s database. Your ignorance is astounding.
Typically it’s Republicans who are so cheap as to let their nephews do their IT security. 20+ years of experience and I’ve yet to meet anyone on the left who is that dumb.
Hillary Clinton?
News to me…last I checked the democrat party and candidate’s headquarters were staffed almost exclusively by 20-something millennials who could well be someone’s niece or nephew.
Didn’t sound like it was a blind accusation. Whoever D is, is familiar with voter data such as provided by NGP VAN. But this really isn’t a forum to have a political debate. D was simply using his knowledge to make an educated guess – lighten up.
Thanks for shining a light on this issue folks! Very few Americans realize that their voter registration data is A) a matter of public record, B) freely available to download en masse in many states, C) full of criminally-exploitable data. For example, I downloaded the entire Florida voter database a few years ago, entirely legally.
See for example http://www2.sos.state.oh.us/pls/voter/f?p=111:1:0::NO:RP:P1_TYPE:COUNTY
Indeed, there are some people who, motivated by an odd political agenda (eradicate voter fraud?), enjoy publishing these records. No surprise then that someone has aggregated the freely-shared data into one place. The problem is one of data transformation – sunshine laws meant something completely different when large databases could only be accessed by visiting the records office in person with pen and paper versus downloaded remotely. Not enough state-level politicians and bureaucrats have internalized this new reality (new circa 1990s).
Stephen Cobb, CISSP
This fact is quite incredible. It truly is amazing to think how easy it is to find data on someone. Heck, if you have their address, and sometimes just their name and county, you can go to their county’s website and search for it. Some counties don’t allow this but many do. he web is full of data that is, in and of itself, insignificant, but if you dig and branch out, possibly Google search someone’s username and see if they are registered on another site that gives you more information about them, you can find a lot. And that is in the open. Hackers can get even more info. In reality, nothing is ever 100% safe.
Just contract out — Spokeo, Intelli.us — that’s how they operate. Additionally, they routinely add back in people who have “opted out,” and so there isn’t even a real opt-out. When they correlate incorrect data, there’s also no official way to correct it.
Please tell me that there is no way for a party to change a citizens vote or even lose it.
That depends. How do you feel about dimpled chads?
I’m just trying to figure out how Chad got pregnant. 😀
— Tom Brokaw
Now we know: unprotected activity. 🙂
Your question has no relevance to this database or surrounding issues.
I’m interested in the voting record. I notice the fields are zero or one. Would that be true/false yes/no? They have a record of you voting, but not what your vote is correct?
I am not able to say what they have and what they don’t have. We’d have to ask them – if we can figure out who THEY even are. Technically, they shouldn’t know what your vote is unless you tell them in some survey or something, right?
Ron, you are correct. Voter records do not contain voting choices marked on a ballot, only whether you have voted in a specific election or not.
Primaries are usually split by political party. This is how they would know if you tend to vote Republican Democrat or independent. It is strictly something they learn in the primaries.
Since our elections are designed to use secret ballots, I can only guess that any “how they voted” information is derived from which party’s primary they voted in, not (we hope!) from actual votes on the ballots.
Who gives a shit ? I vote for the Dems and I don’t care who knows it !!!
That’s fine, but there are people who live and/or work in areas where your political affiliation can affect your ability to get a job, job advancement, and pay.
I grew up in a town like that, and I remember my Dad being afraid to register with the Dems because it would hurt his ability to make a living.
It shouldn’t be that way. I’d like to see party affiliation be available to the parties, but not necessarily public records that can be posted publicly on the Internet.
Government should only be allowed to do what they do well. Government does nothing well, except for screwing up and spending money. Those activities should be eliminated.
Government is no better or worse than private enterprise at doing things. Try calling customer support for any major cable company. Ask SONY how secure their data was.
Government should do what needs to be done that cannot be trusted to the greed of private enterprise. LIke inspect meat.
Jakob’s claim is based entirely on ideology, not at all on fact or reason.
“Government is no better or worse than private enterprise at doing things.”
Actually, studies show that government is more efficient than private organizations.
There is not a study on the planet that would come up with that. Market based activity uses price structure for calculations. In today’s times the market is heavily warped due to government intervention but still provides vastly better mechanisms for determining costs.
Would that be a government study that came up with that conclusion?
Actually, studies show that government is more efficient than private organizations
Said nobody who actually worked on a government contract. Note, I did not say “was employed on”.
You should check again Gov. Has more Cost Over runs! That’s why OUR Taxes are so High to Pay for USELESS Gov Workers! The Only Gov. Workers Who COUNT are the MEN & WOMEN SERVING in OUR MILITARY! The Rest are a WASTE OF MONEY!
After thinking about this…While I don’t know that one can find where any studies show that government is more efficient than private organizations, I do know some governments that one can study that demonstrate how inefficient government is relative to private enterprise:
China (esp. pre 1990)
Soviet Union
North Korea
Venezuela
Vietnam
Kampuchea
etc.
etc.
etc.
Could this be tied to Romney’s “Project Orca” project back in 2012? I worked on the war-floor on election day for this, and the system was supposed to have all Voter information tied into it, where a volunteer would be standing behind the check in desk, and check that person off of the database. The system was supposed to be able to predict how the person would vote, and give Romney’s campaign a heads up of how things were going. However, the system failed miserably on election day
Can’t be because the data are from Feb/Mar 2014 or thereabouts.
GAWD you guys rock.
I’m too interested in the fields like “general_*” or
primary_*.
how current are these?
Not sure. The data appear to have been last updated in March 2014, but they don’t have info for every person. So for a lot of folks I quickly skimmed, there were just “O” for specific primaries and elections, but I did see some “1” for 2010 stuff. Frankly, I didn’t want to look at the data too much – just enough to get a sense of what might be in there. The fields went up to 2016 primaries, and of course, the primaries haven’t occurred yet and anything after March 2014 might not be in the database at all. But again, that’s my impression: don’t hold me to it, okay?
If you have the IP address, then you can track that down to the ISP. Contact the ISP and ask them to contact the customer. Let them know you will publicly post the name of the ISP in 72 hours.
Just an example, media companies track down IP addresses all the time to combat piracy.
There are some things that are best handled by the feds. Chris and I decided to go to them and let them do their job and bring their resources to bear on this one.
I’m very familiar with how to do notifications, thanks.
Actually, IP addresses are assigned to “Autonomous Systems” (ASes). Most corporations have their own ASes; those IP addresses are allocated to them, not to an ISP. A DNS lookup of the IP address will yield the domain name, and a whois lookup will yield the owner of the domain.
Looks to be a mongodb database based on the technical json structure. A database that size would need technical support. Reach out to mongodb with the IP address. They should be able to determine who is using their mms service to monitor that database. Cheers.
Now that it’s secured, I can reply. Yes, it was a MongoDB installation. Even if MongoDB could determine who they would never tell us. They might, however, respond to a govt inquiry or request for them to contact the user with a note to secure the dbase.
It is terrible situation.
here is another one for Iowa on Google docs.
[link deleted by DataBreaches.net]
i located it just by doing a Google search
[link deleted by DataBreaches.net]
good times
Sorry, but I removed the links as I don’t like linking to what are essentially data dumps of personal information – even if they’re public records. But you’re right, those lists are easy to find. And that concerns me, too. I value transparency and accountability, but we’ve got to rein in the widespread sharing of our personal information.
The one from Iowa linked above by silent observer which was redacted by DataBreaches.net seems to be in the exact same format as the database described in the article, down to the field names, though the complete list of field names is not visible unless you go to Tools > Select Columns. This may provide a clue to the owner of the database described in the article, and/or how it was generated.
A lot of data passes through Nation Builder on its way to customers who may then compile the list with other data, assign their own uniq_id etc. Here’s Nation Builder’s statement today
It certainly does, however NationBuilder’s default field names (if the information on its website is accurate and up-to-date) are different than the ones shown in the original article and in the link above. Please compare: https://elections.nationbuilder.com/about/data_columns In contrast, the Iowa database that was linked to above and the database discussed in the article use exactly the same field names, which deviate from those provided by NationBuilder despite that obviously being the ultimate source of the data.
The field names in the image in the story were not from a csv file.
What’s the site/software
this kind of BS is *not* supposed to happen by *accident*.
There’s sloppy infosecurity everywhere you turn. And that’s assuming, for now, that it was accidental.
Nothing accidental is supposed to happen, by definition, so your statement is without useful semantic content.
so if nr vickers actually accessed this data then he directly violated the law and should be prosecuted no matter his attempt at explaining an excuse as to why he was performing actions he was not legally authorized to do
True
Oy vey, the goyim know we are data-mining them. SHUT IT DOWN!
Thanks for taking action and bringing it to the Feds. A lot of people would have exploited the situation.
Chris’s motivation to get these leaky sites secured and to call attention to the ongoing lack of adequate security of databases with our personal information. It’s a goal he shares with this blogger, so yes, when we couldn’t locate the owner within 24 hours, we agreed that for the public good, we’d start contacting federal agencies and California.
It should be safe to say that a Democrat created the site in question, Republicans aren’t smart enough to build such a website, they’re all a bunch of dumb hillbillies.
“Once you generalize you’re instantly incorrect”
Statistically speaking, its impossible for every single Republican to be the same. Comments like that are just ignorant and pointless. Next time, think of something intelligent to say.
You sound like the dumb hillbilly here, making generalized statements like that.
Folks: most of the tips that came to my site about the source of this database pointed to Republican-associated campaigns or entities. Only 1 or 2 suggested Dems. At the present time, I still don’t have specific and exact knowledge of whose database this was. If/when I find out, I will publish that. In the meantime, can we focus on the issue of whether a huge database – even with public records – poses a risk to our security and privacy.
“Know thy enemy” — which you obviously don’t. That “bunch of dumb hillbillies” controls both houses of Congress and 2/3 of the state governorships and legislatures.
Typical leftist comment. Both parties are very capable.
Actually, that comment was not typical of leftists at all. OTOH, “typical leftist comment” is a typical right wing sentiment.
Thank you for notification about this problem.
Thank you for notifying! 🙂
Thank you for arriving late to the party Chris Vickery but I’m sure that all the good people down at the NSA already have the situation 100% under control… cuz that’s what they do! May I remind you that all of your “investigating” is taking away work from dedicated NSA union members, and that ain’t right! Do yourself a favor and go investigate Steve Harvey, or maybe even Justin Bieber (that little turd!) Leave the REAL dirt digging to the professionals. Now get back to your paper route, or whatever it is you do for a living… stop holding your subscribers hostage. I bet you you list “fishing expeditions” as your line of work for tax purposes huh! Yeah, real smooth.
Poor troll attempt.
Yes thanks for bringing this to the attention of the FED’s. Now we just have to make sure they follow up on it and it’s not just another 1 or 2 day TV blurb. As for the sad sack “Rocky J Squirrel” kind of sounds like an old guberment worker from the days of punch cards, Just couldn’t get beyond fortran or cobol but still bringing home those big bucks of retirement because of his union membership. Too many guberment employees doing NOTHING CONSTRUCTIVE and getting paid way too much for it including benefits.
Why aren’t the feds issuing blurbs/alerts/press releases to alert entities to go check their damned dbases for exposure on this port, etc.?
As long as Chris keeps feeding me leaks, I will keep reporting on them to try to keep this in the public’s awareness until we get more IT and infosec folks doing a better job.
I wish the FTC would also issue something that this is a known risk and that an entity that isn’t addressing it isn’t engaging in “reasonable security” under the FTC Act – and could face a 20-year monitoring program under a consent order.
How is it that when someone illegally pirates copyrighted entertainment content, law agencies responsible for enforcing copyright are aware and able to trace it, and can report what you downloaded, when you did it, and even the browser used to it; but federal entities continuously shrug their shoulders that they “can’t” figure out who breaches their supposedly secured databases containing sensitive, classified or otherwise privileged information?
I know some of the breached information (as above) is public record, but that doesn’t mean it needs to be made available anyway. There are so many ways that data in the publicly accessible domain could still be used in illegal and aggressive ways.
As much as I love technology, going off the grid starts to sound a little better every time I hear about something like this! 😉
you can thank google and farcebook for making it a thriving business model. They just love to track your every move and sell it to anyone. How else do you think they make so much money? Clickthrus? NOT.
Some of the data is still available online.
See:
[links removed by DataBreaches.net]
All you have to do is search for a unique data element name from the database schema.
Mike Davis, CISSP
Anywhere there’s pubic records of voters, you’ll find such data. You don’t even need to search for a data element. But the states and sites that post such data do it by design, and hopefully in compliance with their state’s laws.
How do you think, how many db copies already exist over the world ?
may also include whether or not you voted in the last general and primary elections, whether you appeared to follow a party line vote,
And this information is being collected and stored how? Interesting.
My info is exposed and I will not be voting in this election unless the information is removed. And privacy laws help protect the hard working law abiding tax paying citizens. My cell number is exposed as well…really come on! Who can I send the over chargers too!
I love your sarcasm. At least I hope your not serious. Your information is public record. “Private” data is different, look up PII.
This article and this comment thread really sheds light on how little voters know about public information and the modern democratic process.
PUBLIC INFO. Please look up Public in the dictionary. This is a none issue. Period.
PS. The sky has blue colors most on the day. Please call the government!
Where can we download this database!? This would be great for small business to use and have access for FREE versus the $10,000 per MONTH that only the 1% can afford! So by providing a link to it, it IS supporting small businesses that would like to reach people at their mailing address for postcard, etc. Again, the RICH can afford to reach these people and they are NO MORE HONEST then us small business… Actually us small businesses ARE MORE HONEST because we have to face our customers, where the rich get to HIDE behind lawyers, security, etc. If you rip people off in the bottom 30%, you risk retaliation… SO YOU DON’T
Someone please email me the link to this database!!! [email address deleted by moderator]
You’re so honest but you want to use someone else’s intellectual property for your commercial gain. I see….
This is precisely why we try to ensure that databases are secured before we report on leaks – because there are people out there like you who will try to take advantage of the situation.
And you’re so intellectual that you think that this information is the ” intellectual property” of anyone other than the individual voter and that voter’s registration office.
Not information, a structured and formatted database. Try hacking Experian’s credit report database and then tell them that isn’t their intellectual property.
191 million voters? That seems about right from the percentage of people who actually vote. Ha ha!
I dunno…that seems a little bit high considering the US has a population hovering around 310 million 🙂
I do this professionally and have been trying to warn my employer about our abysmal sec setup, but have never downloaded a dump before. Something like this can help me move the conversation along. Can anyone point me in the right direction. Have Tor, no detailed instructions necessary I understand a measured reluctance, just point.
That’s not going to happen via my site.
And that database has been secured.
Look, folks, I don’t care WHAT your explanation, rationale, or excuse is: You won’t learn where that kind of database is on my site or get pointers to it. My goal is to PROTECT people’s data, not point others to it.
^^ + 100 ^^
Yep. +100 from me too. Nothing beats integrity.
We live in an age, where the blessing of an interconnected world is marred by a lack of personal privacy. Databases online and in enterprises contain valuable personal information, which if stolen, can be sold or maliciously used by hackers. For example, according to one marketing firm consulted by researcher Chris Vickery, a database of all American voters can go for as much as $270,000.
Despite such a demand for sensitive information, databases are often vulnerable to data theft. The consumer obviously has no control over the safety of their information and rely on the vendor and the technology for protection. However, vulnerabilities still exist and so does careless errors done on the part of data stakeholders and system administrators. On December 20, researcher Chris Vickery contacted DataBreaches.net to say he had found a database with 191,337,174 million Americans’ voter information exposed due to a misconfiguration of the database.
Such examples prove that knowing where the sensitive information exists and, how it should be protected is imperative. As technology improves and the requirement of data collection expands, such threats and attacks will continue to grow.
If this is at all accurate it would indicate that the personal information of over 81% of all the registered voters in the nation was posted online. I would find this hard to believe, unless it was the result of Hillary and Bernie’s infighting over just this kind of a list.