The non-profit organization Man Alive in Baltimore provides substance abuse treatment and mental health services to some of the city’s neediest residents. As if the facility didn’t have enough challenges, on August 24, they were hacked, and a patient database with sensitive personal and treatment information was put up for sale on the dark web.
DataBreaches.net was first tipped to the incident over the last weekend in August, and after confirming that the sample data provided by the seller, “Return,” appeared to be genuine, contacted the facility by phone and through their contact form to make sure they were aware of the breach. Getting no response because it was after-hours, DataBreaches.net contacted the Baltimore office of the FBI to alert them. Disturbingly, they refused to do anything to get in touch with the facility to alert them. The same organization that wants everyone to tell them about breaches is apparently unwilling to return the favor by notifying victims that they have become victims.
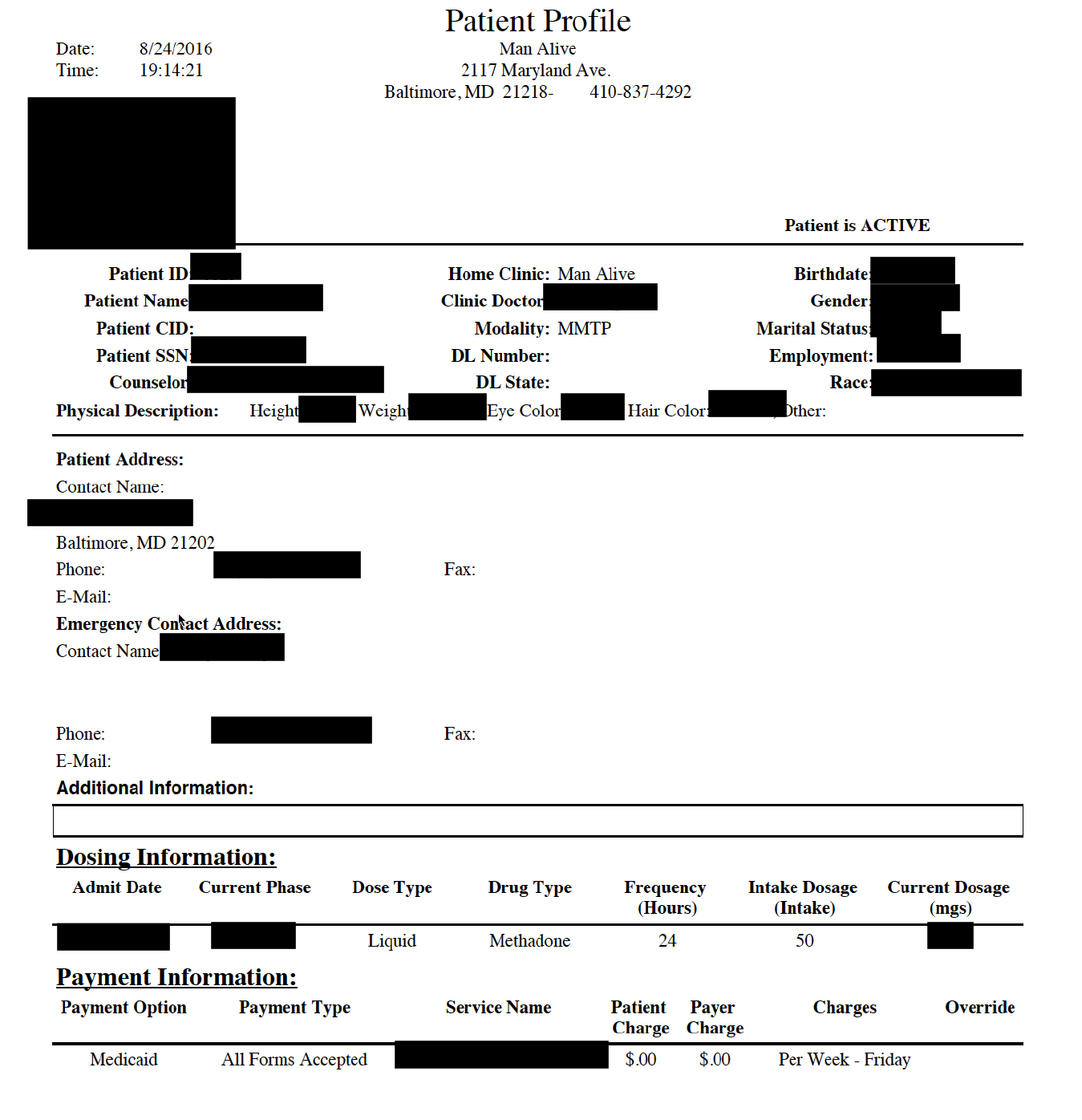
Information Compromised
As seen in the sample data, a patient profile includes a picture of the patient as well as fields for:
- first and last name
- date of birth
- full Social Security Number
- postal and email addresses
- home and cell phone numbers
- a physical description of the patient (height, weight, eye and hair color)
- race
- driver’s license number and state
- marital status
- employment status
- emergency contact person; and
- whether their status at the facility is active or inactive
Not all patients had information entered for all of the above fields. The profile also includes information on their treatment, including:
- date of admission
- treatment modality
- whether they are on methadone
- the names of their doctor and counselor
- dosing information; and
- payment option
Many of the patients in the sample appear to be on Medicaid although some indicated commercial insurance or a managed care organization (MCO). The profiles did not include insurance account numbers, and many profiles did not include information like driver’s license numbers.
The Hack
The attack on Man Alive occurred on the evening of August 24. In a chat with DataBreaches.net, Return, who appears to be of Russian background, described how he compromised them: “With the help of the social engineer, applied to one of the employees. Word file with malicious code was downloaded. After that the PC be infected loader”
For Sale
On August 24, 2016, “Return” posted the following on crdclub.su:
—SSN+DOB database, MD, 43kI’m selling a “full info” database, Maryland state. In PDF format. 43k records from medical clinic.
A sample: <“PatientProfile.pdf” – see attachmments for screenshots of sample records>Price: $300
Payment: BTC onlyJabber: [redacted by DataBreaches.net]—
The sample consisted of 727 pages of unredacted patient profiles containing a wealth of personal and treatment information on 633 patients. As of September 7, a 727-page file with unredacted patient profiles was still available online.
Although Return claimed that he had also acquired patient records from the mental health treatment part of the clinic, he declined to provide any evidence of that, and DataBreaches.net could not confirm that claim. Nor could this site confirm that there were actually 43,000 records exfiltrated.
When asked whether he had sold any of the patient data, Return indicated that he had sold some of the identity information such as Social Security Numbers and Date of Birth.
Another Attempt at Ransom
In our chat, Return indicated that he had given Man Alive the opportunity to protect the patient information from sale by paying him 15 BTC. “This is very confidential information, so why not earn money)),” Return told DataBreaches.net when this blogger inquired about the ransom demand. “I think they spend more money on the court, if customers learn about the disclosure of sensitive data;)” he added.
As of September 7, there had been no payment.
Man Alive’s Response
Given the sensitive nature of the patient information, publication of this post was delayed to allow Man Alive time to get their notification ready and their incident response started. Despite multiple requests, Man Alive, through their external counsel at Miles & Stockbridge, did not provide any statement or answers to any of this site’s questions concerning the number of records compromised, whether mental health patient records were compromised, and what the clinic is doing in response to this incident. This post will be updated if they do provide any information. Because they are a HIPAA-covered entity, this incident will likely be reported to HHS, and we should see a substitute notice or notification letter at some point.
Update: On September 9, Man Alive reported this incident to HHS as affecting 860. This post will be updated if DataBreaches.net receives more information explaining the discrepancy between the hacker claimed and what the facility reported.