Compiling data for Protenus, Inc.’s breach barometer should be relatively routine and straight-forward. In May, however, it wasn’t. Here’s a rundown on the factors that complicated our analyses:
Investigating patient data put up for sale on the dark web. Determining whether the breaches were legitimate or fake turned out to be headache-inducing, as the following scenarios illustrate:
A reliable source provided DataBreaches.net with data that appeared to be from Pain Consultants, PLLC in Washington State. According to the threat actor who provided the source with the data, there were 1200 records that included name, address, date of birth, telephone number, social security number, medical details, and health insurance information.

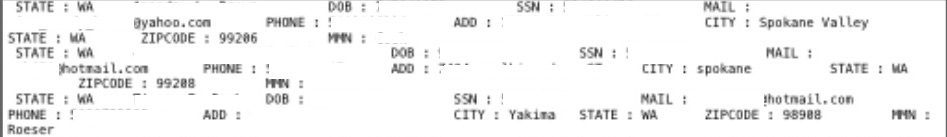
This incident was included in our analyses even though the provider did not respond to inquiries sent by this site.
A second listing, purportedly for the personal information of medical marijuana caregivers and patients, offered “thousands” of such credentials, but that vendor refused to provide this site with any samples that would permit us to attempt to verify their authenticity. As a result, we decided not to include these data in our analyses for the month, even though we could think of one recent breach they might have come from.

A third listing, on yet a different dark web marketplace, offered a database with records that they claimed were from 70,000 Allscripts patients:
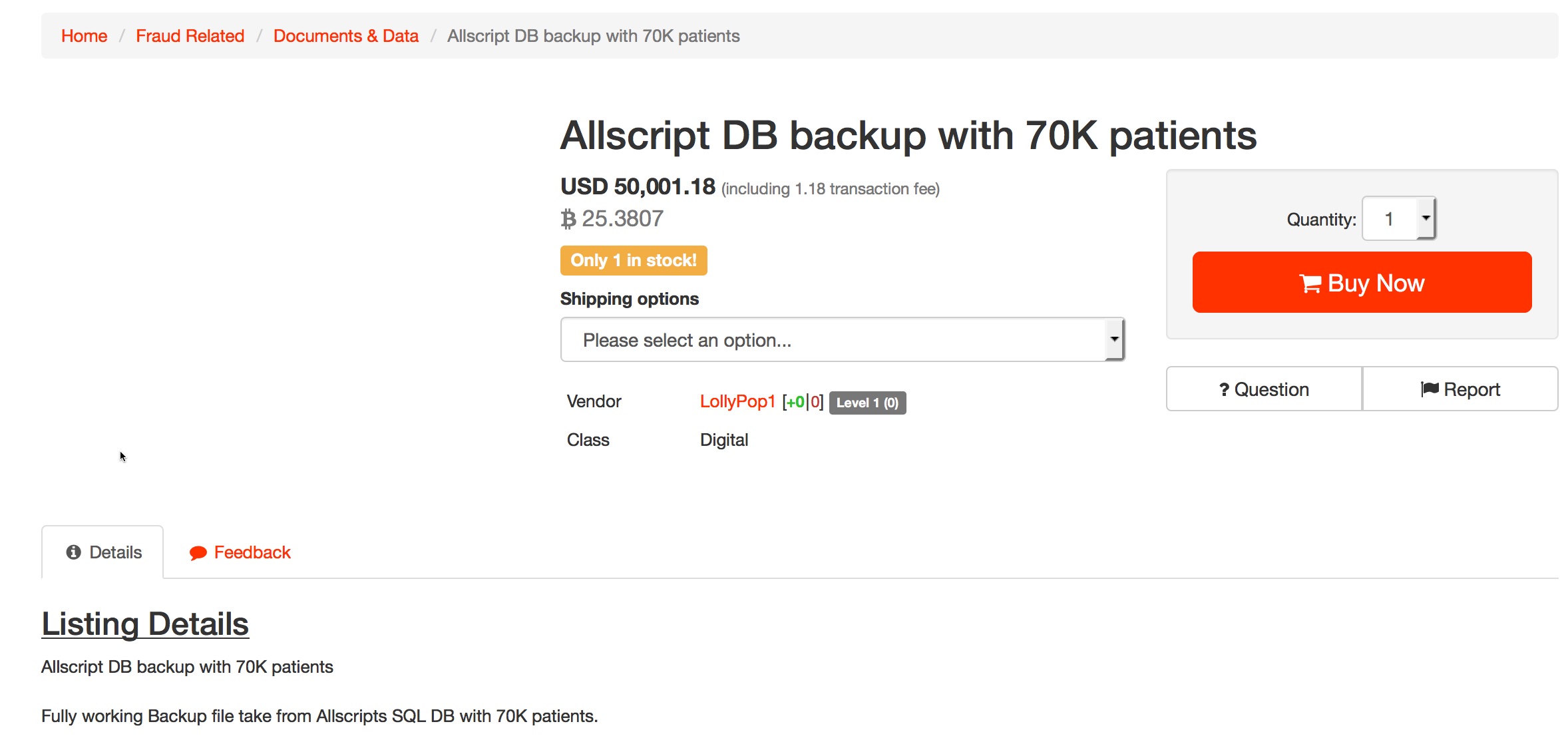
DataBreaches.net was able to contact Allscripts, who investigated and subsequently informed this site:
We are aware of this listing. We take the security of our data very seriously, and we’ve performed an investigation into this matter. Our conclusion is that this listing was posted by a ripper (an individual who commits fraud on underground forums), and that it is a fraudulent listing. Additionally, we consulted with law enforcement, who concurred with our conclusion. Thank you again for reaching out to us.
As a result of their investigation and contact, the so-called “Allscript” data were deemed as “fake” and not included in our analyses.
A fourth listing for a “MedicalDB Leaked Database | 2,000 records | 100% Original and Unmodified” was supposedly from a dump in October 2016. The vendor kindly provided DataBreaches.net with a sample of patient records. The patients all had Texas addresses, and dates of birth in 1937 and 1938. Their records included their name, address, telephone number, date of birth, Social Security number, and some other fields that were not clearly labeled. 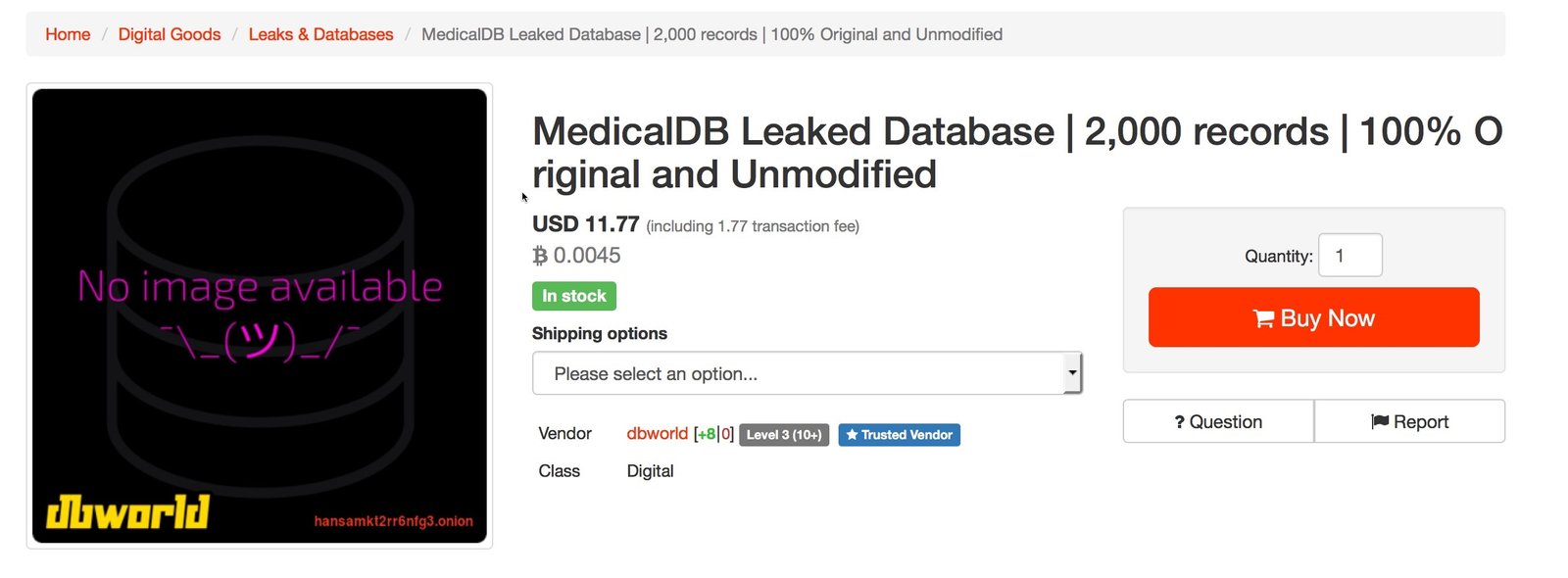
Although it seemed likely that these data were from a real patient database, it was unclear whether it might be a breach we had previously reported on/included, so it was not included in our analyses for the month.
A fifth listing for 5,200 patients’ information was purportedly from “LifeMedical” in Minnesota. The incident was included in this month’s analyses, but because LifeMedical firmly denied that those are their patients’ data when DataBreaches.net contacted them, the incident is coded as “unknown entity.”
But databases on the dark web were just one factor that took time to investigate. In addition:

Three patient records databases were dumped by TheDarkOverlord. Two of the databases dumped by TheDarkOverlord in May – purportedly from Aesthetic Dentistry in NYC and OC Gastrocare – had been mentioned publicly in the past and were included in earlier Breach Barometer reports. The third data dump, from Tampa Bay Surgery Center, has been included in this month’s analyses even though they did not respond to an inquiry from this site. Of note: none of the three claimed breaches has appeared on HHS’s breach tool.
Keeping up with leaking servers was a herculean task in May. Here are just some of the incidents/leaks DataBreaches.net investigated this month, although none are on HHS’s breach tool as of the time of this report:
Bronx-Lebanon Hospital Center patient data leaked from a misconfigured backup server managed by iHealth Solutions. The leak was discovered by Kromtech Security. We really don’t have a solid estimate of how many patient records were in the 500 MB of data Kromtech initially downloaded from the leaking server, so have used the number offered by Kromtech.
An untold number of files with medical information on workers compensation claimants was exposed due to a misconfiguration of a server that appeared to be owned by DocuCents. That leak was discovered by @s7nsins.
Neither DocuCents nor its parent corporation responded to multiple notifications and inquiries sent by this site. The data were secured after DataBreaches.net contacted one of its clients, GEKLAW, and alerted them that their clients’ information was exposed. GEKLAW was only one of numerous firms that had client data left vulnerable or exposed.
The incident has been reported to the California Attorney General’s Office by DataBreaches.net.
An untold number of files with medical information of cancer patients was leaked by CureSeq. The leak was discovered by Kromtech Security, who was unable to get a response from the firm.

On June 8, DataBreaches.net also sent notification to CureSeq with the subject line:
URGENT: You are leaking patient/other data from your Rsync backup
There was no response.
DataBreaches.net contacted some of their clients, including the University of California San Francisco Dept. of Pathology and Stanford Medical Center Surgical Pathology. Contacts were attempted via email and telephone.
None of the covered entities contacted responded to notifications.

DataBreaches.net referred the CureSeq leak to the California Attorney General’s Office, and is considering filing a complaint about it with HHS.
And if you needed even more messiness for the month….
For some incidents, we had no numbers. That’s not unusual, of course, but this month, there were a number of incidents that each may have had numbers in the hundreds of thousands or millions. Not having those numbers leaves us with what may be a truly significant underestimate of the number of breached records in May. In addition to the incident that we believe is linked to DocuCents, the True Health Diagnostics incident, the Molina Healthcare incident, and the OneLogin incident each could have exposed significant numbers of patient records.
So how bad was May?
Your guess is as good as mine at this point, but here’s the final list of entities whose incidents were included:
- AeroCare Holdings
- Arizona Department of Health Services
- Beacon Health System
- Blue Cross and Blue Shield of Kansas City
- Bronx- Lebanon Hospital Center
- Capital Nephrology
- Children’s Mercy Hospital
- Clinton County Board of Developmental Disabilities
- D. Andrew Loomis MD, Pau la Schulze MD,Tammara Stefanelli MD, Christen Vu DO, Anja Crider MD, Susan Clabots-Sheets ARNP
- Diamond Institute for Infertility and Menopause
- DocuCents (?)
- Dr. Kadri (Advanced ENT Head and Neck Surgery): TWO incidents
- Jones Family Practice, P.A.
- LCS-WP LLC d/b/a Walnut Place
- Louisiana State University
- Mecklenburg County, North Carolina
- Mississippi Division of Medicaid
- Molina Healthcare
- N. Fred Eaglstein, D.O. d/b/a Dermatology and Laser Center
- Neeley-Nemeth, LLP dba Barton Oaks Dental Group
- New York City Health and Hospitals Corporation – Coney Island Hospital
- Nova Southeastern University (NSU)
- OneLogin (Stanford Medical School patient portal login)
- Pain Consultants, PLLC –> Puget Sound Pain Clinic
- Robert F. Himmelman
- Rutland Regional Medical Center
- Sound Community Services, Inc.
- SSM Health – DePaul Hospital (Dr. Syed Khader)
- Stephenville Medical and Surgical Clinic
- Tampa Bay Surgery Center
- Tehachapi Valley Healthcare District and Adventist Health (2 CEs)
- Trios Health
- True Health Diagnostics
- University of Wisconsin Hospital
- UNKNOWN
- Virginia Mason Medical Center
So now that I’ve cried on your cybershoulder, trot on over to Protenus and read their report on health data breaches in May.