Leon County Schools in Tallahassee, Florida has more than 34,000 students, more than 2,400 teachers, and a total of 4,300 employees. That’s a lot of students and teachers to notify when you discover that a third-party vendor’s mistake exposed their personal information for almost two years. But it’s not as much as the vendor, Florida Virtual Learning School, having to notify 368,000 current and former students.
 Neither Leon County Schools (LCS) nor Florida Virtual Learning School (FLVS) were aware of any leak until February 11 and 12, when DataBreaches.net saw a listing on a forum for student and teacher databases from LCS and reached out to notify LCS. The individual who uploaded the databases to the forum, “$2a$45,” claimed that an unnamed vendor’s error had led to the breach, and that the full LCS leak contained, “records of everything (including vaccinations, incidents, report cards, students’ sibling information, teachers’ SSNs etc).”
Neither Leon County Schools (LCS) nor Florida Virtual Learning School (FLVS) were aware of any leak until February 11 and 12, when DataBreaches.net saw a listing on a forum for student and teacher databases from LCS and reached out to notify LCS. The individual who uploaded the databases to the forum, “$2a$45,” claimed that an unnamed vendor’s error had led to the breach, and that the full LCS leak contained, “records of everything (including vaccinations, incidents, report cards, students’ sibling information, teachers’ SSNs etc).”
“Today,” he wrote, “I’m releasing information containing 35k students (+18k parent address information) and 4k teachers. I have to leave some of the sensitive data out of the leak.”
According to his forum post, information on the teachers included the following fields:
teacher_first_name, teacher_middle_name, teacher_last_name, teacher_sex, teacher_dob , teacher_address, teacher_city, ,teacher_state, teacher_zip, teacher_cell_phone, teacher_phone, teacher_email
while information on the students included the following fields:
stuid, studentid, student_name, birthday, race, race_desc, ethnicity, sex, address, zip, phone, gifted, lunchpin
Parents’ information was also included in the databases he made available for download.
None of the data were encrypted and no passwords were hashed. Everything – everything – was in plain text.
“I might include more information later on, if people are interested in the data,” $2a$45 wrote.
DataBreaches.net was interested, of course, and reached out to both the poster, to try to obtain more information, and to the district.
Over the next few days, $2a$45, who described himself as being a male living outside of the U.S., provided this site with samples from some other LCS tables that included students’ vaccination records and also a table of disciplinary records. His comment about the nature of the incident was that, “Basically, the vulnerability that this server had was purely an access control problem. They didn’t know how to protect their files.” His comment about the vendor’s security failure would be echoed by another researcher who had independently stumbled over the same data one year earlier.
Interestingly, and to his credit, $2a$45 did not seem to be seeking any money for the data or even a bug bounty, and after discussion with this blogger, he informed me that this site could give the school district his email address to contact him and that if he could, he would try to help them secure the data – or at least tell them where their security had failed.
On February 16, LCS called DataBreaches.net in response to the email this site had sent them. They had not been aware of any leak or breach until they looked into the data this site sent them. DataBreaches.net agreed to hold off publishing anything until they had a chance to investigate and to notify parents. DataBreaches.net also provided the publicly available information to the Florida Department of Law Enforcement who the district had contacted for assistance.
 Today, the district’s Executive Director, Technology & Information Services contacted me to say that notification about the incident was now public and that it had been a third-party vendor who was responsible.
Today, the district’s Executive Director, Technology & Information Services contacted me to say that notification about the incident was now public and that it had been a third-party vendor who was responsible.
FLVS’s breach reportedly impacted 368,000 current and former FLVS students, including those from LCS. Here is the relevant part of FLVS’s public notification:
Florida Virtual School Responds to Data Security Incident
A NOTICE TO STUDENTS AND PARENTS
Florida Virtual School (FLVS) recently learned of a potential data security incident involving certain information provided to us by students and parents. We are providing this notice as a precaution to inform potentially affected individuals about the incident and to call your attention to some steps you can take to help protect yourself. We sincerely regret any concern this may cause you.
FLVS learned that unauthorized individuals appear to have gained access to some of our computer systems that stored personal information relating to certain students, parents of students, and Leon County Schools’ teachers. Although the investigation is still ongoing, based on what we have learned to date, we believe that this incident could affect information in FLVS school records, including but not limited to students’ names, dates of birth, school account usernames and passwords, physical school identification, as well as parents’ names and parent emails. We have not identified any evidence that any student or parent Social Security numbers or financial account information were affected. Please note, currently, we are not aware of any fraud or misuse of your information as a result of this incident.
The security incident may also affect a limited number of Leon County Schools’ teachers, where the teachers’ name, Social Security number, date of birth, address, phone number, cell phone number, emergency contact, spouse’s name, personal email address, work email address, and certain demographic information, may have been accessed by unauthorized persons. These teachers are being directly notified by individual notice by Leon County Schools and FLVS is coordinating and cooperating with Leon County Schools in these efforts.
FLVS takes its obligation to protect the privacy of personal information very seriously and deeply regrets this incident. After FLVS learned of this incident, we immediately initiated a comprehensive IT security investigation and hired an independent forensic cybersecurity investigation firm to assist in our investigation and response. FLVS also contacted Leon County Public Schools and notified the Florida Department of Law Enforcement (FDLE) and the Federal Bureau of Investigation (FBI) and we will continue to cooperate with the law enforcement investigations.
As a precaution and to reduce the risk that any student information could be misused, FLVS is offering potentially impacted students one year of identity protection services through Experian, a leading identity monitoring services company, at no cost. These services help detect possible misuse of personal information and protect against identity theft. The offer is available to students whose information was in the FLVS database from May 2, 2016 to February 12, 2018. Qualifying students or their parents can learn more and if impacted by the incident, can sign up for identity protection services at this website www.experianidworks.com/FLVS or by calling Experian at (888) 829-6553 and referencing engagement number DB05741. For more information about these services, please see the “Information about Identity Theft Protection” reference guide, included below, which also describes additional steps that you may wish to take to help protect yourself, including recommendations by the Federal Trade Commission regarding identity theft protection and details on placing a fraud alert or a security freeze on your credit file.
For more information about this incident, or if you have additional questions or concerns, you may contact our dedicated call center directly at (888) 829-6553 between the hours of Monday through Friday – 9:00 A.M. to 9:00 P.M. EST, and Saturday and Sunday – 11:00 A.M. to 8:00 P.M. EST. Again, we sincerely regret any concern this incident may cause you.
Their statement is not totally accurate. In fact, one might characterize it as significantly misleading. According to what their “dedicated call center” (i.e., Experian) representative told me, FLVS is indeed claiming that they were hacked, that the hack occurred on May 2, 2016 to February 12, 2018, that FLVS discovered the hack through a routine security sweep of its system, that the FLVS notified Leon County Schools, and that FLVS didn’t yet know whether the data were available on the dark web or for download anywhere.
Their claims are not supported by the evidence DataBreaches.net obtained.
Let’s start by taking a short walk down memory lane to June 2017, when a researcher who calls himself “Flash Gordon” contacted me privately on Twitter to alert me to some school data he had found. Flash Gordon is not the same individual as the forum poster who uploaded databases. They had each stumbled across FLVS’s exposed databases independently. Sadly, I had not followed up in June, 2017 when Flash first mentioned the leak to me. As our message logs showed, I asked him whether he intended to make a notification, but he did not answer at that time, and then I forgot all about it.
The screenshot below of his messages to me on June 18, 2017 shows that Flash Gordon had found exposed files on 216.127.144.101, which is the IP address of UCompass (FLVS). The data were leaking because Port 443 was open. Anyone using Shodan to search for exposed databases would have found this.
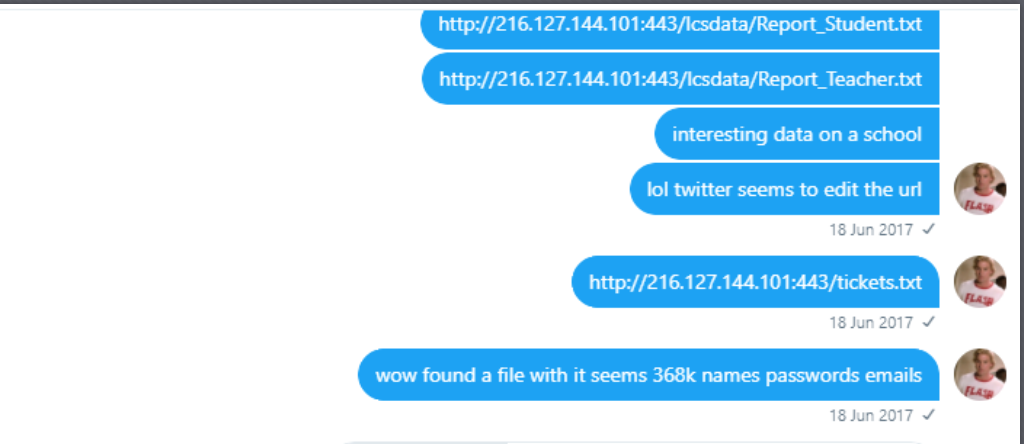
And as the screencap shows, Flash Gordon told me at that time that he had found a file with 368,000 names, passwords, and email addresses. That is the same file FLVS referred to today.
Interestingly, I found myself with two sets of files from Leon County Schools. One set, provided to me by Flash Gordon in 2017, contained many more fields in the student data file than the more recent version that had been uploaded to a forum by $2a$45.
The earlier version had all of these fields in the Student data file:
StuID School_Year Student_ID School_Number Last_Name First_Name Middle_Name Last_Name_Appendage BirthDate Race Race_Desc Sex Ethnicity Race_White Race_Black Race_Asian Race_AmInd Race_PacIs Grade_Level Student_Status Res_Address Res_Address2 Res_City Res_State Res_Zip Mail_Address Mail_Address2 Mail_City Mail_State Mail_Zip Phone Parent ESE_Primary ESE_Other Gifted Gifted_NP Lunch_Status Lunch_Status_Desc Lunch_PIN Limited_English LEP_Student NY_School Homeless HR_Teacher HR_Teacher_PID Last_ERW_EntryCode Last_ERW_EntryDate Last_ERW_WithdrawCode Last_ERW_WithdrawDate Last_ERW_WithdrawReason ZoneSchoolElem ZoneSchoolMidd ZoneSchoolHigh PriorSchool Cohort MigratoryStudent Section504 Bottom_35_Math Bottom_35_Reading Grade_8_At_Risk Survey_2_Match
[Note: DataBreaches.net is not naming the forum where $2a$45 uploaded the LCS databases because although he did not share the most sensitive files, he did share files with student, parent address, and teacher personally identifiable information]. And while FLVS’s “dedicated call center” representative informed me that FLVS was unaware of any databases being exposed or available as their investigation was still ongoing, DataBreaches.net had already notified Leon County Schools and FDLE of the LCS data dump and had provided them with links to the dump. That dump included information on 3.7k teachers, 35k students, and 18k student_parent addresses.
Significantly, from a data protection/identity theft perspective, some LCS databases contained Social Security Numbers. In a private message, $2a$45 informed me that he had tested about 20-30 teachers’ SSN and the success rate was about 60-70%. SSNs in the report_student table had a significantly higher success rate, he reported.
In any event, it seems clear that FLVS had a data leak that they have tried to spin as a hack, hundreds of thousands of current and former FLVS students may have their details in the hands of an as-yet undetermined number of people, and LCS student, parent, and teacher data have been dumped publicly if you know where to look.
Not exactly a good day for FLVS or members of the LCS community.
Update: The Miami Herald uncritically just repeats FLVS’s use of the word “hackers,” even after they were told that the server was left open!
Hackers stole the personal information of more than 350,000 Florida Virtual School students, parents and teachers two years ago, the company announced Friday evening.
The stolen information….
“Hopefully we can bring these criminals to justice,” Fuller said.
IT staffers discovered the breach on Feb. 12 when a cybercriminal posted on a common hacking site bragging that they had acquired the information two years ago, he said.
The cybersecurity firm Florida Virtual School hired found that hackers got all the data from a single sever [sic] accidentally left open, Fuller said.
The server was left open. That’s exactly right. It was not secured. No login was required. So there was no bypassing of code or bypassing of any “stay out” banner. This was not a hack. Nor is the site the database was posted to a “common hacking site.” The site the database was uploaded to is a LEAK forum, and the uploader has no reputation as any kind of criminal. As I noted earlier, he had even offered to help LCS correct the security problem. So who are these so-called “criminals” who FLVS wants brought to justice? People who found their unsecured data and downloaded it? Perhaps FLVS should be grateful for the forum poster who uploaded a database and initiated a sequence of events that made FLVS aware of their screwup.
Shakes head no.
https://memegenerator.net/img/instances/62975478/im-not-saying-it-was-hackers-but-hackers.jpg
Why would they upload the file to a forum?
There are some sites where files are shared……