Soumyarendra Barik reports:
Personal data of 47.5 million Indians — including their phone number, service provider, name, gender, city, email, and Facebook ID, among other things — claimed to be sourced from caller ID app Truecaller is available for sale on the dark web for $1,000 (₹75,000), cybersecurity firm Cyble said. Truecaller, in a statement to MediaNama, however, denied any breach of its database.
Read more on Medianama.
Note that I didn’t find any statement on Truecaller’s site, but Medianama posts a statement from Truecaller:
“There has been no breach of our database and all our user information is secure. We take the privacy of our users and the integrity of our services extremely seriously and we are continuously monitoring for suspicious activities. We were informed about a similar sale of data in May 2019. What they have here is likely the same dataset as before. It’s easy for bad actors to compile multiple phone number databases and put a Truecaller stamp on it. By doing that, it lends some credibility to the data and makes it easier for them to sell. We urge the public and users not to fall prey to such bad actors whose primary motive is to swindle the people of their money.”
DataBreaches.net reached out to Cyble.io to inquire whether, or how, they have actually validated the data in the dataset. The following is their response:
* The data acquired by us appears to have originated from 2019 as here –
https://www.bankinfosecurity.asia/researcher-data-leaked-for-300-million-truecaller-users-a-12519
* The data was acquired from a reputed seller, and they have listed several other verified leaks in the market. That said, the credibility of the seller is undisputed from our perspective.
* Reference: https://twitter.com/AuCyble/status/1265535300970983433
* We looked at certain samples, and the details matched
* Interestingly, Truecaller admitted that the data we have might be real data though (which is ambiguous)
* While Truecaller has denied this leak entirely, however, to-date we haven’t been requested for a sample from their team yet – we are also surprised by how they arrived at a conclusion considering:
* They haven’t performed any validation that the data we have is the same from 2019. Yes, we did highlighted on the original post<https://cybleinc.com/2020/05/26/47-5-million-indian-truecaller-records-on-sale-for-only-1000/> that this leak is not new, and is from 2019 as below
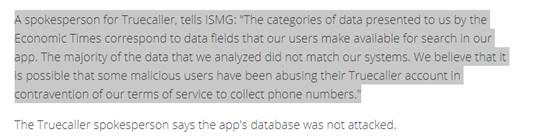
* Their 2019 comment asserted that a malicious user may have abused their service. Reference
here<https://www.bankinfosecurity.asia/researcher-data-leaked-for-300-million-truecaller-users-a-12519>:
* At this point, we have no evidence whatsoever suggesting that Truecaller was hacked in 2019 or recently. As you’d imagine, there are a number of other avenues which may cause data leaks and spills such as misconfigured apps, systems, third party API etc. In 2016, the BBC reported that an investigation by Factwire, an investigative news organization, determined that Trucaller searches could be conducted on the app provider’s official website without even installing the software. There have been known issues with the app in the past.
Many of our team members are using Truecaller and like the app. We hope that they investigate these issue more seriously and work closely with the research communities. In case there are issues or legit security concerns, we trust they will take appropriate actions to mitigate the risks, and in the event of a data leak/spill, they will inform the affected parties/users.