One of the k-12 district ransomware attacks that DataBreaches.net has been following involves Walled Lake Consolidated District in Michigan. The district suffered a ransomware attack on or about October 10 that they are still working to recover from. But while they focus on recovery of systems, the threat actors have tried to pressure on them to pay the demanded ransom by starting to dump files that contain employee and student information. To date, the district has not publicly acknowledged that data is being dumped.
On October 24, the threat actors dumped some limited data as proof of access to, and acquisition of, files from the district’s systems. It was clear from the threat actors’ comments on their leak site that they had read the district’s earlier statement about the attack and wanted to prove that they had exfiltrated data.
They subsequently dumped even more data including personal and personnel information on teachers and information on students.
This time, they quoted a statement from the district’s recent update on the attack and then responded to it:
With the recent hack of Walled Lake Schools’ network on Oct. 10, 2020, our ability to sufficiently prepare for the Nov. 4 scheduled return to in-person learning has been compromised. But better to say, school does not care about anything like privacy and security and have no wish to stop sharing or back to normal work.
Yesterday, DataBreaches.net reported that we had reached out to the district last week to inquire what the district was doing in response to the first small data dump. This site received no response at all.
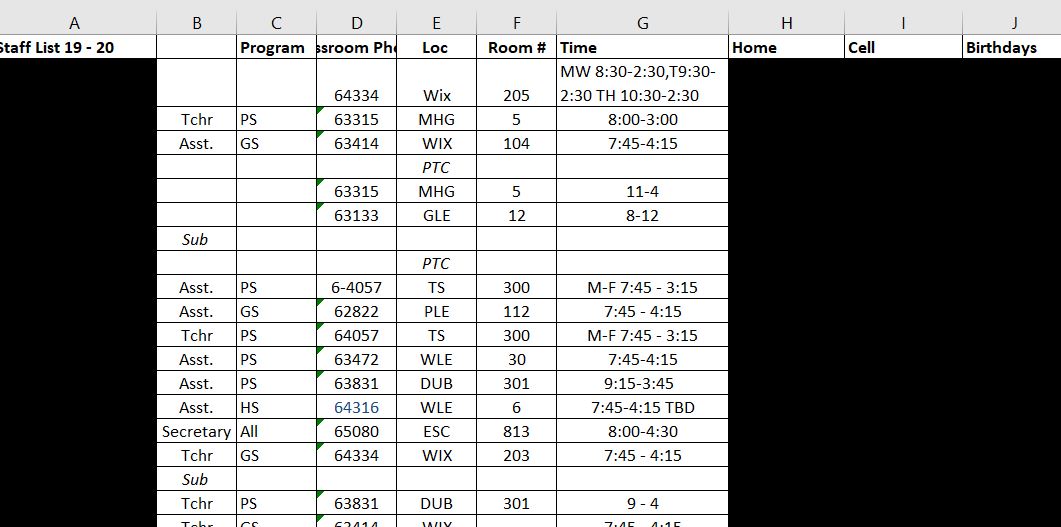
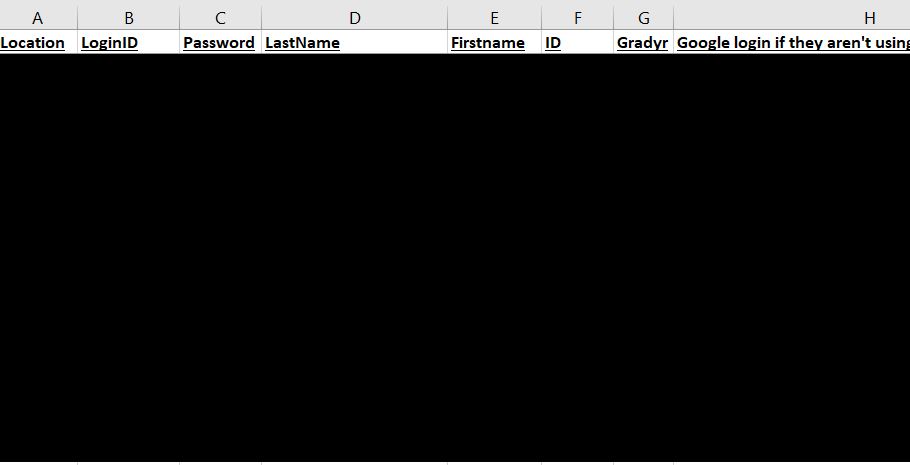
DataBreaches.net is not going to get too specific about how much data the threat actors have already dumped, but in looking through just some of the files, I saw salary schedules, personnel records involving certifications and assignments, files concerning retirements and resignations, and a spreadsheet with teachers’ names, assigned classes and rooms, their home phone numbers, cell phone numbers, and month and day of their birthday. I also noted a spread sheet with student IDs and logins to the district, and staff injury reports with personal details. And that was just a quick skim at some of the files that had been dumped.

The district’s October 27 update makes NO mention of knowing that personally identifiable information is already on the dark web. They write:
We apologize for any inconvenience and appreciate your continued patience. This targeted computer hack of Walled Lake Schools was impossible to anticipate and the timing could not have been worse. However, we are excited to have students return safely to in-person instruction and want to make sure all of our systems are fully operational to ensure a smooth start to the new school year.
DataBreaches.net questions their claim that the attack was impossible to anticipate. Experts have been warning schools for years about the increase in attacks on K-12 districts (e.g, see this 2017 news report) , and there have been even more warnings in 2020. That’s just this blogger’s opinion, though. Others may obviously disagree.
In any event, because they did not respond to this site’s inquiry, we have no indication that they have warned employees and parents to take steps to protect themselves from identity theft or fraud attempts. DataBreaches.net therefore decided to publish some limited proof today in this post so that parents and employees hopefully find out that they need to take steps to protect themselves.
Hopefully, the district will start to publicly acknowledge the scope of the breach and advise employees and parents what to do to protect themselves and what the district will do to offer them any protection services or mitigation services.
I can assure you they haven’t notified employees or families the extent or even that their information COULD be compromised. I have a close friend who teaches there- and they’re suffering the consequences due to the districts “head in the sand approach”