I’ve always resisted any urge to write a “worst breaches of the year” piece at the beginning of December because I just know that if I do, there’s going to be something that would be on my “worst” list if only I had waited a few weeks.
The Conti ransomware attack on Leon Medical Centers in Florida is one of those breaches that proves I was right to wait.

Since DataBreaches.net first reported on the attack and the threat actors’ claim that they would be dumping data on more than 1 million patients complete with SSN, photos, and other information, Conti has begun to dump some data. Folders and files that were dumped on Monday were from the directory labeled “finance.” The folders and files revealed a somewhat dizzying array of files with payroll, banking, bank statements, card statements, and more. Some of the files appeared to go back to 2005, including some of the payroll data.

Check register files, like the one illustrated above, displayed the check number, employee name and full SSN, employee ID number and the net amount of pay for the week. Other files contained other information on employees and their positions, and yet another file contained the emergency contact numbers for financial affairs employees.
How Did Conti Do It?
DataBreaches.net asked Conti if they would reveal anything about how they gained access to LMC, and they did. A spokesperson sent the following statement, which appears to be what they may have written to LMC:
In September we sent you an email containing the exploits in the attached document. It was opened by a user with citrix access. Then, using the CVE-2020-0796 vulnerability, rights were raised to the local administrator. After that, using the program Blood Hound were found computers where there are authorization data domain administrators. The computer was found, we were able to get access to it and spread the network. We found local administrator computers where passwords to different resources were stored in the open. We found out where there were backups, SQL, etc. Then we found the local computers of your domain administrators. With the help of mimmkatz, passwords of administrators on these computers were obtained. Going to the RDP on them, we found Key Pass programs from where we got access to your AV server.
What Other Data Did Conti Exfiltrate?
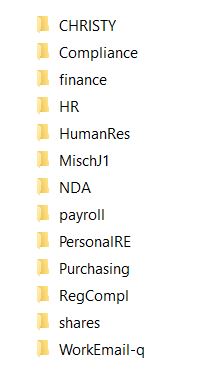
Conti also gave DataBreaches.net exclusive access to some of the other data from LMC they are preparing to dump. In addition to data in the folders illustrated in this image, they also provided access to files in folders called “0000/” and “/scan/.”
The files DataBreaches.net saw contain a great deal of operational files and documents, including human resources files involving named personnel who were tested for COVID-19 and their test results. There was also other health information on employees, including some information on “break the glass” settings for named patients. There were also files involving claims by employees and other files containing more sensitive employment or disciplinary issues involving named employees. Many of the folders and files were compliance-oriented and concerned risk and privacy.
While there was a large amount of information on named employees, there was even more data on patients. Apart from listings of named patients who had tested positive for COVID-19 (lists that were seemingly be sent to the Florida Department of Health), two folders that Conti allowed DataBreaches.net to view were particularly concerning. One directory contained more than 1.47 million files that appeared to be scans of patient appoint/service records from 2013-2015.
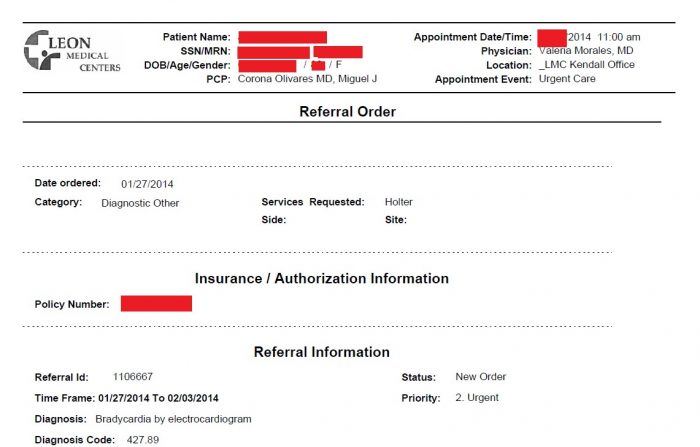
Files in this directory contained the patients’ first and last name, their gender, their age, date of birth, date and time of appointment, referring physician’s name, provider’s name, and the reason for a visit or appointment, with insurance/authorization information in some cases. In some files, patient photos also appeared.
In addition to the almost 1.5 million of these types of files, another directory contained almost 300,000 files that covered 2009 – early 2019, where the files appeared to be scans of referrals or test orders, often with handwritten notes on them. Photos of patients were also included on some of the files, as were SSN.
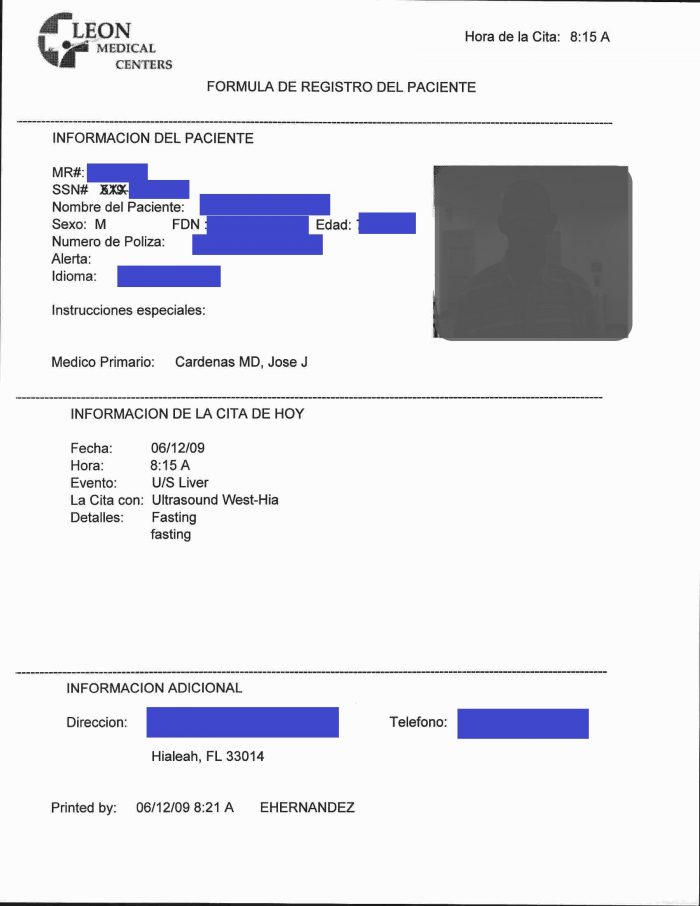
A few other folders contained an additional 25,000 files with patient information.
When this breach was first made public by the threat actors, LMC claimed that Conti’s claim of 1 million patients was a gross exaggeration. Conti’s claimed numbers may be somewhat of an exaggeration, and DataBreaches.net did not attempt to deduplicate all the files by patient name, but it seems like this is a breach that may impact at least hundreds of thousands of former and current patients as well as employees.
What DataBreaches.net saw did not see, however, unless I managed to miss it, was evidence that Conti acquired patients’ full EMR. Nor did DataBreaches.net see any massive files with health insurance-related records Did Conti acquire those? DataBreaches.net does not know, but for the patients’ sake, hopes that they didn’t.
In any event, exact numbers aside for now, this is clearly a significant breach that will necessitate notifications to former and current employees and former and current patients as well as HHS. It will also require LMC to deal with all their exposed bank, credit card, and payroll-related accounts. And yes, they will need to remind/retrain employees about the kinds of targeted phishing or social engineering attacks that can now be more tailored or convincing because Conti acquired and dumped information on their executives and employees.
When HHS investigates, and I suspect they will investigate this one, there are a lot of questions to explore. With all the files that were dumped, and all the folders and files that dealt with Risk, including workers comp issues, OSHA, and other safety and privacy-related files, what DataBreaches.net did not find was any HIPAA-mandated risk assessment. Perhaps this site missed it, or perhaps it’s on another system or server that Conti did not access or make available to DataBreaches.net. But HHS will likely want to see how LMC inventoried their patient data assets and how they assessed risk to those assets and then addressed the identified security risks, and when they addressed known vulnerabilities and risks. And I’m guessing a lot of employees and patients are going to want to know that, too.
DataBreaches.net reached out to LMC last night to inform them that this site would be reporting on the data that had been made available for preview and to ask for a statement if LMC wished to make one. No response has been received by time of this publication. This post will be updated if a response is received.