The Twitter account of a researcher known on Twitter as @ido_cohen2 is gone and their DarkFeed.io site has an “under maintenance” notice for the past day. According to a source, they have been scared away for good. Have they been?
Over the past months, DataBreaches.net has occasionally been contacted by someone who appears to be a Russian threat actor. Some of the info offered by this individual has not seemed credible, but some of it has been, and a recent interaction may have predicted what happened in the past 24 hours.
On April 12, this source mentioned “ido_cohen2” to me in a Telegram chat. They (the source) informed me that someone was going to pay someone to use EDR requests on Twitter to get researchers’ account information. In the following transcript, DD is “DissentDoe.” I’ve redacted the source’s name.
[Redacted]: if ur using a personal email on twitter
[Redacted]: might wanna change it 🙂
[Redacted]: same with phone
[DD]: why?
[Redacted]: you know this monkey
[DD]: Someone going to hack me?
[Redacted]: twitter.com/ido_cohen2
[Redacted]: ? he is getting a visit to his house
[DD]: What does that have to do with me?
[Redacted]: ur a researcher
[DD]: Yes.
[Redacted]: so theres ur answer
[DD]: So your asshole affiliate is going after all researchers?
[Redacted]: hint
[Redacted]: 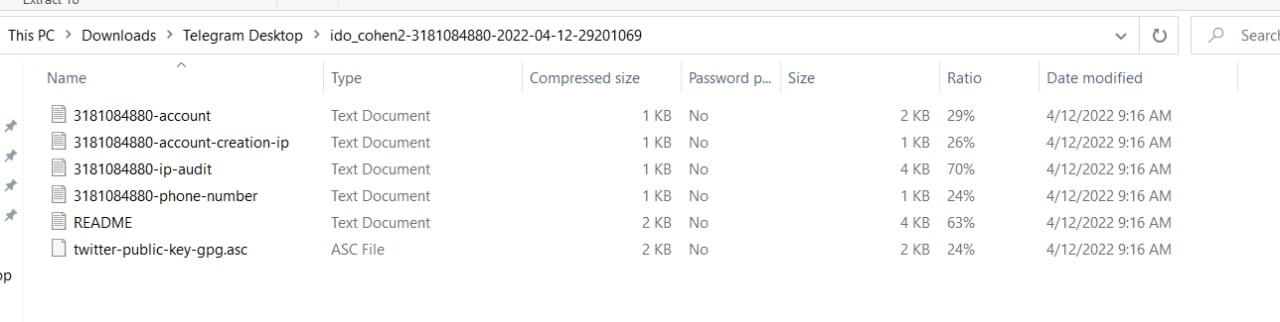
[DD]: (pardon my language)
[Redacted]: 😉
[DD]: I only use my domain/work … which are public.
[Redacted]: ok good
[Redacted]: twitter subpoenas ?
[Redacted]: idk why the affiliate is paying someone to do them
[DD]: Do you have any idea how many times Twitter has been subpoenaed about me? LOL….
[Redacted]: yes 😀
[Redacted]:so it doesnt matter for u
[Redacted]: know any researchers
[Redacted]: who need to be unmasked
This morning, the same source messaged me:
[Redacted]: your friend @ido_cohen2
[Redacted]: was scared away ?
[Redacted]: he is gone for good
This was not the first time, though, that ido_cohen2’s username came up in the context of some threat actors really hating him. When DataBreaches reported on a scam letter allegedly drafted by Groove, this site did not report the researchers’ names that they used. One of them was ido_cohen2’s Twitter identity. DataBreaches reached out to him at the time to alert him that scammers might be using his name as part of their scam.
So… has ido_cohen2 really been scared away, and for good? We’ll see. I tend to doubt it, but it will be interesting to learn if there really was an attempt to use an EDR (Emergency Data Request) on Twitter to get researchers’ information.
This post was edited post-publication for safety reasons.
So.. I think Twitter has not received a lot of EDR request about ido_cohen2 Twitter profile, so it could be easy determinate which law enforcement operator works for cyber crime entities.. because only LE can ask for EDR.. I suppose
I think you do not understand how this works. No, law enforcement is not working for any cybercrime entity. The threat actors are filing EDR forms, posing as law enforcement agents. They are counting on the requests not being verified as carefully because of the alleged “emergency.”