MX: Jalisco Congress Attacked by Play
The Congress of Jalisco announced that it has been affected by a ransomware attack on December 6 by a group called “Play.” The attack encrypted 14 servers and some employees have received extortion demands seeking payment for a decryption key.
At a press conference, the President of the Board of Directors, Mirelle Alejandra Montes Agredano, and the Secretary General of the Congress, José Tomás Figueroa Padilla stated that most of what was affected was of a legislative, legal, or administrative nature. Investigators had not yet determined if any files had been exfiltrated or deleted. As Mesa de Redaccion reported, the officials added, “the affected files correspond mostly to public information that is already transparent and duly backed up, and that the finances and accounts of the Legislative Branch did not suffer any type of affectation.”
As of publication, DataBreaches did not find any listing for this incident on Play’s dedicated leak site.
AR: National Institute of Statistics and Census Hit with Malware
On December 5, the National Institute of Statistics and Census (INDEC) announced on its social networks that it had suffered a virus.
Its announcement on Facebook:
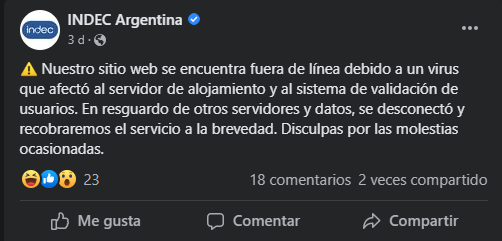
Our website is offline due to a virus that affected the hosting server and the user validation system. In order to protect other servers and data, it was disconnected and we will recover the service as soon as possible. We apologize for any inconvenience caused.
More details of the virus were reported by Infobae:
A virus was detected that was hosted in the periodic backup of the INDEC. When the scheduled backup was executed last night, the virus was activated and encrypted the virtual machine that authenticates the Institute’s internal users. In view of this situation, for security reasons, the remaining servers were deactivated until the problem was solved.
The situation was subsequently updated on Twitter:
Since last night the website is active again. We reiterate our apologies to our users for the delay because, prior to the reconnection, security tests were carried out on all systems to ensure the care of the data.
BR: Iochpe-Maxion Victim of Cyberattack
Sao Paulo-based automotive components manufacturer Iochpe-Maxion has issued a statement about a cyberattack it experienced on December 5. The translation is as follows:
… in its information information technology environment, which resulted in the unavailability of part of its systems and operations and operations in some units in Brazil and abroad. The company promptly activated its control and security protocols to contain the attack, having preventively isolated some of its systems to protect the environment.
The Company, together with its specialized advisors, is acting in a diligent manner diligent and employing all its efforts to identify the causes of the incident, determine its its extent and mitigate its effects.
The Company will keep the market informed of any relevant information information related to this event.
The company’s statement was also reported by Global Happenings. As of publication, no group has claimed any responsibility for an attack on the firm.
AR: Automovil Club Argentino Discloses Intrusion in Its Systems
Automovil Club Argentino posted a notice on its Facebook account that it suffered a network intrusion on December 1st:
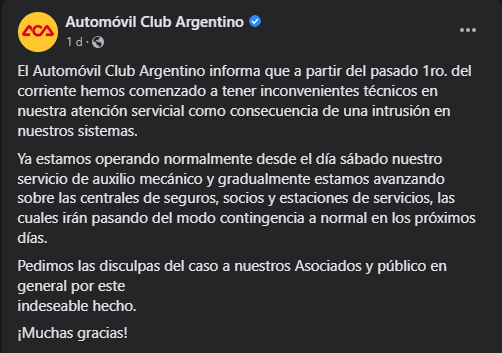
The Automóvil Club Argentino informs that as of last 1st of this month we have started to have technical problems in our service as a consequence of an intrusion in our systems.
We are already operating normally since Saturday our mechanical assistance service and we are gradually advancing on the insurance, members and service stations, which will be changing from contingency to normal mode in the next few days.
We apologize to our associates and the general public for this undesirable event.
Thank you very much!
AR: Cetrogar Hit by Ransomware
The Argentinian retailer of technology, household items, and appliances has reportedly been affected by a ransomware attack at the beginning of December. The identity of the attackers and any ransom demand have not been disclosed.
It appears that customers have experienced some inconvenience and are angry. Minuto De Cierre reports:
The home appliance chain has no operating system, even though it has been hacked for at least four days. Customers who, unaware of the issue, go to Cetrogar, receive for their purchases handmade invoices, which can generate problems with future warranties and even tax evasion.
There does not appear to be any notice on their web site or social media accounts. Earlier today, Play ransomware group added a listing to their leak site that does not name their victim but from the location, appears likely to be Cetrogar. The threat actors claim they will be publishing data on December 17 and that files include employee documents, passports, fingerprints, and agreements.
ES: Attack on Ayuntamiento Requena Claimed by BlackCat
On November 28, Requena City Council, Valencia issued a resolution saying that they had suffered a cyberattack on November 27 that encrypted user data and required them to turn off their system. A copy of their full resolution can be found at Revista Local.
The Levante news site provides additional details, including the fact that the cybercriminals demanded $500,000 in BTC. The outlet notes that the servers had been paralyzed for 10 days by now, “including the payroll payment system, and the 200 officials have only been able to collect part of their salary.”
The BlackCat (ALPHV) ransomware group has claimed responsibility for the attack and has already leaked a number of files.

DataBreaches sent some inquiries to Requena City Council by email but received no reply. DataBreaches also contacted BlackCat via Tox. Of note, in responding to DataBreaches, BlackCat’s spokesperson denied that the group had demanded a payment of $500,000 in BTC. Because Levante’s reporting seems to indicate that the ransom note had asked for more but had made some comment that they would settle for $500,000, DataBreaches is following up to try to get clarification from BlackCat as to what their demand actually was. This post will be updated if a reply is received.
Editing by Dissent. This post was edited post-publication to remove statement that ALPHV claimed to have more than 2 TB of data from Requena.