A new listing on ransomedvc claims, “We have successfully breached the District of Columbia Board Of Elections and have gotten more than 600k lines of USA Voters.”

The listing links to a sample consisting of one registered voter’s data. That listing included a number of fields with, but not limited to, VoterID, registration date, voter’s last name, middle name, and first name, partial SSN, driver’s license number, telephone number, date of birth, postal address, political party affiliation, email address, and polling place. DataBreaches was able to confirm that it accurately matched the DCBOE’s database for that voter by using the board of election’s verification process.
That voter registered in 2022. DataBreaches requested a sample from any voter who registered recently, but was not provided one by press time.
Like many other boards of election, D.C. voter registration lists are publicly available. Anyone can acquire a copy of the D.C. list for $2.00. But also like many other areas, some fields are not publicly available to everyone. The $2.00 doesn’t buy you all the data types in the ransomedvc sample. The following entry is from the National Conference of State Legislatures and shows access to state voter registration lists and what fields are kept confidential:
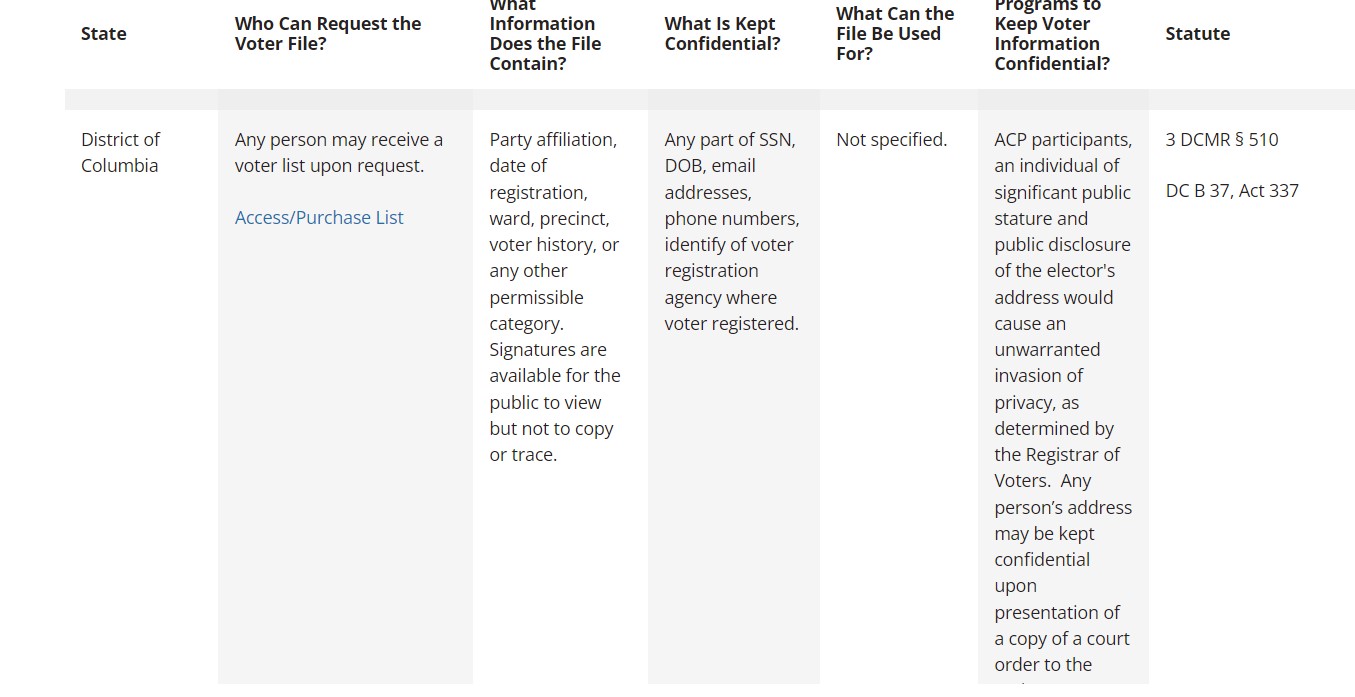
So did ransomedvc gain access to a database with some confidential voter registration information? Yes, and a spokesperson for ransomedvc tells DataBreaches that the reference to 600k lines is because each line is a complete voter record. When DataBreaches recently examined the BOE’s monthly statistics for 2023, it appeared that there were between 550-600k currently actively registered voters.
Ransomedvc informs DataBreaches that the data will be sold to one buyer only. The price was not publicly listed, but in October 2020, the U.S. Election Assistance Commission commented on such lists being sold and the pricing:
The price, availability, and type of data in the voter file varies state-by-state. The price of the statewide voter file ranges from $0 to $37,000. The relative availability of voter file information can be categorized as open (effectively no use restrictions), mixed (some restrictions for specific types of user groups), or restricted (some restrictions for specific types of user groups or complete restrictions for specific types of user groups). In general, even the least restrictive states prohibit the commercial use of voter file information, however the amount of PII (such as DOB or SSN) included in the voter file may remain significant and valuable to a variety of malicious actors.
With only 600k voters and not full SSN, the price for the current data set should be relatively low even though there are other types of personally identifiable information. Some prominent residents may have been able to get access to their data suppressed for safety reasons, but without the whole database available to DataBreaches, it was not possible to look at that question.
DataBreaches reached out to the D.C. BOE for a statement and was told a statement would be sent, but it was not received by press time.
The domain name was corrected post-publication to ransomedvc. It had erroneously been listed in an earlier version as ransomed.vc.
Update 1: The following statement was sent to DataBreaches by the D.C. BOE:
Washington, D.C.–On October 5, 2023, the District of Columbia Board of Elections (DCBOE) became aware that a hacking group known as RansomVC claimed to have breached DCBOE’s records and accessed 600,000 lines of US voter data, including DC voter records.
While DCBOE is still investigating this matter, DCBOE has found that voter records were accessed through a breach of the web server of DataNet, DCBOE’s website hosting provider. No internal DCBOE databases or servers were directly compromised.
DCBOE has taken the following actions during the initial phase of our investigation:
- DCBOE initiated an internal assessment and began working with its data security and federal government partners to investigate the breach. These partners include, but are not limited to, the Multi-State Information Sharing and Analysis Center (MS-ISAC), the Federal Bureau of Investigation (FBI), Homeland Security (DHS), and the Office of the Chief Technology Officer (OCTO). DCBOE is collaborating with MS-ISAC’s Computer Incident Response Team (CIRT) to resolve the issue.
- DCBOE took down its website and replaced it with a maintenance page upon learning that our website was the source of the breach.
- DCBOE conducted vulnerability scans on our database, server, and other IT networks.
DCBOE continues to assess the full extent of the breach, identify vulnerabilities, and take appropriate measures to secure voter data and systems.
It should be noted that in the District of Columbia, some voter registration data–such as voter names, addresses, voting records, and party affiliation–is public information, unless it has been made confidential in accordance with District of Columbia rules and regulations. DCBOE shares this information upon request in compliance with the law.
This remains an active investigation and DCBOE will release additional information as it becomes available.