As many people suspected, Omni Hotels & Resorts was the target of a ransomware attack in March.
Omni first described the incident as a chain-wide “outage” due to IT issues. By April 1, guests were losing patience with the “outage.” Bleeping Computer noted guests complaining online claiming that they had to send text messages to the front desk requesting to be let into their rooms, and it might take 30 minutes for someone to show up. Others complained on social media that they were spending hours or days trying to reach someone to make or change reservations.
On April 3, Omni admitted that the “outage” was a cyberattack.
Omni’s most recent update was on April 8, when they reported that they had restored systems across its portfolio of properties.
Their update page has never stated it was a ransomware attack or that they received any extortion demand.
On the important question of what types of data may have been accessed or acquired, Omni’s status page states:
We are currently working to determine the scope of the event, including impact to any data or information maintained on Omni systems. Our investigation into the incident remains ongoing and we are working with external specialists in this process.
Threat Actors Claim Responsibility
According to threat actors who have now claimed responsibility for the attack, Omni already knows what data has been exfiltrated. A spokesman for Daixin Team informed DataBreaches that the attack was launched on March 27, and a negotiator or representative for Omni entered the threat group’s chat room the next day.
“They know what data we have,” the spokesperson told DataBreaches. “They received proofs and examples of data.”
As some employees had told Bleeping Computer, some servers were restored from scratch. Daixin did not know whether some servers might possibly have been restored from offline backups.
In a listing on their leak site today, Daixin writes:
STOLEN DATA INCLUDES:
Sensitive data. (Including all records of all visitors from 2017 to the present )==== LEAK ====WILL BE SOON
They have not provided any proof of claims at this point, however.
DataBreaches has reached out to Omni to request their response to Daixin’s claim. DataBreaches has also reached out to Daixin Team to request some proof of claims and additional details. This post will be updated when responses are received.
Daixin Team was the subject of a CISA alert (.pdf) on October 22. Previous coverage on DataBreaches of their double extortion attacks on the medical sector and business sectors can be found linked here.
Update 1: It appears that in response to this site’s email inquiry (and perhaps, others’ inquiries), Omni posted another update today. This one states:
Omni Hotels & Resorts continues to investigate a recent cyberattack on its systems with the assistance of a leading cybersecurity response group. As part of this investigation, we have determined that limited information pertaining to a subset of our customers may have been impacted.
It is important to note that the impacted data does not include sensitive information such as personal payment details, financial information, or social security numbers. It may include customer name, email, and mailing address, as well as Select Guest Loyalty program information. We have reported this matter to law enforcement.
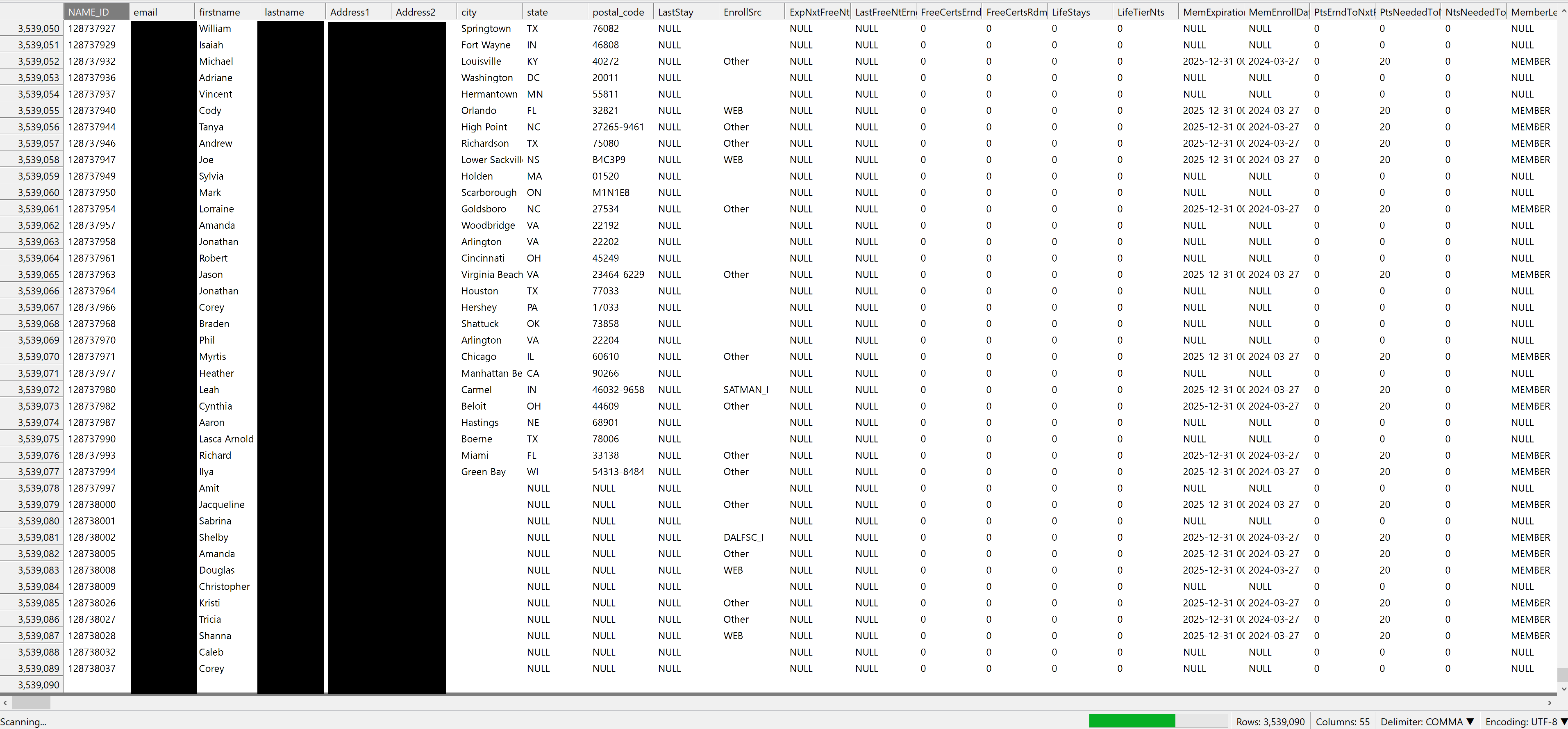
Update 2: Daixin Team responded with both data and a screenshot of alleged negotiations between them and Omni. One sample was a small spreadsheet sample with fields that included fields with: Guest_name_id, First_name, Last_name, Email, Zipcode, State, Country, Membership_ID, Membership_Level, and other fields about their last stay. DataBreaches has redacted some of the data in the screencap below:
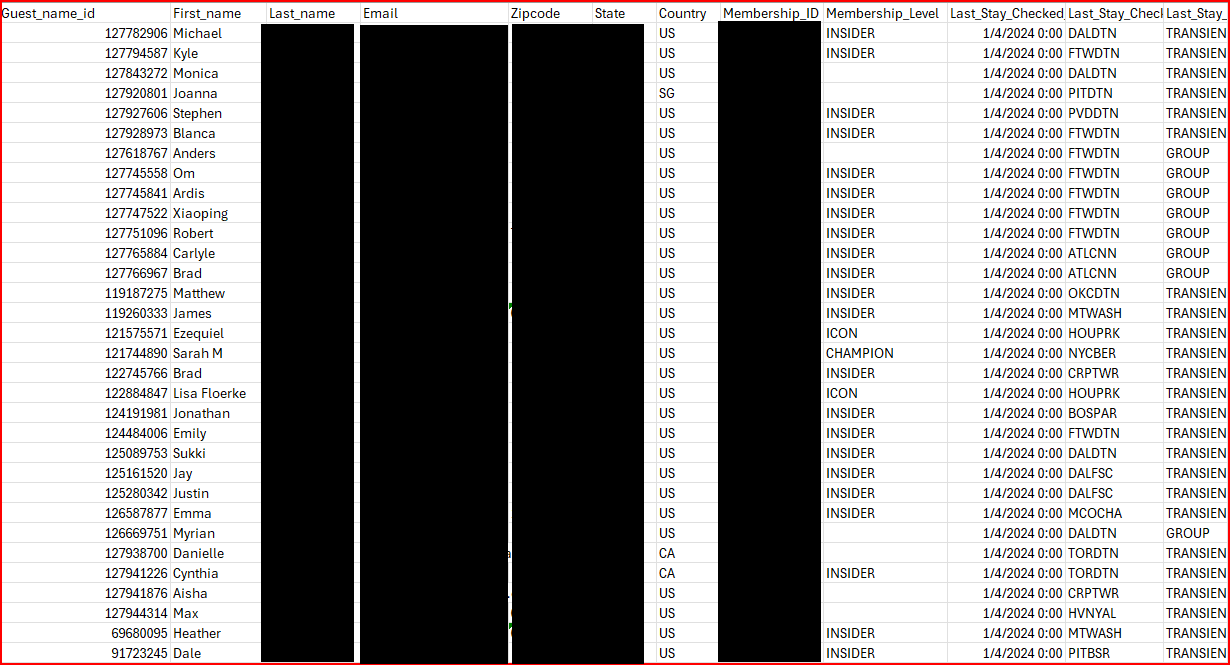
Daixin Team also provided a second spreadsheet with the same fields, but the data in the second sample was from guests who checked out in 2017. Most of these were “GOLD” level membership guests. This sample contained 10,000 rows or records. Sorting by Guest_name_id and Membership_ID found no duplicates, so these appeared to be 10,000 unique guests.
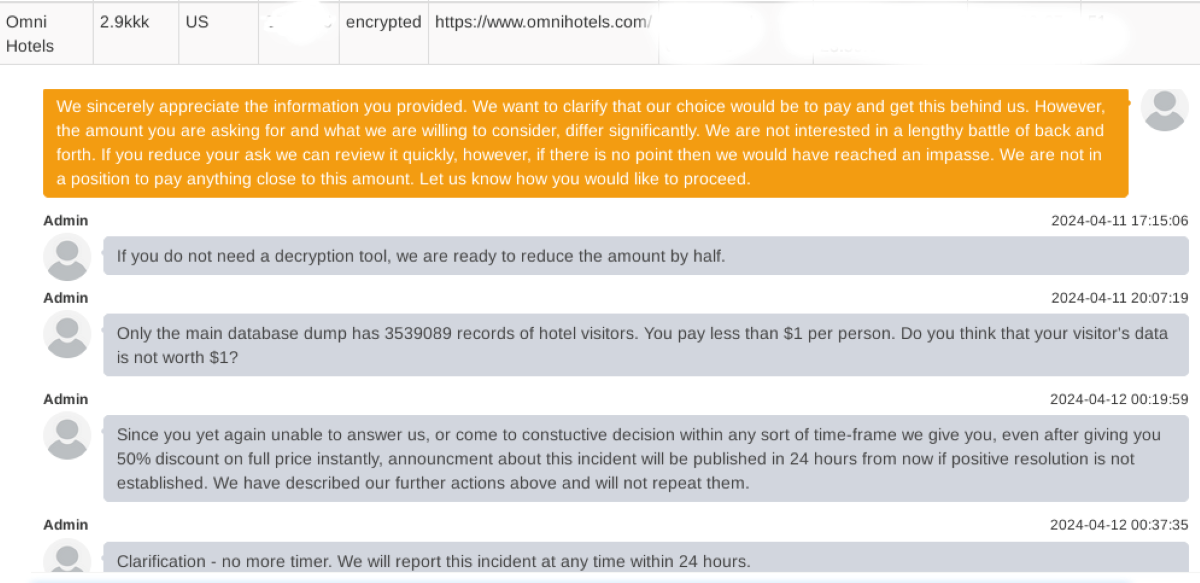
The negotiation chat snippet provided by Daixin to DataBreaches appears below. They inform DataBreaches that as of the last negotiations, they had dropped their asking price to $2 million. “They are in chat now, but they are silent, and time is up,” their spokesperson wrote to DataBreaches this afternoon. The chat log includes a statement by Daixin to Omni that the main database dump has “3539089 records of hotel visitors.”
Daixin also provided proof of the 3.5 million guest data. They provided Databreaches with 3 parts of a spreadsheet with the data. Unlike the previous two samples, these data included the guests’ postal addresses: