The individual known as “0mid16B” has been busy, it seems. They contacted DataBreaches on Wednesday to announce that they had hacked MedSave Health Insurance TPA Ltd (“MedSave”). MedSave is a third party administrator in India that partners with more than 10 insurance companies, processing and settling claims submitted by hospitals or insured members. MedSave lists 5,000 hospital networks that they work with. They are considered one of the biggest TPAs in India.
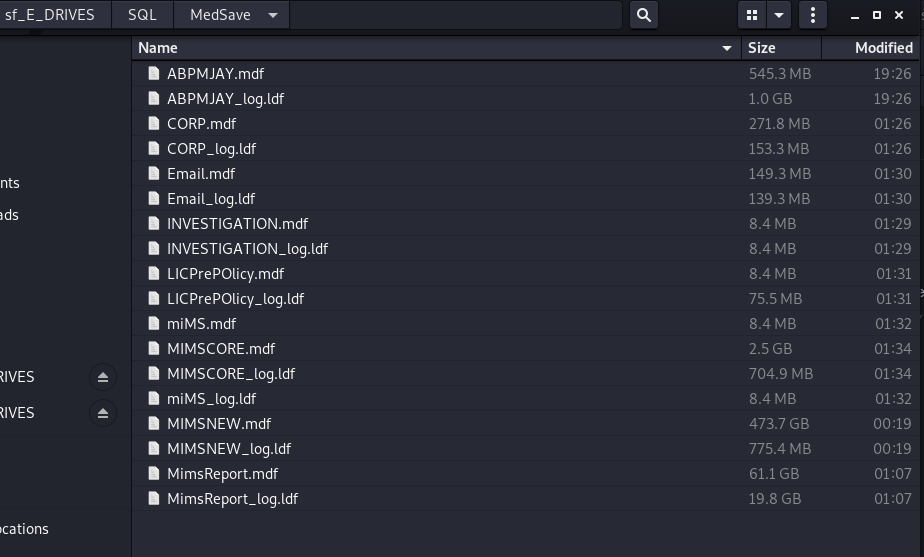
“In total, I stole 561 gigabytes of databases,” 0mid16B wrote. “Corporate, accounting, employees, sales and personal/health data of 10,617,943 people.” They attached a screenshot showing a directory of .ldf and .mdf files and several .csv files as proof of claims.
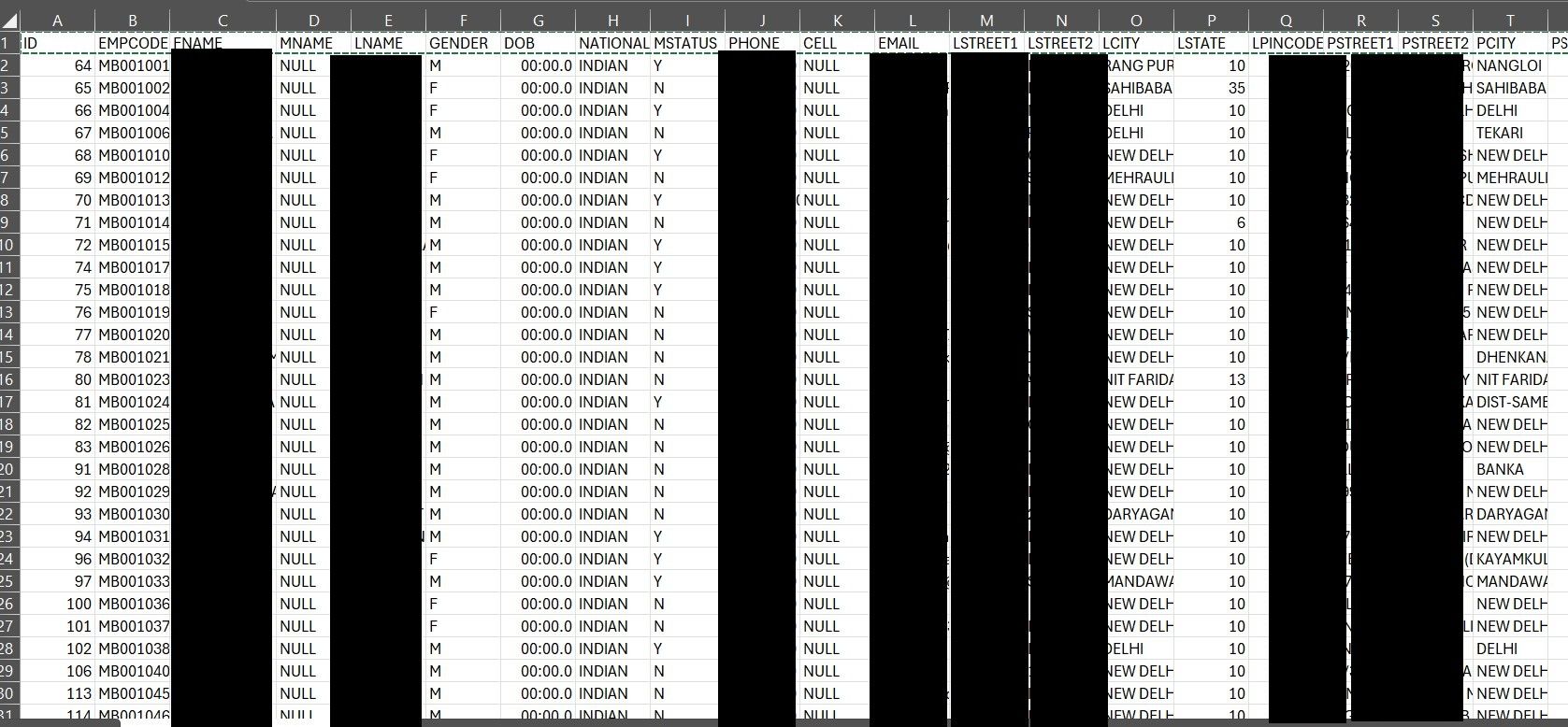
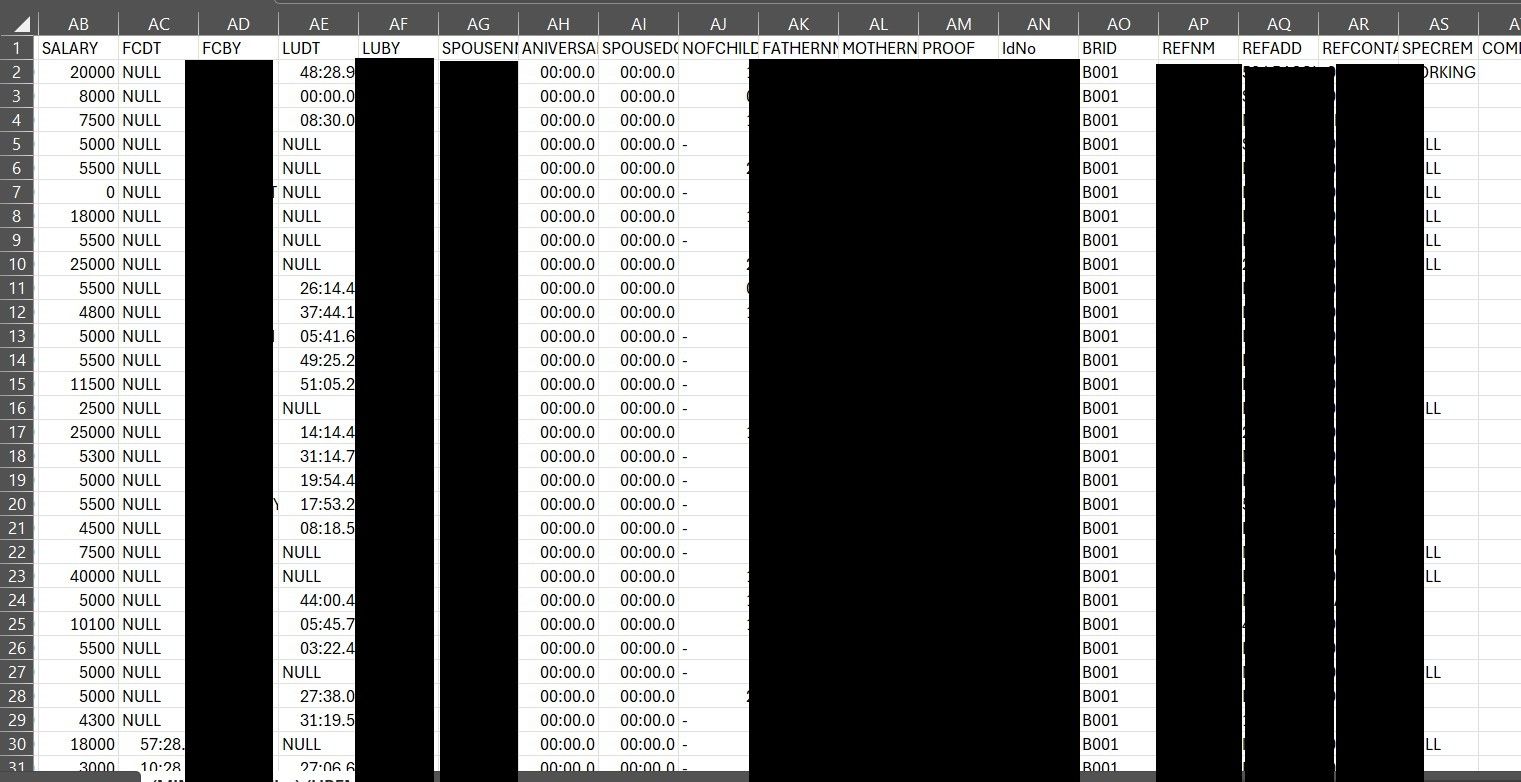
One .csv file that DataBreaches inspected appeared to contain a wealth of employee information with the following fields:
ID EMPCODE FNAME MNAME LNAME GENDER DOB NATIONALITY MSTATUS PHONE CELL EMAIL LSTREET1 LSTREET2 LCITY LSTATE LPINCODE PSTREET1 PSTREET2 PCITY PSTATE PPINCODE DESIGNATION DEPARTMENT STATUS DOJ DOL SALARY FCDT FCBY LUDT LUBY SPOUSENM ANIVERSARYDT SPOUSEDOB NOFCHILD FATHERNM MOTHERNM PROOF IdNo BRID REFNM REFADD REFCONTACT SPECREM COMPANY PHOTO PHOTOPATH IPADD REASON
Not all the fields were populated, but many were. A spot-check of some employees’ names revealed that they were executives of MedSave.
The data, 0mid16B wrote, were current as of January 8, 2025.
On inquiry, 0mid16B would not reveal how they gained access but claimed that MedSave had not detected them initially. “I still have access,” they claim, adding, “In fact, I went in and killed their system 3 times between 12th Jan to 15th Jan.”
0mid16B also did not reveal how much they demanded, but it sounds like they never even got to tell MedSave the amount. “I left a note on their server and sent them an email, but without monetary demand. I waited for them to respond for 72 hours. There was no response until today. They tried to recover the system but I killed it each time they tried.”
DataBreaches asked 0mid16B if they had any comment on MedSave’s security. They replied:
“This company served more than 10 million customers. Yet they do not even bother to have AV installed. I breached in since 31st Dec and remained undetectable until i informed them on 12th Jan. The SOP should be bringing the server offline and investigate the root of breach but this company brought it back online with the vulnerabilities still intact. Until today, i still have access. Transferred more than 560 GB of data out of their server within a matter of a few days, it should be a red flag automatically based on outgoing bandwidth, but nothing was flagged or limited in the eyes of their sysadmin.”
MedSave’s site has been unreachable, returning a “403 Forbidden” response. DataBreaches sent the firm a message via their LinkedIn account on Wednesday, telling them what 0mid16B claimed and asking if they had any comment or response. That was followed by an email to their domain email account in case email could get through.
No reply has been received by publication. 0mid16B says that they intend to sell some of the data and leak the non-customer data.
This post will be updated if MedSave responds.