
Australia has experienced a number of significant cyberattacks on healthcare entities in the past few years. Now a relatively new ransomware group, Cyclops, claims to have attacked Atherfield Medical & Skin Cancer Clinic in Australia:
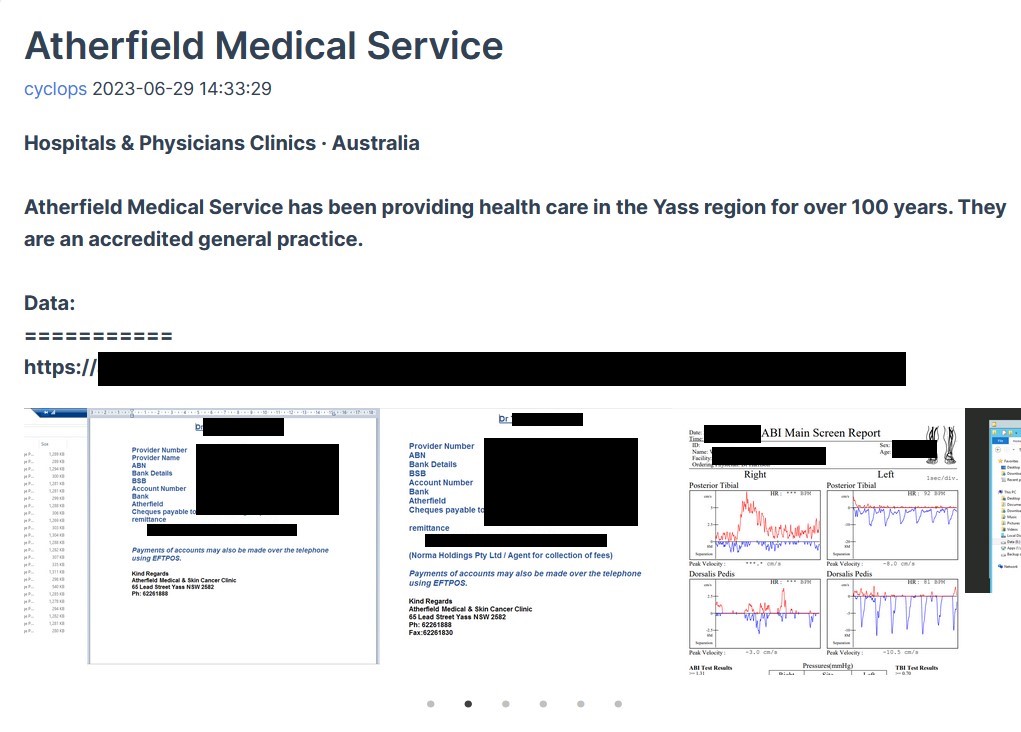
In Cyclops’ listing (above), there is a date of June 29, which appears to be the date they uploaded the data. There is a link to download files and screencaps as proof of claims. DataBreaches has redacted the link to the data.
Inspection of the leaked data revealed a lot of personal and health information of patients as well as banking details of doctors:
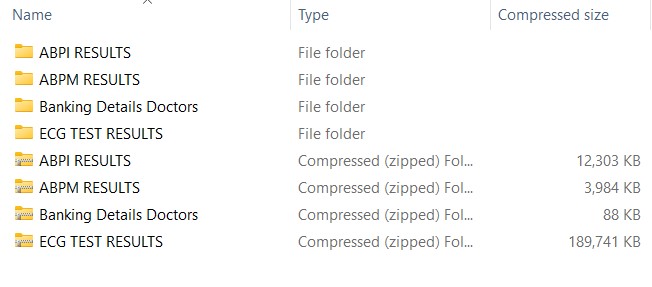
The ECG Test Results folder contained subfolders, one for each year 2020 – 2023. The filenames were formatted to have the patient’s first and last name and the date of their ECG (echocardiogram). The files were all .pdf files and were password-protected. DataBreaches did not attempt to crack the passwords to see if one password was used for all 300+ files or if there was a unique password per file. That said, just the disclosure of patient names, dates of service, and type of test would be considered a breach of protected health information under HIPAA. But this is Australia, not the U.S., and DataBreaches is not an expert on their regulations or laws. The doctors’ personal information for banking would also be a concern if the doctors still use those accounts.
DataBreaches is not sure whether the password protection on individual files was by Atherfield or by the attackers. When contacted via Qtox to ask about that, a spokesperson for Cyclops who called themself “Booda” informed DataBreaches that the attack was by an affiliate and not by CYCLOPS. On July 1, the spokesperson said they would reach out to the affiliate to ask about the individual file password protection, but they have not gotten back to DataBreaches by publication time.
Not finding any alert or notification on its site, DataBreaches emailed Atherfield on July 2 and July 3 asking about the incident. Their practice manager, identified only as Kaylene, replied today:
Good morning,
We recently experienced a cyber incident where an unauthorised third party accessed our network and took some of our data. We immediately partnered with forensic specialists and cybersecurity experts commenced an investigation to understand what happened. This investigation is ongoing.
We have also taken steps to further secure our systems.
The unauthorised third party published some data externally on 1 July 2023 which we are investigating as a priority.
We are notifying all individuals who may have been impacted by this incident, and providing steps they can take to protect their personal information.
We are taking this matter very seriously and we apologise for any inconvenience or distress that this incident may have caused.
At this point, then, it seems that this is a confirmed breach, but its scope is yet to be determined or revealed. DataBreaches will continue to monitor the situation.