A relatively new ransomware group calling themself “Gunra” has shown it has no compunction about attacking hospitals. They have reportedly locked — and have started leaking information from — the American Hospital in Dubai (AHD).
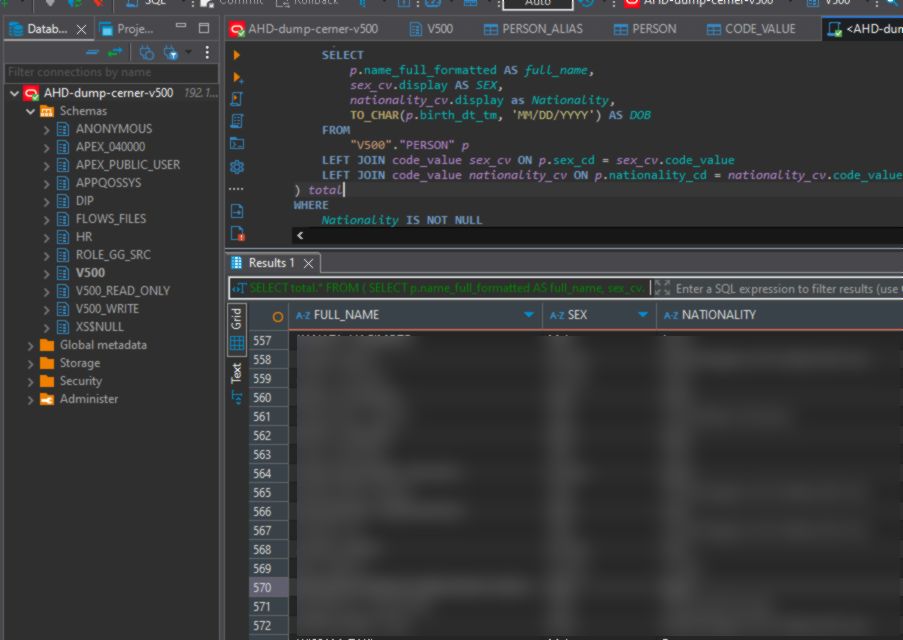
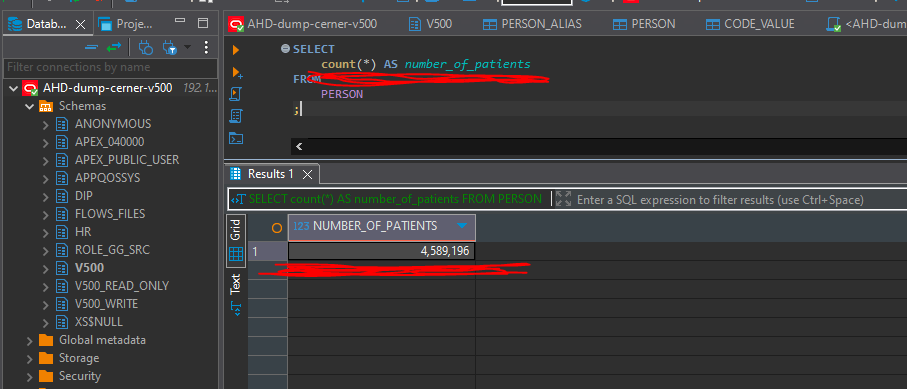
In its first listing concerning this attack, Gunra claimed to have exfiltrated the entire Cerner Millenium database (now known as Oracle Health EHR) with about 450 million patient records. Another screenshot indicated 4,589,196 patients, but it is not clear whether that would be unique patients or includes multiple records for some patients.
DataBreaches has redacted Gunra’s proof of claim to blur patient names from their screengrab. The database was reportedly 4 TB in size, and 700 GB when compressed.
DataBreaches reached out to Gunra via their Tox account to request additional details. Their spokesperson, who described themself as their client manager, was unable to answer some questions such as how they gained accessed, but was willing to provide DataBreaches with additional data, including a spreadsheet with new patient data from one service for the first quarter of 2025. DataBreaches has redacted patient names, medical record numbers, contact numbers, and treatment plan notes. Patients seen by this service was seeking or receiving fertility-related information or treatment services. Some patients were seen individually (“single”) while some were seen as couples. In some cases, patients sought sperm preservation services for medical reasons such as having cancer. The entries in this table all relate to sensitive issues of conception and health decisions individuals or couples may make.
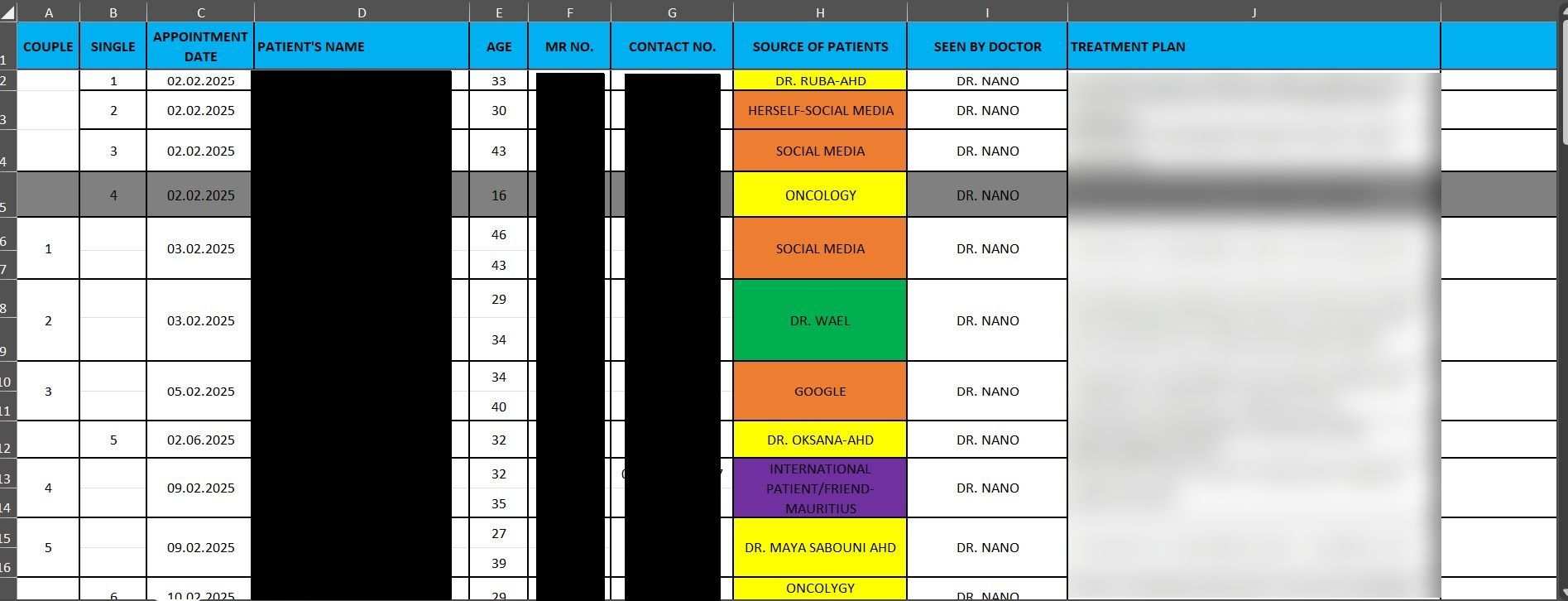
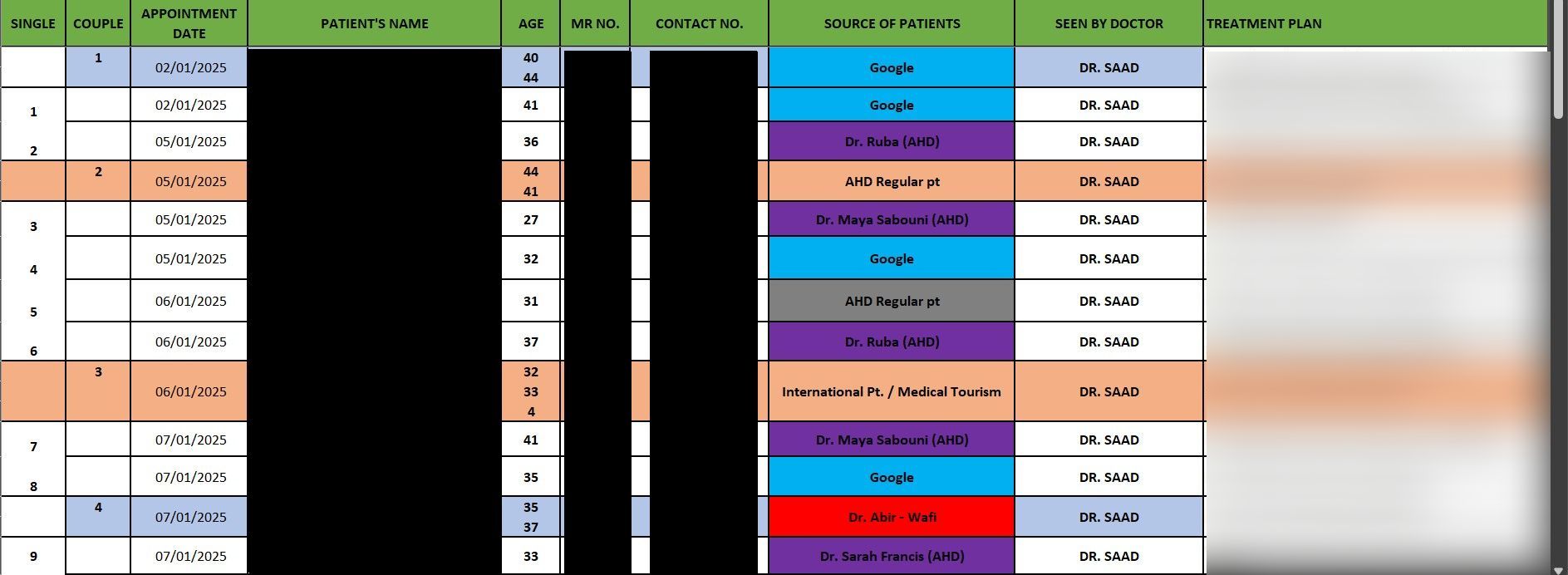
Screengrabs from patient records provided to DataBreaches.net by Gunra. Each row represents a unique appointment for a named patient or the names of both couple members. Redacted by DataBreaches.net
In response to a question from DataBreaches about whether AHD had detected Gunra’s presence and how they had responded, Gunra provided DataBreaches with an internal document dated June 1. Metadata indicate that it was authored by AHD’s Senior Manager for Clinical Systems at American Hospital Dubai and was last modified by its Senior Manager for IT Infrastructure at AHD.
The Downtime Incident document provided the following summary of the incident:
At 02:00 AM on 1st June 2025, the AHD IT team identified a critical system downtime affecting the hospital’s VMware vSphere infrastructure and EMC Unity storage systems. Upon further investigation, it was determined that the event was caused by a cyberattack on AHD’s IT infrastructure, resulting in the encryption of virtual machines and storage volumes. This incident has disrupted access to multiple core hospital systems
Systems/Assets known to be affected at that time were listed as:
VMware vSphere: vCenter, ESXi hosts, and associated virtual machines
EMC Unity Storage: Production storage LUNs; and
AHD’s Critical Services Impacted: Cerner, MyCare, LIS, Third Party Application Services and file services
The document outlined steps that AHD had already taken as well as steps to be taken. DataBreaches is not disclosing the full document so as not to interfere with any incident response plans the hospital may be implementing. But we do note that best practices for incident response include not using internal communications to communicate about a breach as attackers may be monitoring your communications. That seemed to be the case here.
Because Gunra is a ransomware gang and they did encrypt data, DataBreaches asked about any ransom demand and the hospital’s response, but the spokesperson was unable to answer those questions other than alleging that “AHD guys and CEO Sherif Beshara are fakers.” Sherif Beshara is the Group CEO of Mohamed & Obaid AlMulla Group of Companies. AHD is part of the Mohamed & Obaid AlMulla Group.
It is not clear to DataBreaches why the CEO was specifically named as a “faker,” but according to Gunra’s client manager, AHD lied to patients by claiming they are updating their IT sysems. “They seem want to hide their databreach and cyber incident,” the client manager told DataBreaches.
As proof of the coverup claim, Gunra provided DataBreaches with an internal email chain where a customer support agent indicated that a customer showed the call agent a screenshot from post on X (formerly Twitter) and stated that he was not believing AHD’s claim that current problems were due to a system update. AHD’s COO responded to the call agent’s email, with one line, “Please ignore and don’t share it.”
Once again, then, the use of internal communications when the threat actors still had access reveals information that AHD would almost certainly not want publicly disclosed this way.
“Stupid guys, their poor patients will get future incident. That’s why we will leak their CreditCard Numbers and personal private informations,” Gunra’s client manager informed DataBreaches. They have since leaked more data, although it appears to be mainly folder and filename listings of internal business type of records such as analyzing services and fees, payroll records, etc.
DataBreaches is not a lawyer and is certainly not expert on UAE breach notification law, but private hospitals in the UAE do seem to have obligations to notify regulators and patients of breaches that pose a high risk to rights and freedoms. DataBreaches suspects that they will be required to notify under UAE’s Health Data Law (Federal Law No. 2 of 2019) and the recently enacted Personal Data Protection Law (Federal Decree Law No. 45 of 2021), although how quickly they will disclose and whether individual notifications will be involved remains to be seen.
Ideally, notification should be made within 72 hours of discovery of the breach, and if it cannot be made that quickly, then the entity should explain why. By its own internal documentation, AHD was aware of the breach by June 1, although they may not have been aware of the scope and whether patient data was involved. By now, however, given that Gunra leaked data and the patient database has been reported on both social media and in news, AHD will be under more pressure to disclose or make some statement.
What may also come into play is Article 20 of the PDPL, which imposes data security obligations. If Gunra’s claims are confirmed, should AHD have been storing so much patient data without any encryption to protect it? What will regulators decide if it they investigate? Given that the new law just went into effect, this will be an interesting case to follow, although certainly, for the patients whose sensitive personal data is being exposed or leaked, this is a more serious matter.
DataBreaches emailed AHD to inquire what it was doing in response to the breach and whether any regulators or patients had been notified of the incident. No reply has been received as of publication, but this post will be updated if a reply is received.