Ransomware operators known as the Maze team have been getting media attention for their influence in implementing what is being called a double extortion scheme: attackers gain access to their victim’s network, exfiltrate data, and then lock up the victim’s system with ransomware. They then demand a fee — which may be hundreds of thousands of dollars or even more — to provide a decryption key. But even if the victim pays that ransom, the attackers still hold copies of the victim’s data which they threaten to dump publicly if the victim doesn’t pay a second fee. To increase pressure on their victims, Maze Team created a web site where if the victim doesn’t pay them within a few days, Maze names them and provides a public sample of their data for the taking. The sample may be old uninteresting data just to show proof of access, or it may be sensitive corporate or personal information.
In the past few months, a number of other ransomware operators have adopted the Maze naming and dumping data approach, including DoppelPaymer, Nefilim, Ragnar, Sodinokibi (REvil), CLOP, Ako, and Netwalker.
Like other ransomware groups using the Maze model or approach, Ako maintains a site on Tor. At the present time, there are seven entities listed on their site two from the medical sector, four from the business sector, and one k-12 school district. Not all victims are U.S. entities, and the school district in Texas does not have any data dumped, although the attackers posted a note that stolen files are “coming soon” in case of non-payment.
Perhaps some of the most sensitive data comes from a pain management practice in Massachusetts. North Shore Pain Management has two offices in Massachusetts. The Ako operators have dumped more than 4 GB of their data that includes employee and patient information. The patient records are a covered entity’s nightmare because it is all unencrypted protected health information that discloses patients’ names, addresses, telephone numbers, diagnoses, treatment codes, social security numbers, health insurance policy information, billing information, employer information, workers compensation details and much more. Most of the more than 4,000 files are not spreadsheets or databases but rather are .pdf files or scans of tabled data involving deposits, explanation of benefits statements, bank account information, copies of checks with routing and account numbers, and other correspondence.
The files dumped by the attackers are not EMR, but do contain a lot of PHI. Not all patients have the same data types exposed, but to show they mean business, Ako used an unredacted screenshot with PHI on their website’s link to them. DataBreaches.net has redacted it below:
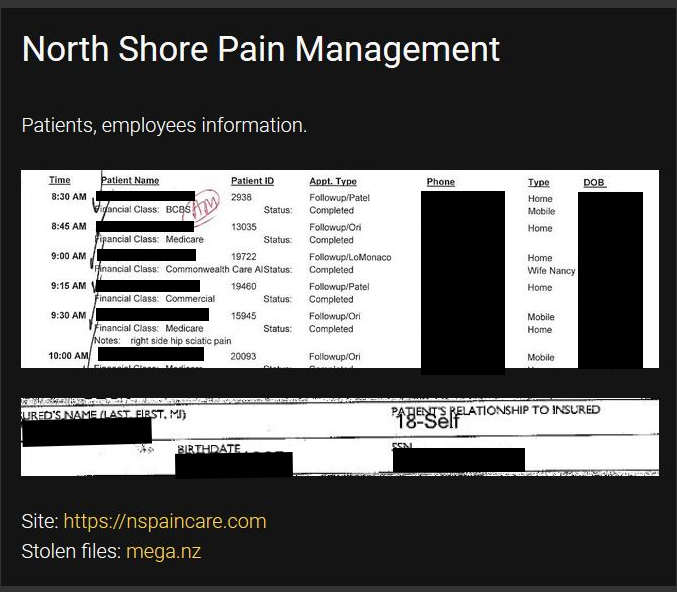
Not all of the files in the data dump were meaningful (some were image files from Wild Tangent game), but some files were quite large with significant amounts of PHI such as one file which included a number of completed insurance claim forms containing patients’ name, insurance policy number, insurer, SSN, DOB, diagnosis code, treatment code, and charges. Depending on the type of claim or case, the patient’s employer might also be disclosed with other relevant employee information. The file also contained Explanation of Benefits statements, copies of checks and other payments records, and information on appeals.

DataBreaches.net reached out to NSPAIN’s Twitter team, but did not receive a reply by publication time. At this point, then, they have not confirmed or denied any breach to this site, and based on a phone call I received yesterday from a victim of another ransomware operator, I cannot even be sure that NSPAIN knows that their patient and employee data was stolen (if it was, as it appears to have been).
This post will be updated if more information becomes available. This appears to be an incident that will require notification to HHS OCR.
Note: For an introduction to Ako ransomware, see SonicWall’s report in February and a report by AppRiver. Note that the $3,000 ransom mentioned may no longer be valid. One of Ako’s recent victims whose data has been dumped has this note on their listing:
Got only payment for decrypt – 350,000$
Payment for delete stolen files was not received.
Apparently, the attackers were not going to settle for just hundreds of thousands of dollars. They dumped thousands of records from the business including customer screening and due diligence, and other business and customer records. And of course, the implication is that if the firm doesn’t pay the other fee for deleting stolen data, it will be dumped publicly.