ROCKVILLE, Md., Nov. 24, 2021 — Supernus Pharmaceuticals, Inc. (NASDAQ: SUPN), a biopharmaceutical company, today announced that it was the recent target of a ransomware attack. The attack had no significant impact on the business and did not cause any serious disruption to the Company’s operations. The Company continues to operate without interruption and does not currently anticipate paying any ransom amounts to any criminal ransomware group.
The Company currently believes the incident began around mid-November, 2021. Based on the preliminary results of the ongoing investigation, the Company believes the criminal ransomware group encrypted certain files on the Company’s systems, deployed malware to impede access to the Company’s systems, and thereafter threatened to publish certain data copied from the Company’s systems. Upon detection of the ransomware, the Company notified government authorities, engaged cybersecurity experts and its outside law firm, and commenced its recovery process. The Company successfully recovered the impacted files and has taken additional steps designed to further protect its networks and files.
To date, the Company has not paid any ransom and has been able to restore all of the information encrypted by the criminal ransomware group.
Although to date the Company’s business and operations have not been significantly impacted by the incident, there is no assurance that further attacks may not significantly impact the Company’s business or operations and that information improperly obtained by the criminal ransomware group may not be exploited by the criminal ransomware group or other third parties. The Company will take appropriate action to protect any stolen confidential information and will continue to investigate the incident and monitor the situation going forward.
About Supernus Pharmaceuticals, Inc.
Supernus Pharmaceuticals is a biopharmaceutical company focused on developing and commercializing products for the treatment of central nervous system (CNS) diseases.
Our diverse neuroscience portfolio includes approved treatments for epilepsy, migraine, ADHD, hypomobility in Parkinson’s disease, cervical dystonia and chronic sialorrhea. We are developing a broad range of novel CNS product candidates including new potential treatments for hypomobility in Parkinson’s disease, epilepsy, depression and rare CNS disorders.
For more information, please visit www.supernus.com.
Source: Supernus Pharmaceuticals
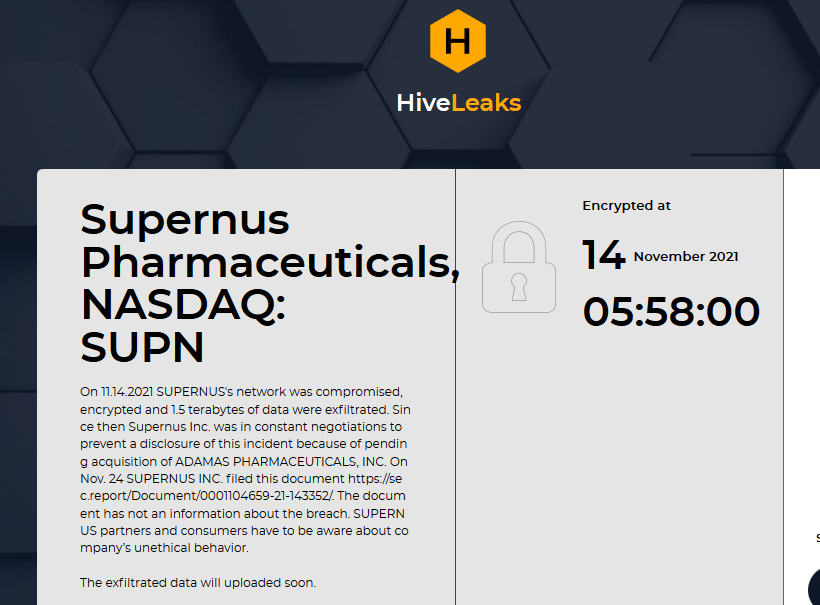
Update: This incident has been listed on the Hive threat actors’ dark web leak site. They claim to have encrypted the files on November 14 and to have infiltrated 1.5 TB of data. The rest of their statement appears incorrect in suggesting that Supernus covered up the incident from the SEC. To the contrary, Supernus issued the press release incorporated above in this post, and in its SEC filing of November 26, it pointed to the press release and linked to it. Although the threat actors claim that the firm was in negotiations with them, the firm makes no mention that it ever negotiated with them, and only mentions that it had not paid any ransom (as of November 24).