 On April 28, a new forum user on BreachForums called “Menelik” claimed to have 49 million Dell Technologies customer records for sale.
On April 28, a new forum user on BreachForums called “Menelik” claimed to have 49 million Dell Technologies customer records for sale.
The Daily Dark Web provided a screencap and details from the listing. The customer data purportedly includes data between 2017 and 2024, with “full names, addresses, cities, provinces, postal codes, countries, unique 7-digit service tags of systems, system shipment dates (warranty start), warranty plans, serial numbers (for monitors), Dell customer numbers, and Dell order numbers.”
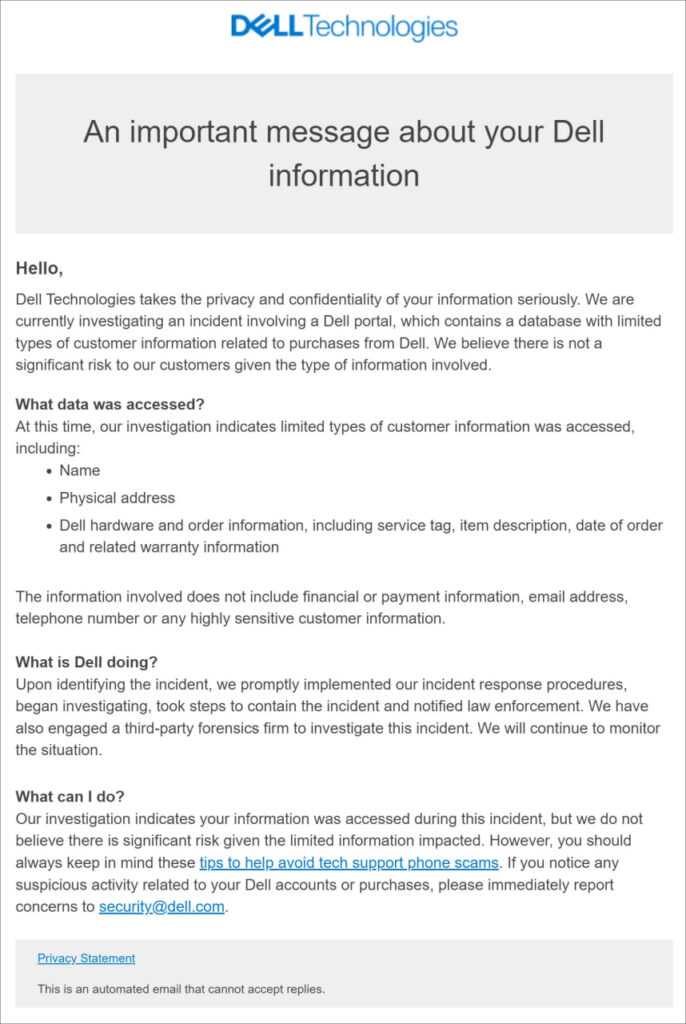
Yesterday, Dell notified customers of the incident (see screencap).
Menelik updated their listing by using Dell’s notification as confirmation of their claims and reiterated their claims about the data, specifying data types and adding:
Top 5 countries with most systems:
- United States
- China
- India
- Australia
- Canada
- About 7 Million rows of the data are individuals/personal purchases
- 11 Million are consumer segment companies
- Rest is enterprise clients, partners, educational institutions and others that I could not identify easily
They also explain the disappearance of the original thread from the forum:
My old thread was removed by Breached mods (due to expired sample link) so some people thought this data was sold.
But no, I am still the sole owner of this data. I am planning to sell it to 1 individual only.
I don’t have email/phone number for this 49 million but I do have email & phone number of some several thousand customers. All recent.
Dell’s notice (see screencap) suggests that there is little risk to customers, but recognizes that the data might be used as part of phone scams or other schemes. Dell declined Bleeping Computer’s request for more details about the incident and the number affected, telling them they “are not disclosing this specific information from our ongoing investigation.”
“Menelik” is “ShinyHunters”
The name “Menelik” may not be familiar to most people, but DataBreaches can reveal that this attack was the work of ShinyHunters. They informed DataBreaches about it at the time after being unable to get Dell to respond to them via multiple contact attempts and email addresses.
DataBreaches emailed Dell last night to ask about their policy concerning contacts by threat actors — whether they read communications but don’t respond or whether they don’t even read communications from what might be individuals who have hacked them. In that email, DataBreaches also noted that ShinyHunters informed this site that they found a second vulnerability and claimed they had already started exploiting it to exfiltrate data. They did not provide any proof of claim at this time. DataBreaches asked Dell whether if ShinyHunters contacts Dell again, Dell would read the communications.
No reply has been received by publication.
Updates: Post-publication, Dell responded:
Our program includes prompt assessment and response to identified threats and risks. We are not disclosing any information that could compromise the integrity of our ongoing investigation or any investigations by law enforcement.
Update 2: Bleeping Computer published more details about the attack and Shiny Hunters’ attempts to get Dell to respond prior to putting the data up for sale.