On some as yet undisclosed date, Doctors Center Hospital in Puerto Rico became the victim of a relatively new ransomware group calling themselves Project Relic.
To date, Doctors Center Hospital (DCH) has not responded to inquiries sent to it by DataBreaches on November 11 and November 12, and their email appeared to be out of service when DataBreaches first attempted to contact them via email. No notice appears on their website, and DataBreaches could find no public notice about the breach. On November 9, however, DCH notified HHS that 1,195,220 patients had been affected.
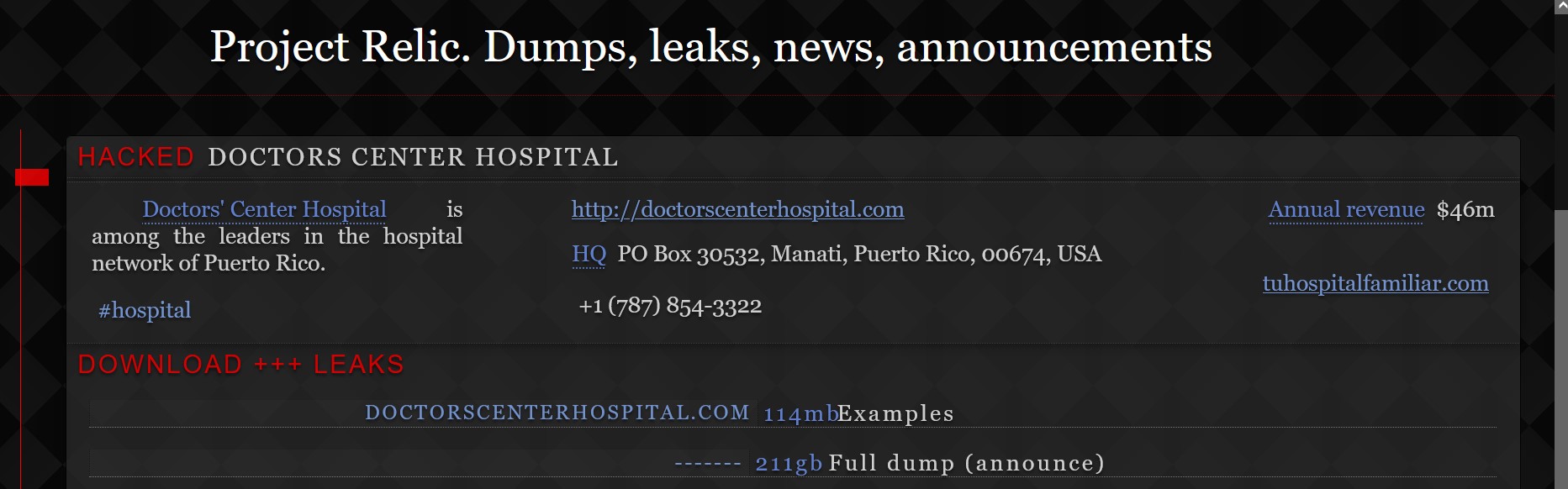
For their part, the threat actors have already leaked 114 MB of files from what they claim are 211 GB of files that they exfiltrated. Inspection of the sample revealed a number of internal files of the hospital system as well as some files specific to named employees. Other files contained scans of named patients’ medical notes or records.
Not much has been written at this point about Project Relic, who presumably took their name from gaming. But BlackPoint has some information on them shared by a client who was a Project Relic victim. According to BlackPoint, Project Relic ransomware is written in Go. Like other groups, they use a chat application to negotiate with their victims and a leak site where they dump data of those who do not reach an agreement with them. Their ransom note, a sample of which is included in BlackPoint’s whitepaper, indicates that they steal, encrypt, and delete sensitive files of the victim. Payment is demanded in bitcoins.
BlackPoint writes, in part:
The methods used to deploy the malware and steal the data are unknown. The customer’s IT managed service provider (MSP) collected several artifacts and shared them with Blackpoint’s Adversary Pursuit Group (APG) for analysis. Relevant artifacts include a Microsoft Installer (MSI) file, a Dynamic Link Library (DLL), and screenshots of the specific commands used to spread and execute the DLL across the network.
Their full report with technical details can be requested on their site.
This post will be updated as more information becomes available about this specific incident.