More than two months after Fortra first began notifying clients that threat actors had exploited a vulnerability in GoAnywhere, many patients whose protected health information was stolen may still have no clue. In Part 1, we noted six entities that have disclosed the breach. Five of them are listed on Clop’s leak site with their data being leaked to pressure them into paying extortion. Their disclosures generally do not include any statement about patient data being leaked on the dark web. In Part 2, we list eight U.S. entities and one Canadian entity that do not appear to have publicly disclosed this incident, even though protected health information may already be leaking on the dark web.
HHS was asked to comment on these large third-party file-transfer breaches. Their comments appear at the end of this article.
MedMinder
MedMinder has not issued any press release or public notification concerning the incident and did not reply to this site’s inquiry of March 11. In a statement to TechCrunch last month, the prescription delivery and management service indicated it was “aware of the allegations” but declined to comment further while the company was investigating. DataBreaches sent Medminder a second inquiry on April 18, but still received no reply.
Clop claims to have Medminder files that they describe as “Technical documentation. PDF, png files, xlsx databases. Data files in “godrive” goanywhere`s folder.”
Inspection of the limited data Clop has leaked in this first part appeared to be internal data and not protected health information (PHI), but we have yet to see what is in other parts.
Homewood Health
Homewood Health offers inpatient and outpatient mental health treatment and support services. Numerous entities in Canada contract with them for employee assistance programs. DataBreaches has sent Homewood Health two email inquiries about the Fortra/GoAnywhere incident but has received no reply, despite the fact that their website says, “For any media related inquiries, please get in touch with us. We’ll be happy to answer any questions you may have.”
Clop claims to have acquired a lot of personal or protected health information:
“Xls, csv files – name, last name, email, date of birth, department of employee. Csv files – reports of client activity on the website, log files of the chatbot. PDF – statistical reports, xls files – lists of buyers, company names and policy numbers, financial reports. PDF – individual cases (short-term loss of operability) – name, last name, address, date of birth, phone numbers, place of work. JPG – photos of employees on documents, photos from different events. Photos of different documents (driving license, vaccination). Presentations.”
In this first part of their leak of Homewood’s data, Clop leaked detailed files, including:
- files that each contain dozens of pages of reports on Teknion employees whose names had been redacted;
- files that each contain dozens of pages of reports on Conestoga College employees whose names were not redacted; and
- screencaps of case summary reports from Oncidium.
Other screencaps contained some personal information about employees.
Allied Benefit
Clop has leaked some data from Allied Benefit and claims to have acquired:
FTP servers by the names of medical companies. Pdf, Csv files – payments for medicines: name, last name, ID, amount, name of drugs). Reports, databases with people’s names and addresses. Database of medical companies: name, address, phone number, billing address, Tax_ID. Employee databases: name, address, phone, email. PGP encrypted files. Password protected archives.
Inspection of the leaked data did reveal folders for .ftp servers for clients.
CloudMed
CloudMed is a revenue management business associate. Clop claims to have acquired:
Customer databases of different hospitals: name, address, SSN, phone number, insurance name, insurance diagnosis name, doctor’s name. Log file, which contains login, hash passwords, name, phone, email, users and what files were put through the site.
The limited data that Clop has leaked so far does not appear to contain PHI, but it does document transmissions over the file transfer system. It is not clear how many more parts or data leaks there will be for this entity.
Tropical Texas Behavioral Health
Tropical Texas Behavioral Health was also added to Clop’s leak site, but without any details other than just a “Coming Soon” message. There is nothing on the mental health and substance use treatment provider about any breach and no submission on HHS’s public breach tool.
Clop’s listing doesn’t indicate whether TTBH was part of the Fortra incident. Emails sent to TTBH on April 16 and 19 have received no reply.
[UPDATE of April 28: TTBH responded that the concern was about employee data, not patient data, and Fortra eventually notified them that no data was accessed. As of today, Clop still has the empty “Coming Soon” text with their name.]
Multiplan
Clop often adds a statement to many victims’ leaks: “The company doesn’t care about its customers, it ignored their security!!!
In Multiplan’s case, Clop went much further:
Example of company and criminal board interested delay inevitable. This company negotiate with only one purpose, to delay announcement after their quarterly reports. They do not value all of 3TB of their data that soon you have here. Investors should ask big question of this company board. Why you did not tell market of this situation before results? who is criminals and they must held to account for market manipulation.
The first part of the data leak for Multiplan was in 32 parts, which may be a reflection of Clop’s frustration with that particular victim. The figure below shows a redacted version of the directory of folders that Clop has already leaked. Each folder was for a different provider or health plan.
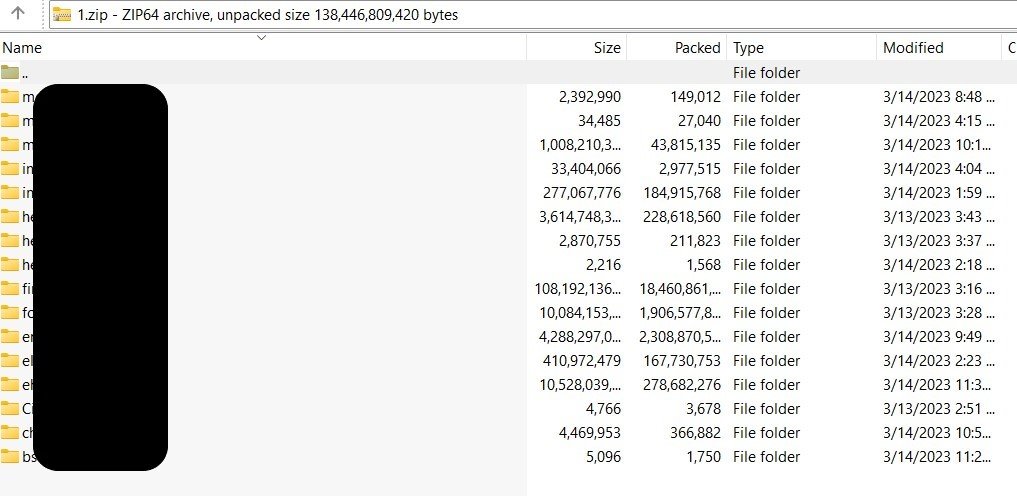
Clop does not indicate how many more updates there will be for each victim entity.
Alivia Health
Alivia Health in Puerto Rico has not provided any notification and has not responded to emailed inquiries of March 11 and April 16.
Clop claims to have acquired “Pdf, xlsx, png, jpeg files.” The first data leak for Alivia was allegedly files in their GoAnywhere\documents_20230202\ directory. None of the files in the small leak could be definitively linked to Alivia or to any patient data, though. We will have to see what future updates include.
ITx
ITx (Intellihartx LLC) is another revenue management company. Clop claims to have exfiltrated:
CSV, XLSX files – payment bases for medical services: date, amount, company name, account balances. Customer databases: name, address, phone, date of birth and SSN, income level, marital status, field of work, brand of car. Invoices.
The screencaps posted do indicate that Clop acquired files related to medical claims, including one screencap of a listing of patients with past due balances and steps taken to collect payment from them.
Updated June 9: Intellihartx LLC reported this to Maine as affecting 489,830 patients of its clients.
MedExHCO
MedEx works with the workers’ compensation industry. The first part of Clop’s leak was in 49 parts and is still being reviewed by DataBreaches. Clop claims to have acquired:
Forms of accounts: name, last name, phone. Databases of supplier companies: company name, phone and other data. Databases of people: name, last name, address, date of birth. Confidential letters with the history of treatment/operations. Pdf files with personal data: name, last name, address, date of birth, last digits of SSN. Xlsx databases of doctors providing their services: name, last name, address, phone number, tax_id, in some databases the last 4 digits of the SSN. TIF files – billing documents for medical insurance with all personal data, including the full SSN codes.
A directory listing from their FTP directory, redacted by DataBreaches, reveals the names and IP addresses related to some of their clients.
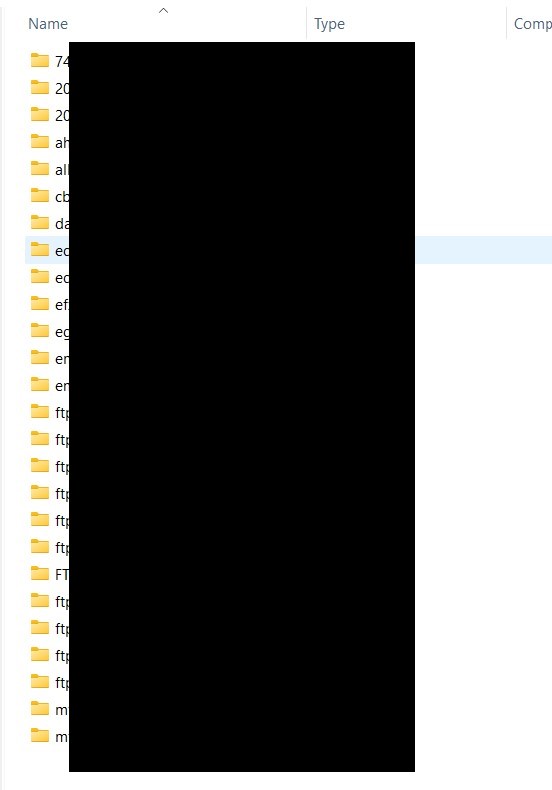
MedExHCO did not respond to an email inquiry from DataBreaches.
Comments
If Clop is attempting to extort some of Fortra’s clients, as appears to be the case, will they also try to extort these companies’ clients? Many of these entities are third-party service providers who collect and use protected health information from numerous companies, health systems, and/or health insurance plans. Where does the attempt to extort stop?
But an immediate concern is the lack of timely notification. It is now more than two and a half months since Fortra discovered the breach and started notifying its clients. HIPAA-covered entities are required to notify patients and HHS of breaches no later than 60 calendar days from discovery, but Fortra clients who were notified at the beginning of February may or may not have had enough information to determine who needed to be notified. Some entities may have had contracts calling for Fortra to make any notifications in the event of a reportable breach, but their failure to answer questions or issue any statement by now, combined with Fortra’s refusal to answer questions about whether it is making notifications to HHS on behalf of any clients is concerning. Patients’ protected health information and employees’ personal information are been leaking on the dark web. Do they know they are at risk? They shouldn’t first be first finding out from the media.
It is possible that one or more of these entities may have made notifications but DataBreaches could just not find them or they did not respond to our inquiries. It is also possible that there are more HIPAA-covered entities that have been affected that we do not yet know about at all.
So how many patients, total, will be affected by this breach? We already know about 1 million from the CHS/CHSPSC report. How many more will there be when we finally get numbers?
If anyone has received any notification from the entities listed in this post or any other healthcare-related entity affected by the Fortra breach, please email a copy to FortraBreach[@]databreaches.net or contact us via Signal at +1-516-776-7756.
HHS Comments
The Fortra/GoAnywhere breach is the second big third-party breach involving a file transfer service that Clop has hit in the past few years. The first was the big Accellion breach where Clop also attempted to extort Accellion’s clients and leaked data on their leak site if the clients would not pay.
DataBreaches reached out to HHS with some questions. The first related to how HHS responds to these large third-party breaches: does HHS actually
investigate each victim’s risk assessment and security prior to the breach, or
do victims of multiple-victim incidents like these tend to get less
investigation and scrutiny than a single-victim breach?
HHS answered:
Once OCR initiates an investigation following a breach report, OCR collects evidence through interviews, witness statements, requests for data from the entity (including business associate) involved, site visits, or other available, relevant documents. Covered entities and business associates are required by law to cooperate with complaint investigations and compliance reviews.
So all of the covered entities and business associates should be prepared for HHS to investigate their security and their incident response, including the timeliness of their disclosure and notification.
DataBreaches also asked HHS whether given that there have now been two big breaches involving file transfer software or systems getting breached, will HHS be suggesting any new approaches to file transfers to better protect PHI?
HHS answered:
HIPAA regulated entities should ensure that their risk analysis considers all the potential risks and vulnerabilities to the electronic protected health
information (ePHI) that is held and the security measures in place to protect it. Network servers are the most common location for a large breach of ePHI.OCR has highlighted this trend in large breach reporting, published guidance on file transfer protocols, and announced the resolution of completed HIPAA investigation on this issue. Compliance with the HIPAA Security Rule requirements not only is the law, but necessary to protect the privacy and security of individuals’ health information. Please see the links below for more information:
2021 Report to Congress on Breaches of Unsecured Protected Health Information
2019 settlement of breach on FTP server
OCR’s October 2016 Cybersecurity Newsletter:
Mining More Than Gold, focused on exploitation of FTP servers, including FTP services available on network-attached storage (NAS) devices
Thanks to HHS for reminding us of these resources.
Correction: In preparing this article for final publication, the subsection on MedExHCO was accidentally omitted. It has now been inserted, post-publication.
Update of June 19: Reports of affected healthcare entities continue to emerge. This week we learned that the Toledo Medical Center was one of the Intellihartx clients affected by the breach. We also learned that almost 14,000 Vermont Blue Advantage and another 2,250 Vermont Blue Advantage insured members living out of state were also affeced.