DataBreaches probably sounds like a broken record after six years of calls for more transparency in breach notifications. Sadly, the situation has gotten worse in the past year. Not only do entities fail to admit they suffered a ransomware attack, but they fail to inform patients if the patient’s protected health information was leaked or is freely available on the internet.
Yesterday, the Institute for Liver Health LLC, doing business as Arizona Clinical Trials and Arizona Liver Health (“ALH”) issued a press release about a “data security incident.” Their statement indicates that they had no idea they had been attacked until law enforcement contacted them on January 30 to tell them that their name had shown up “in a part of the internet used by criminals as an entity whose information may have been taken by a criminal.”
DataBreaches had noticed a listing on LockBit3.0’s site on January 29. Perhaps law enforcement also saw it and notified ALH. DataBreaches had contacted ALH about LockBit’s listing on January 29, but ALH did not reply. DataBreaches also contacted their systems administrator via LinkedIn at the time. He, too, did not respond.
ALH’s investigation found that an unauthorized third party accessed ALH systems “for a limited period” and obtained some files. Their statement did not reveal when the attack occurred or how long the attackers had access. The types of information involved varied by individual but included “date of birth, financial account number, and medical information, such as diagnosis/conditions; lab results; medications; treatment information. For a limited number of individuals, driver’s license number/government identification number may also be involved.”
Quick notification to HHS…. but what about patients?
On February 1 — two days after law enforcement contacted them — ALH notified HHS and reported that 1,277 patients had been affected.
On March 30 and 31 — almost two months later — ALH posted a notice on their website and press release that did not explain the gap between their discovery of the incident and their public statements.
Did ALH mail the 1,277 affected patients notification letters on February 1? Did they send letters this week? Neither the press release nor the website notice mentioned notifying patients by mail. What they state is:
We have arranged for Cyberscout through Identity Force, a TransUnion brand, to provide individuals who have been impacted by this incident with one year of complimentary credit monitoring. …
To find out if you have been impacted by this incident, please call us at 1-800-405-6108. If we confirm that your information was involved, we will provide instructions on how to enroll in the complimentary credit monitoring services over the call. The deadline to enroll in the complimentary credit monitoring services is June 29, 2023.
DataBreaches read their notice a few times. Was it just an unintended omission not to state that letters had been mailed or were being mailed, or have they put the responsibility on patients to call them to ask if they were affected? The latter would be unacceptable. The only patients who should be calling to ask if they are affected are those who did not receive a notification letter and fear they might be affected.
The phone number they give patients to call with questions opens on Monday.
The LockBit3.0 listing

LockBit3.0 added Arizona Liver Health to its leak site on January 29, as shown above. The ransom demand was listed as $150,000.00.
The following screencap shows that LockBit3.0 gave ALH 13 days to pay their demand. Their listing included nine screencaps as proof of access to ALH’s system. No patient data was posted as part of the proof, but a redacted excel sheet with AHL infrastructure information was included. The listing also had a price menu: $5,000 to extend the deadline to pay by 24 hours, $150,000 to delete all the data from their server, or $150,000 to download all the data.
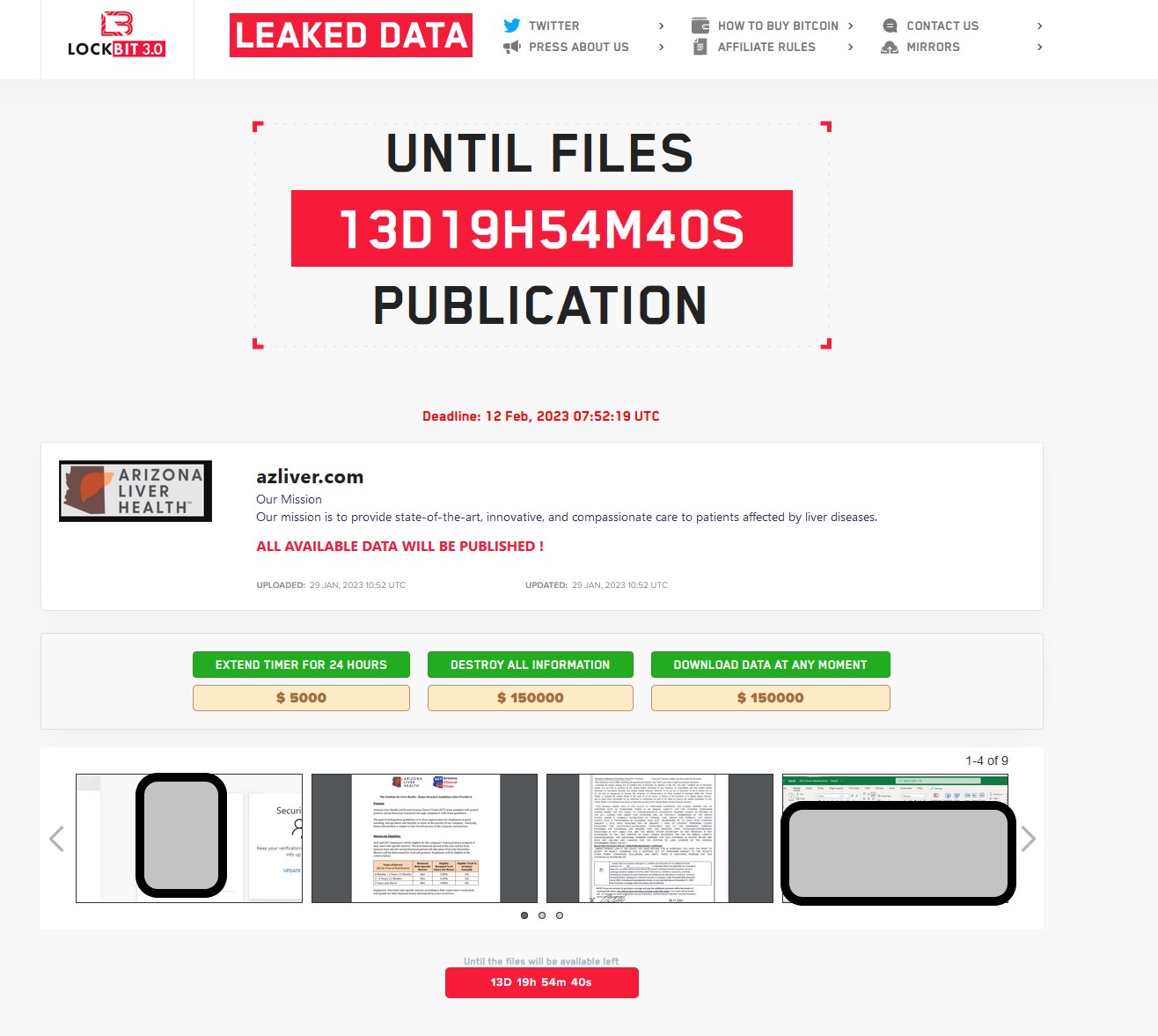
What happened next, you wonder? We are unsure because ALH’s notice and press release never mentioned any ransom situation. DataBreaches can report that the listing disappeared from LockBit’s leak site at some date unknown to DataBreaches. If LockBit3.0 ever dumped any patient data, DataBreaches did not spot it at the time, and none of the sites that track or report breaches seem to have ever spotted a data dump from this victim.
So did ALH pay LockBit’s demanded ransom? Usually, listings are only removed when someone pays.
But even if ALH paid to get the data deleted, shouldn’t patients know that there is no way ALH can be sure that the criminals didn’t keep a copy of data that they could later sell or misuse? Have the patients been given enough information to assess their risk of harm so they can take steps to protect themselves?
If anyone has received a notification letter from ALH, please share a copy with DataBreaches.net. And if any patient calls their call line and asks whether ransom was paid or what happened, please let us know their answer.