UPDATE 9-21-2016 Over the past two days, DataBreaches.net provided the First Bank of Ohio with samples from two files that “Fear” claimed were from them. They have firmly denied that either file is theirs:
These have nothing to do with us. The second group are businesses that are applying for liquor licenses in Ohio.
The second file they are referring to is the file that had been mentioned in my first post on the claimed hack, below. The newer file is a file “Fear” has described elsewhere as “Ohio_transactions_2016.csv.”
So once again, “Fear’s” claims have been refuted.
CORRECTION and UPDATE (Sept. 20):
In reporting on the claims of a teenager known as “Fear,” this site noted what he had claimed and what he could back, but also noted where he had not provided any proof of claims. In fact, the headline had the word “claims” in it specifically because not all statements were proven.
Following publication of the article, this blogger continued trying to get @hackinyolife to provide more proof of his claims. Late last night, Fear began providing more documentation. A review of what he provided indicated that in some cases, he either did not understand what he was looking at, or had flat-out misrepresented some things. As one example, he had never specifically mentioned Neustar in talking to this site, yet when other journalists contacted him to follow up, he told them he had hacked them. He admitted to this site last night that he had not hacked Neustar.
After a lengthy chat with Fear last night, and after looking at the additional materials he provided last night, it also seems clear that he did not obtain any prescription monitoring database from Florida. While there was information pertaining to medical professionals, it was mostly information that would be publicly available such as in license verification, although the state’s public portal did not reveal all the fields that were in the underlying table (e.g., practitioners’ addresses, phone numbers, and email addresses would not be shown in the public results although they were in the state’s records).
DataBreaches.net informed Fear that it would be issuing a correction to its story and would be reporting that he didn’t have what he had claimed to have. It now appears that he has issued a statement that he calls “The Truth:”
hello, media, hackers, pentesters.
Today I will be revealing the truth.
I did not hack Neustar, i lied to media to troll them.
I hacked into 38 government ftp servers, and had access to states data.
The bank breaches included has nothing to do with my breach on the ftps.
I gained access to the banks because i breached north dakota bank back in early 2016.
I had access to gov banks in each state. So i used it to troll the media.Yes, the government did get hacked, along with social security numbers from the back, tax papers, voting data.
But Neustar was a mirage to troll the media.
What really happened (SUMMARY)
-United States banking server with known gov banks was breached. (100million SSNs, maybe more.)
-Government FTP servers hacked via exploit, not neustar.
-30+ .US and .gov domains were hacked via exploit.@hackinyolife
-F
Fear’s newest claims were not backed with any proof of some of the claims above. He only provided this site with one screenshot with a few SSN that is unlikely to have come from any of the servers he claims to have breached.
At this point, then, DataBreaches.net believes that even though Fear did provide some evidence of hacking servers associated with states and did obtain some data, and although he had previously provided evidence of a hack involving the Bank of North Dakota, specific claims he made about the new hacking should be treated with extreme skepticism if not outright rejection.
DataBreaches.net apologizes to its readers for having provided inaccurate information.
Original post:
Sad to know .us domains are so unsecure
A private message to DataBreaches.net on Saturday evening was the prelude to a young hacker downloading tremendous amounts of data from states.
Over the next few hours, a teenage hacker known to DataBreaches.net from his past hacking activities would remind us once again just how insecure everything was, showing this blogger samples of files that he obtained in a hack that not only gave him access to every state with a domain on .us, but also to some .gov domains such as the U.S. Department of Education.
When asked how he obtained access, he replied:
I gained access to an ftp server, that listed access to all the ftp’s on .us domains, and those .us domains were hosted along with .gov , so I was able to access everything they hosted, such as, public data, private data, source codes etc…
He declined to reveal what .gov sites, other than USED, he was able to access, but did expand a bit on his previous answer, telling DataBreaches.net:
It was very simple to gain access to the 1st box that listed all the .us domains, and their ftp server logins. I went through each and every one, it was legit. I am pretty sure about every person who does security researching can do this, yes, it may have took me about 3 hours or 4 hours or looking around, but it is still possible.
Encryption was no obstacle for him, he said, because he saw no evidence that encryption was used at all: “I was able to read all of it in plain text form.”
As he acquired files, the teenager commented in a private chat on what he was obtaining: Social Security numbers in one file, credit card numbers in another, postal and email addresses and phone number of Minnesota school board candidates in another, web-banking transactions from the First Bank of Ohio, and more, he claimed.
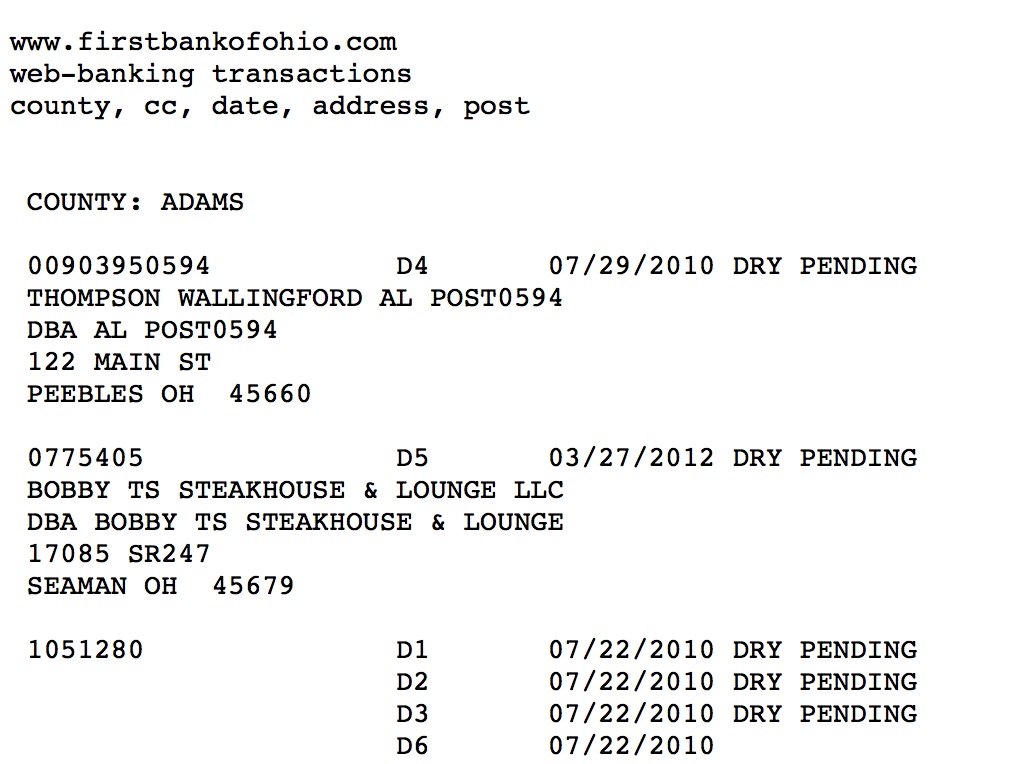

The hacker seems to have paid particular attention to Florida. Just one file alone from Florida had 267 million records, another had 76 million, he told DataBreaches.net.
“i just got access to a total of Social Security’, 101087939 numbers,” he claimed at another point, without indicating which state it was from.
i have been wget one state for like an hour lmao
has like
prob
400 mil
entries in total
When asked, the teenager, who prefers to be called “Fear,” claimed that he was also able to acquire voter registration databases. Although such databases are publicly available in many states, there has been growing concern about their too-easy accessibility and the risk that a hacker could tamper with the lists to corrupt the election process. Ironically, on Thursday, US-CERT issued an advisory on securing voter registration data in the wake of some highly publicized hacks.
Fear (also known as @hackinyolife on Twitter) claims that he was also able to access Florida’s pharmacy prescription monitoring program that is used for law enforcement purposes, telling DataBreaches.net in chat:
they had monthly reports on every citizen in Florida, and it included phone, address, name, SSN.
On inquiry, he noted that those records also contained the medication names and corresponding prescription numbers, but declined to provide any screenshots as proof.
Although he hasn’t done any counts yet, Fear estimates that he has already acquired a couple of thousand credit card numbers and millions of Social Security numbers.
When asked whether he was also acquiring state employees’ personnel information such as salary information, bank account numbers for direct deposit, etc., he replied that he was able to get phone numbers, addresses, names, and positions, but “sadly, not bank information.”
As to his intentions, Fear tells DataBreaches.net that he is dumping small portions of private data: “I’m still analyzing each file to make sure to separate private from public.”
When asked if he had any message for the states and .gov entities he had been able to access, he replied:
5 char passwords won’t save your boxes lmao
Nor, apparently, were some steps taken on Sunday to secure the data. At one point, Fear informed DataBreaches.net he had just tried to login but “they took the entire .us ftp server down.” Florida’s site was available again shortly after that, he reported, but it was now password-protected.
Too little, too late, though, it seems, as Fear told this blogger:
too bad they dont know its backdoored lOL…. they legit suck at security
According to Fear, he did not leave backdoors for other states – only Florida. That backdoor was removed last night.
A lot of damage can be done with 13 hours of access to a lot of states, though.
This story will be updated as more information becomes available.
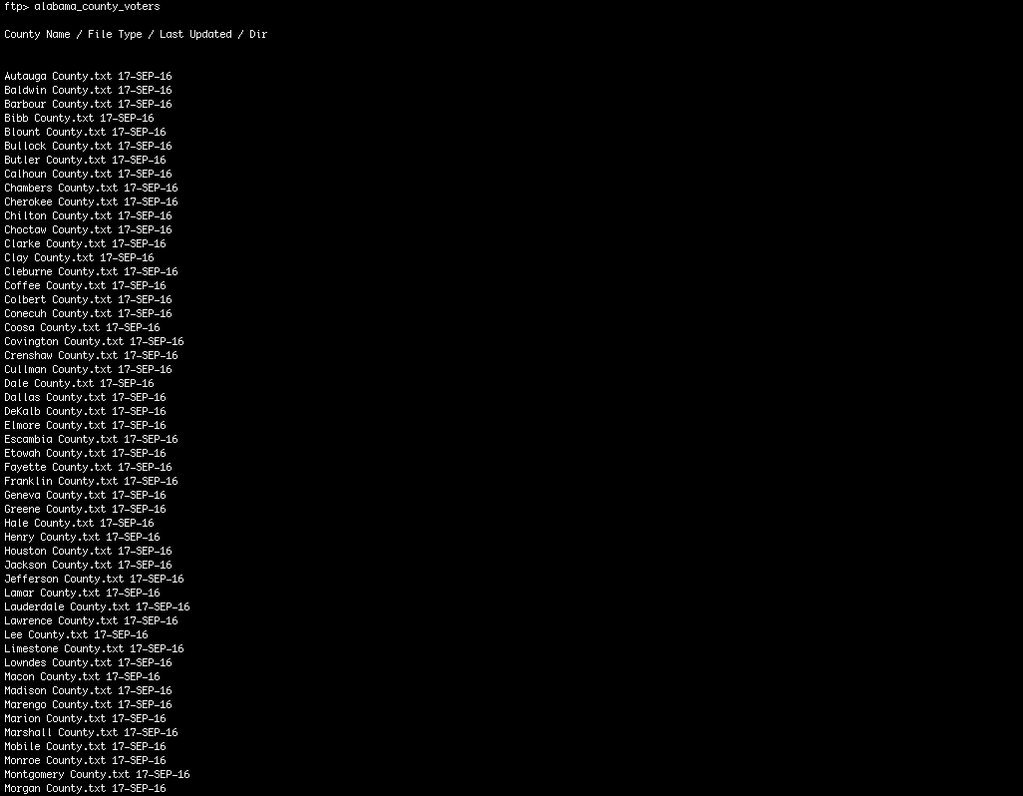
CORRECTION: A previous version incorrectly captioned a screenshot as reflecting Washington data. The screenshot was from Alabama.
You may want to double check the image of affected counties, “Listing of WA county files related to voter registration data. ” This doesn’t appear to be WA state; a quick search found these counties in AL.
Thanks. I had been looking at different screenshots and captioned that one incorrectly. Fixed it now.
I’d be interested in hearing what law enforcement people think about your “live” contact with a hacker during an ongoing breach. If you are contacted by authorities, such as FBI or some state attorney generals, do you have the legal resources to protect yourself?
Good question. I hope I don’t have to find out. I do have a lawyer who advises me/represents me on First Amendment issues, but I don’t think I’ve ever put your question to him.
As Joseph Cox of Motherboard recently articulated, journalists generally do NOT have an obligation to report crimes to law enforcement or to share information with law enforcement. That’s not our job. I am not encouraging anyone to hack anything or anything more than they are already hacking. I am simply asking them to explain what they are doing and what they are obtaining – and to request that they show me evidence of same for reporting purposes.
Could law enforcement try to raid me to get my notes or any files I obtain? Sure, they could try, but then we’d have a real First Amendment fight that would likely go on for years.
So how does law enforcement feel about what I do? I have no idea. If you ask them and they answer you, let me know. I can’t imagine that they’d be deliriously happy, but then again, they’re probably getting information from my reporting that they can and will use if they ever pursue a case against someone.
“phone numbers, addresses, names, and positions”
You can get this simply by doing an information request directly at the agency. It’s public information.
The file was a table from their server, though, and the information was not publicly viewable from the corresponding portal.
Sigh…. Attention whore, much?
More likely an attempt to generate interest/suggest authenticity to boost sales.